
Imagine the horror: Monday morning at the office, and you find out someone has stolen all your company's private data. Not only that, but they have also managed to breach your security measures, blocking you out, helpless to regain access.
The stakes? Your customers' trust, your reputation—all on the line. That's a week start no business can afford. And sadly, it's the sad reality that has led to the downfall of several businesses.
A company willing to dance with such risks - no matter how small or big - jeopardizes not only its financial stability, but also its candidacy for achieving compliance. The consequences extend far beyond a mere monetary setback: they include the loss of clientele, a diminished prospect for expansion, loss of trust, and the painstaking journey to rebuild what was once secure.
This haunting possibility highlights the importance of Penetration Tests —a proactive approach that empowers organizations to unveil and rectify vulnerabilities before they morph into gateways for malicious invaders.
In this blog post you’ll learn all the basics about Penetration Testing:
- What is Penetration Testing?
- Penetration Testing vs Vulnerability Assessment
- Types of Penetration Tests
- Penetration Testing Methodologies
- Penetration Testing Steps
- Penetration Test FAQs
- Get Help Running Penetration Test
What is Penetration Testing?
At its core, a Penetration Test, or pen test, is a simulated cyber-attack aimed at identifying and exploiting vulnerabilities in your network, systems, and applications.
Think of it as a digital stress test for your defenses - a proactive measure to discover weaknesses before actual cyber marauders can. It's crucial to assess your security posture and validate your security controls. A 3rd party penetration testing service will provide you with an independent and objective assessment of your internal and external vulnerabilities (identify doors you’ve left open for cyber-attacks), as well as recommendations on how to fix them.

Penetration Testing vs Vulnerability Assessment
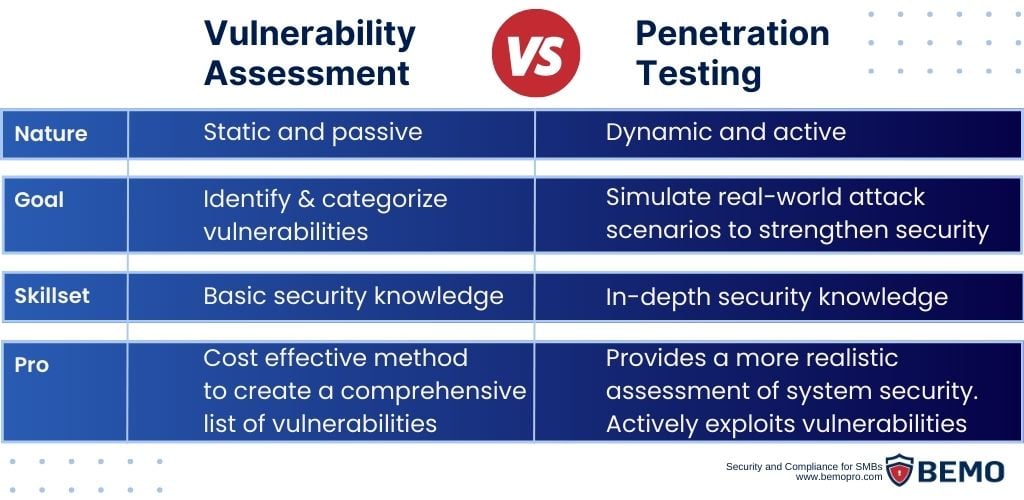
Before delving into the nitty-gritty of pen testing, it's crucial to distinguish it from its close relative, the Vulnerability Assessment. While both assessments share the noble goal of bolstering cybersecurity, they dance to different tunes.
Penetration Testing is a simulated cyber-attack aimed at identifying and exploiting vulnerabilities in a system, mirroring the tactics of potential hackers. It's like staging a controlled siege on your digital fortress to unearth weak points before malicious actors can exploit them.
The emphasis here is not only on identifying vulnerabilities, but also on actively probing and exploiting them to assess the system's resilience.
Imagine hiring a skilled locksmith to test the security of your home by attempting to pick the locks, bypassing alarms, and accessing sensitive areas. The locksmith, in this case, plays the role of a simulated attacker.
In contrast, a Vulnerability Assessment focuses on identifying and categorizing vulnerabilities within a system without actively exploiting them. Think of it as creating a comprehensive map of the cracks in your walls—knowing where they are, but not actively testing their resilience. It's a crucial step in understanding potential entry points and weaknesses, but it lacks the dynamic, real-world simulation of a Penetration Test.
It’s like using a home security system to scan your property for potential vulnerabilities, such as unlocked windows or weak doorframes. The system flags these weaknesses without attempting to breach them.
Types of Penetration Tests
Knowing the different types of penetration tests is crucial for a few reasons. First, each type focuses on specific aspects of security, allowing organizations to identify vulnerabilities in different areas of their infrastructure. This comprehensive approach ensures that potential entry points are thoroughly examined.
Second, cyber threats evolve, and attackers employ various tactics. Understanding the diverse range of penetration tests helps organizations stay ahead by proactively addressing vulnerabilities before malicious actors can exploit them.
