| Silver | Diamond | Platinum | |
|---|---|---|---|
| (Minimum 20 seats. Microsoft licensing not included.) |
user/month |
user/month |
user/month |
| Plan Features | |||
| Security Monitoring with Email Alerts Email alerts when suspicious activities are identified on your network. **Managed IT required for response/resolution. |
|||
| Email Security Protect your email from malicious attachments, phishing links, spam, and spoofing and an email encryption service to protect sensitive content. |
|||
| Identity Security Securing identities is a key component of the Zero Trust security model. Ensure that identities are monitored, protected, and that only employees can access company resources. |
|||
| Corporate Device Security Centrally manage and secure company-owned laptops, PCs, tablets, phones through Intune Mobile Device Management. |
|||
| Personal Device (BYOD) Security Manage and protect you company data on personal mobile unmanaged devices. Publish, push, configure, secure, monitor, and update mobile apps. |
|||
| Vulnerability Patching patching Microsoft Applications, Windows 11 and MacOS |
|||
| Quarterly IT Review Your dedicated BEMO CSM will meet you quarterly to review your long-term IT Plan, review your account, and review your business technology security and health. |
|||
| Security Attestation Letter BEMO provides official proof of your security status and achievements on a quarterly basis. |
|||
| Document Security Have full control over who can access and read documents. Mitigate against accidental sharing of sensitive information or malicious theft of confidential information through data classification, automatic encryption, and data loss prevention. |
|||
| Guest Management Security Provide guest users a secure and monitored access to collaborate using SharePoint, OneDrive or Teams with limitations and auto-removal to prevent data loss (download, cut/copy, print.) |
|||
| Network Security Microsoft Security Service Edge Internet Access |
|||
| Cloud App Security Know which apps are being used on and off your corporate network. Protect against the risk of Shadow IT and other sophisticated threats. |
|||
| Insider Risk Security | |||
| Vulnerability Management Secure your environments from critical and known vulnerabilities that could be exploited by attackers, including third party applications in Intune. **Managed IT required for vulnerability patching beyond critical. |
|||
| Managed Threat Detection Help contain threats early in the kill chain, leveraging Microsoft Sentinel (XDR/SIEM) and BEMO's Security Operations Center Team. |
|||
| Azure Security Center Monitoring | |||
| Free 3rd Party Add-Ons ConnectWise (cloud backup for M365), Keeper (Password manager) and KnowBe4 (security awareness training |
|||
SECURITY SIMPLIFIED
Get secure. Skip the drama.
- 61% of cyberattacks target small businesses
- 60% of SMBs close within 6 months of a breach
- The average recovery cost tops $1.1 million
You know the stats, but what can you really do? No time. No resources. Where do you even start? Simple: here.
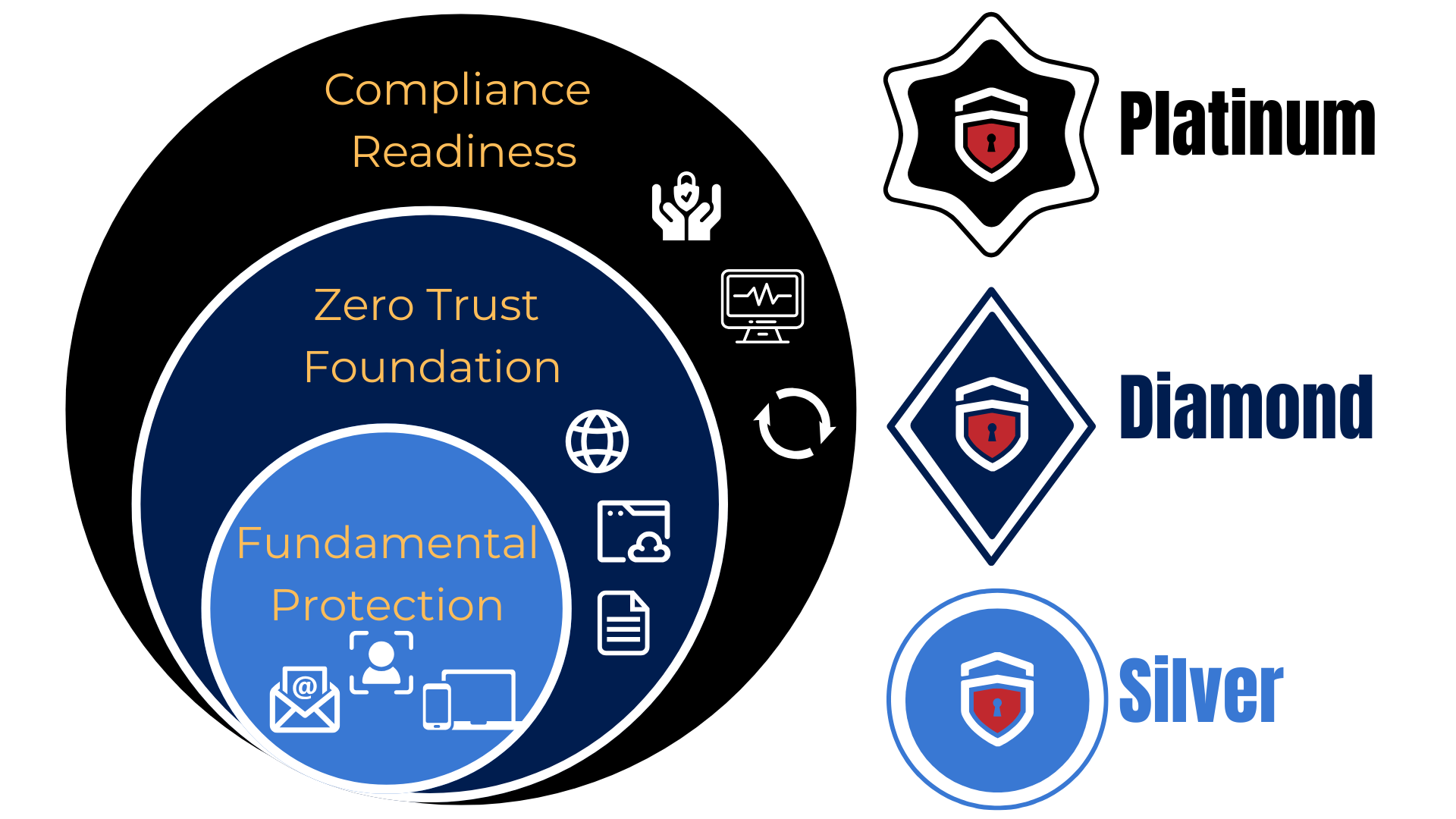



:: BEMO's Managed Security Offerings
Click Here to Review Offering Details
:: Need Managed Helpdesk?
