
SOC 2 compliance can be a stressful undertaking for SMBs, but achieving it is within your reach. The process of achieving an SOC 2 report for an SMB is like building a house. It requires a budget, careful planning, effective coordination and communication between multiple parties, attention to detail, and the right tools to get the job done.
I recently built my own house, and I will admit, it is no small feat. Would I do it again? Probably not unless I hired a general contractor, so that I could rely on their expertise, save time, and avoid the stress! What were my biggest pain points in the process? Finding and coordinating all the subcontractors, passing all the inspections, and fixing all the non-compliant items while continuing to stay on schedule.
Just like making the decision to build a house, you want to know upfront what challenges you might face so that you can properly plan. You want to know the steps involved so that you can make wise decisions to avoid hassles later.
You need to know if you are equipped to handle the process yourself or if you need to hire that “General Contractor” (a Managed Security and Compliance Provider in the case of SOC 2) that will use their expertise to manage the entire SOC 2 process - from the initial roadmap to the finished SOC 2 report.
In this blog, we will cover:
- Time Constraints
- SOC 2 Budgeting
- Skills Required for SOC 2
- Why SMBs should consider using a Managed Service Provider to Achieve SOC 2
We mentioned Time, Money, and Skill and in the scenario of building a home, and you can easily see how these three factors can directly affect each other – if you spend too much time, it costs you money. If you don’t have the skills, it costs you time and more money trying to fix the mistakes. Let’s discuss these challenges and how they relate to achieving SOC 2.
Challenge #1: Time Constraints
Just like the entire process of building a house, SOC 2 compliance is not something you can do overnight. It requires a lot of planning, preparation, documentation, testing, and auditing. You'll need to dedicate a significant amount of time and resources to ensure that your policies, procedures, and controls are aligned with the SOC 2 criteria and that they are effectively implemented and continuously monitored. The time to complete the process depends on how far along you are with existing security processes and the time your staff has to focus on compliance efforts.
Some of the time-consuming items in the SOC 2 process include:
- Defining the scope of the audit
a. Determine what type of audit you are pursuing SOC2 Type 1 or SOC Type 2
b. Understand the Trust Services Criteria and which are applicable to your business
c. Determine your in-scope systems (internal and 3rd party) that will be part of the audit
- Policy and procedure documentation and implementation
a. Company Security Policies, HR Onboarding and offboarding, Disaster recovery plan, Change management, etc… - Finding a qualified auditor
- Performing a thorough risk assessment
- Finding someone to do penetration testing
- Setting security controls and managing security vulnerabilities
- Remediating gaps (fix the items that aren’t up to par)
- Gathering and organizing documentation and evidence
As the process begins, you may discover tech and operational inefficiencies, resulting in new tasks to complete before the audit (adding more time to the project) – like consolidation of software, moving legacy systems to the cloud, new policies and procedures that need documented and employees that need trained on them.
Challenge #2: SOC 2 Budgeting
SOC 2 compliance is not cheap and understanding the investment (both time and money) can be complex. You'll need to invest in various tools, technologies, and services to help you not only achieve, but maintain compliance over time.
For example, you might need to purchase or upgrade your security software, hire external consultants or auditors, purchase compliance automation software, and purchase penetration testing services. You will need to hire staff with security and compliance expertise and possibly staff a Security Operations Center.
Don’t forget that time is money – opportunity cost. Opportunity cost is the value of what you give up when you choose one option over another. For example, if you spend time on compliance activities because you chose to save money and do it yourself, you are losing the opportunity to use that time for other important tasks, such as growing your business and developing new products or services.
Compliance activities can be time-consuming and complex, especially if you are not familiar with the process. You will have to learn a lot of new information and coordinate many different activities to stay on track. This can also affect your employees’ happiness, as they might feel overwhelmed with having to manage a compliance project on top of their regular job duties!
Some of factors affecting cost include:
- SOC 2 Type 1 or 2 – Type 1 will be less expensive because it does not assess the operation of controls over time like Type 2 does.
- Complexity of your organization – how many of the TSC are you auditing? Do you have multiple custom-built applications? How many 3rd party systems are being evaluated?
- Loss of Productivity of your team due to time spent on compliance effort
- Security Tools and Employee training
a. Threat detection, endpoint mgmt. software, security incident and event management (SIEM) tools, password managers, vulnerability scanners, employee security awareness training tools, etc
b. Penetration testing
c. Tech stack upgrades and migration costs
d. Compliance Automation software
e. Annual recurring cost to maintain SOC 2

Challenge #3: Skills Required for SOC 2
SOC 2 compliance is not something your employees can handle as a side job. You'll need to have a high level of security and operational expertise to understand and implement the SOC 2 standards and best practices.
You'll also need to have a strong culture of security awareness and accountability among your employees, vendors, and partners. You'll need to train them how to handle sensitive data and how to report and respond to any incidents or issues.