Moreover, different types of penetration tests simulate real-world scenarios, providing insights into how various attack vectors could compromise security. This knowledge allows organizations to strengthen their defenses, implement targeted security measures, and enhance overall cybersecurity resilience.
Let's dive into the different types of pen tests:
- Network Penetration Testing: Involves evaluating the security of a computer network; this includes anything from routers, workstations, firewalls and servers, to identify vulnerabilities and potential exploits. For example, a tester might employ scanning tools to identify open ports, misconfigurations, or weak authentication protocols within a corporate network.
- Web Application Penetration Testing: Focuses on assessing the security of web-based applications like browsers and plugins. This test aims to uncover vulnerabilities in the application's code, logic, or configuration that could be exploited by attackers.
- Physical Penetration Testing: As given by its name, it tests the vulnerability of physical controls like cameras or locks. Testers might attempt unauthorized entry into a facility, bypassing access control sensors, or exploiting weaknesses in physical security protocols. This type of testing provides insights into vulnerabilities that go beyond digital realms, such as data centers or office spaces.
- Social Engineering: Social Engineering Penetration Testing involves manipulating individuals within an organization to gain unauthorized access to sensitive information. It assesses the susceptibility of employees to deception and manipulation. Testers may pose as trusted entities via phishing emails or phone calls to trick employees into divulging confidential information or clicking on malicious links. This type of testing addresses vulnerabilities related to human behavior and user awareness.
- Cloud Penetration Testing: Evaluates the security of cloud infrastructure and services. It aims to identify vulnerabilities in configurations, access controls, and the overall cloud environment.
Penetration Testing Methodologies
Penetration Testing can take different routes to simulate an attack. Each serves distinct purposes in evaluating an organization's security posture from various perspectives, ensuring a comprehensive assessment.




Black Box Testing: The Blind Approach
In Black Box Testing, the tester approaches the system with no prior knowledge of its internal structure or workings. This method mimics a scenario where an external threat, devoid of any insider information, attempts to exploit vulnerabilities. It provides a realistic simulation of an attacker probing the system without any specific insights.
White Box Testing: The Informed Assault
Contrasting with Black Box Testing, White Box Testing involves a tester with complete knowledge of the system. Armed with detailed information about the architecture, vulnerabilities, and potential weaknesses, this approach allows for a strategic and targeted assault. It mirrors scenarios where an insider or a well-informed external attacker seeks to exploit the system.
Gray Box Testing: The Partial Insight
Gray Box Testing takes a middle ground, where the tester possesses partial knowledge of the system. This approach reflects situations where attackers have some insider information but lack a comprehensive understanding of the system's intricacies. It aims to capture the nuanced reality of a partially informed attacker navigating the digital landscape.
Purple Teaming: Collaborative Test
Purple Teaming is a collaborative approach that brings together both offensive (Red Team) and defensive (Blue Team) security teams. The first trying to breach in and the second, attempting to stop them from doing so.
Unlike traditional penetration testing, which often involves a one-sided simulated attack, Purple Teaming gives real-time feedback between both teams, emphasizing teamwork, communication, and learning about advanced threats and cybersecurity tools.
The goal is to not only identify vulnerabilities, but also to work together in real-time to understand, address, and enhance the organization's overall security posture.
Penetration Testing Steps
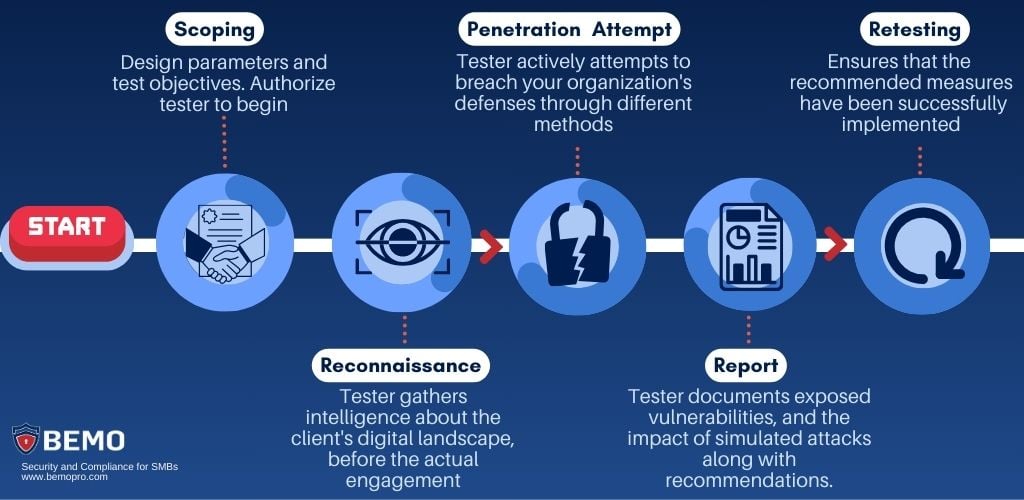
- Scoping: Here, the parameters, objectives, and limitations of the penetration test are meticulously defined and signed in a contract. For the pen tester, this phase is crucial not only for understanding the boundaries within which they operate, but also for obtaining legal protection.