Pair your cybersecurity plan with managed helpdesk for protection and productivity in one solution
:: On-boarding, tech support, hybrid workers, security audits, password resets!
:: Simplify your life with BEMO with the Managed Helpdesk Ad-On.
Key Elements
A comprehensive security plan must include the following elements to keep your people and your business safe as you grow:
 Email Security
Email Security
Email is the primary method of cyber attack. BEMO's custom policies protect you from malware, phishing, spam and spoofing so you can safely send and receive email and encrypt sensitive content.
 Identity Security
Identity Security
Identity security controls and monitors internal access to resources, reducing the risk of accidental and malicious insider threats. Our zero trust policies trust no device by default, even if already inside the network perimeter.
 Corporate Device Security
Corporate Device Security
Centralized management and control of company-owned devices. Manage and secure your fleet of laptops, PCs, tablets, and mobile devices using Microsoft Intune Mobile Device Management (MDM).
 Personal Device Security
Personal Device Security
Your employees want to access company resources on devices you don't control. Enable safe access from personal devices and keep company applications on these devices secure, compliant and up to date.
 Document Security
Document Security
Control sensitive information and mitigate against accidental sharing of sensitive information or malicious theft using data classification, automatic encryption, read access controls, and data-loss prevention policies.
 Application Security
Application Security
Know which applications are being used by your company, both inside and outside your corporate network. Use this insight to protect against sophisticated threat actors who could be hiding inside your environment.
 Network Security
Network Security
How we live and work has changed. Companies need secure networks that can be accessed from anywhere in world. Work in the modern world and move beyond VPN using Microsoft Security Service Edge.
 Managed Detection and Response (MDR)
Managed Detection and Response (MDR)
You defenses need to grow as you do. Our MDR solution combines Microsoft Sentinel (SIEM/XDR) with human expertise in a Security Operations Center (SOC) to rapidly identify and limit threats.
 Vulnerability Management
Vulnerability Management
Protect against critical vulnerabilities in Microsoft and third-party applications that could be exploited by attackers. And for even deep protection, get Managed IT to ensure all known vulnerabilities are regularly patched.
Frequently Asked Questions
The Top 10 questions we get about Security as a Service for Small Business:
-
1) How long does it take to set up a security package for a small business?
We automate the setup of security plans for small business. We can normally set you up 9 to 12 months depending on your availability, offerings purchased, and your number of seats. Let's start today!
-
2) What if my small business is not in a Microsoft environment?
We'll migrate you. This isn't our first rodeo. We've helped hundreds of small businesses migrate to Microsoft 365 over the past 14 years.
-
3) Why should my small business migrate to Microsoft?
Microsoft are the only company in the world that offers a unified IT ecosystem from the operating system all the way up to cloud computing. From a performance perspective, everything is designed to work seamlessly. From a cost perspective, your small business saves in the long run because everything you need is under the same umbrella, all working together.
-
4) Can I switch my plan after I start?
Absolutely. We designed our business around this concept. Our security plans are designed to grow with your small business over time. Pick your starting point now and upgrade over time.
-
5) Do you use AI chatbots or AI support agents?
We do not. There will always be a real human being that you know and recognize by name on the other end of any support exchange.
-
6) Do I have to install custom software on my end to make this work?
You do not. We use deliver our services using standard Microsoft products and services.
-
7) Is this really as simple as you make it sound for my small business?
Yes.
-
8) How do I start the process?
Book a meeting with us. We'll assess your situation, learn about your small business, and talk through everything with you.
-
9) How can I estimate the full cost of Microsoft licensing?
Use our Spend Estimator.
-
10) What makes BEMO an expert in security for small business?
BEMO is a small business built by former Microsoft employees. The pains we'll help you solve are the same pains we had to solve in order to build our own company. We've helped over 1,200 companies solve these same problems.