By clearly defining the scope, the tester ensures that their actions are authorized and align with the client's expectations. This phase serves as the legal groundwork, establishing a framework that shields the pen tester from legal repercussions while hacking into the client's systems.
- Reconnaissance and Scanning: Once the rules are set, the reconnaissance or scanning phase kicks in. Here, the pen tester gathers intelligence about the client's digital landscape. Tools and techniques are employed to identify potential vulnerabilities, entry points, and weaknesses.
It's a digital reconnaissance mission, providing a panoramic view of the terrain before the actual engagement. The information gleaned in this stage lays the foundation for the subsequent penetration attempts.
- Penetration Attempt: With the lay of the digital land understood, the penetration attempt phase unfolds. This involves actively attempting to breach your organization's defenses, emulating the tactics of a cunning hacker.
The goal is not only to gain initial access but also to maintain it, mirroring the maneuvers of a skilled infiltrator. The tester can attempt different attacks: moving funds, stealing credentials, bank account information or customer’s data. Damaging your social media reputation, deleting, changing, or stealing intellectual property, etc.
This phase is the heart of the penetration test, where vulnerabilities are exploited, and the resilience of your systems is put to the test.
- Report: Following the penetration attempt, the focus shifts to the report phase. Here, the pen tester meticulously documents the findings, vulnerabilities exposed, and the impact of simulated attacks.
The report serves as a comprehensive record of the cybersecurity battlefield, providing you with insights into your system's strengths and weaknesses. It includes actionable recommendations for fortifying weak points, patching vulnerabilities, and enhancing overall cybersecurity posture.
- Retesting: The final phase, retesting, involves circling back to the battlefield after recommended changes have been implemented. This phase validates the effectiveness of the security fortifications made based on the initial findings. It ensures that the recommended measures have been successfully implemented and that the system now stands resilient against known vulnerabilities.
Retesting is a crucial step in the continuous improvement cycle, providing assurance that you stand strong against advanced cyber threats. That is why, at BEMO we offer two tests per year, one to identify gaps, the other to ensure they been remediated properly by our experts.
Penetration Test FAQs
Now, let's address the burning questions that often swirl in the minds of IT sentinels and small business owners:
A penetration test acts as a proactive defense mechanism, detecting vulnerabilities before malicious entities have the chance to exploit them. It's a preemptive strategy that safeguards your digital realm from the ever-present threats of the modern cyber landscape.
It is also an important step in your compliance journey, to demonstrate to stakeholders, clients, and partners how seriously you take cybersecurity and how you protect their data.
The frequency of conducting penetration tests hinges upon the ever-changing nature of your organization. It is advisable for organizations to perform penetration testing at least once every year, to maintain a steady level of IT and network security management.
However, we also strongly suggest running penetration tests whenever there are significant app or software modifications, if new offices open or new network infrastructures are added.
Following the completion of a pen test, it is crucial you share the results among your IT and compliance teams, engage in discussions regarding future strategies, and reassess the organization's overall security stance by crafting a remediation plan, testing it, and coming up with a long-term security strategy.
Empowered with this information, you can strengthen weak points, address vulnerabilities, and elevate the overall cybersecurity posture.
Get Help Running a Penetration Test
We get it, finding someone skilled enough to do your penetration testing can be a difficult – and expensive - quest. It is actually one of the main challenges SMBs face when achieving compliance , you're not alone. The good news is that you don’t have to look further!
BEMO includes 3rd party Penetration testing service as part of our compliance packages, taking charge of all the procedures and processes (including coordinating the timing of the tests, meeting with you to interpret the results, and taking remediation action to close the gaps).
Our dedicated Compliance Engineering Team will perform internal and external penetration testing twice per year; once to identify security gaps and again to demonstrate your strengthened security posture. We manage your ongoing security, so you don’t face a painful remediation process or worse yet, a security breach.
Remediation is the process of fixing any gaps or weaknesses in your security controls that are identified during the assessment process. Many compliance providers only show you the gaps found in penetration tests, vulnerability scans, readiness assessments, etc., but do not help with remediation (fixing the problem).
But, as already noted, BEMO facilitates remediation as a result of the pen testing. So don’t take the risk of leaving your security to chance, contact us to get one step closer to achieving and maintaining compliance!
Top 10 Posts
-
Windows 10 Pro vs Enterprise
-
Migrate From Gmail to Office 365: Step-By-Step Guide
-
Windows 10 Enterprise E3 vs E5: What's the Difference?
-
What are the 4 types of Microsoft Active Directory?
-
How to Migrate from GoDaddy to Office 365
-
Google Workspace to Office 365 Migration: A Step-by-Step Guide
-
How to Set Up Office 365 Advanced Threat Protection
-
10 Benefits of Microsoft Teams
-
Top 3 Reasons to Move From Google Drive to Microsoft OneDrive
-
How to remove Office 365 from GoDaddy (tips and tricks)
-2.png?width=1080&height=1080&name=Untitled%20design%20(5)-2.png)




Leave us a comment!