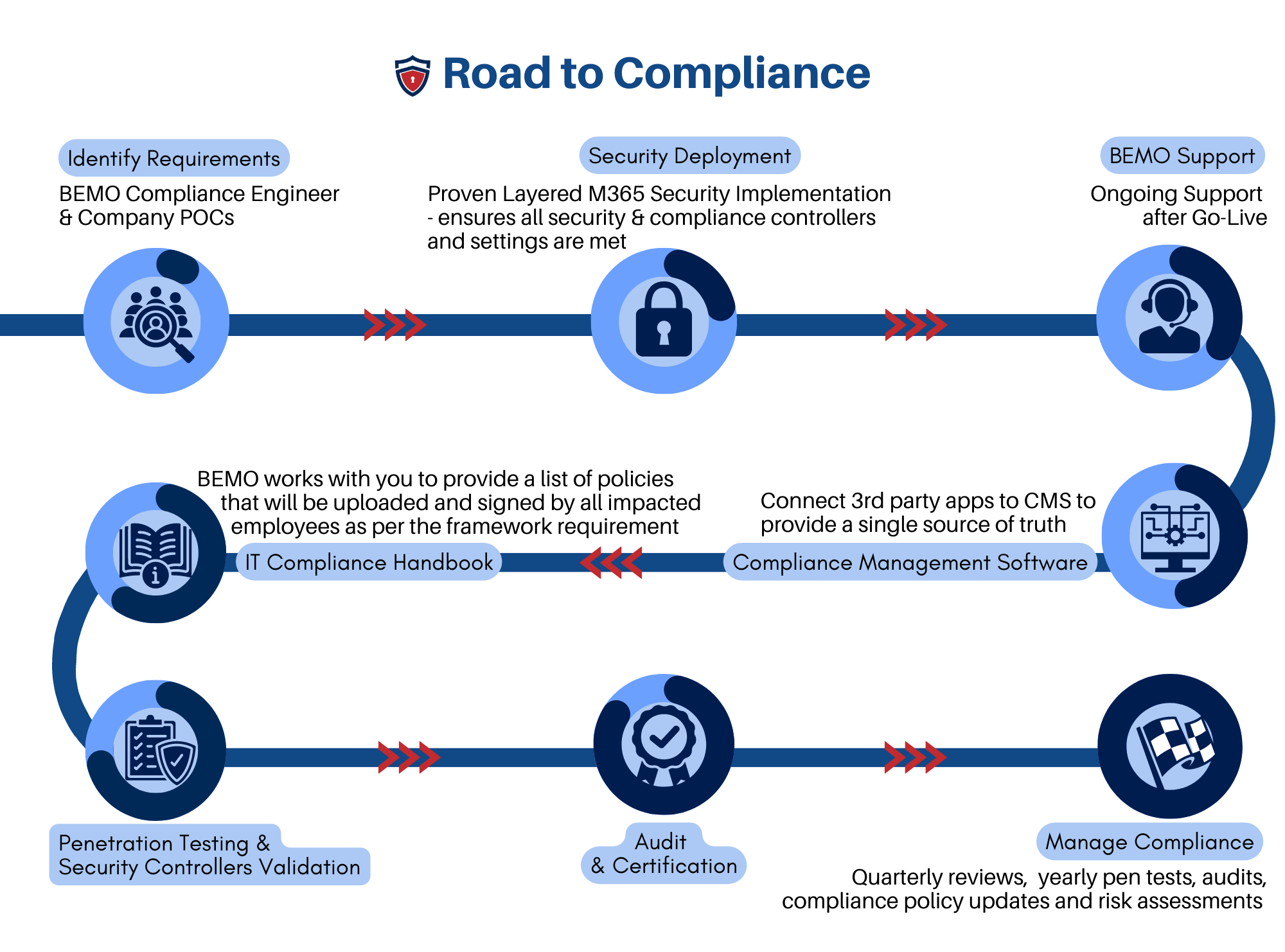
Why SMBs should use a Managed Service Provider to Achieve SOC 2?
We understand that achieving SOC 2 compliance is a challenging and time-consuming process for small and medium-sized businesses (SMBs). It requires a thorough assessment of the organization's security policies, procedures, and controls, as well as a rigorous audit by an independent third-party.
SMBs may lack the resources, expertise, or bandwidth to handle this complex task on their own. That's why many SMBs choose to partner with a Managed Security and Compliance Provider (MSCP) to achieve SOC 2 compliance. An MSCP is a service provider that offers end-to-end solutions for security and compliance, including risk assessment, gap analysis, remediation, implementation, monitoring, reporting, and audit support.
By outsourcing these functions to an MSCP, SMBs can benefit from several advantages:
- Cost savings: An MSCP can help SMBs reduce the costs associated with security and compliance, such as hiring and training staff, purchasing and maintaining tools, and paying for audit fees.
- Expertise: An MSCP has the knowledge and experience to guide SMBs through the SOC 2 requirements and best practices, as well as to address any issues or challenges that may arise along the way.
- Efficiency: An MSCP can streamline the SOC 2 process by providing a clear roadmap, a standardized methodology, and a dedicated team of professionals to work with the SMB. We know that time is money, so a streamlined process will save you money in the long run!
- Assurance: An MSCP can help SMBs achieve and maintain SOC 2 compliance with confidence, as they have the tools and processes to monitor and report on the SMB's security posture and performance.
Because the focus of SOC 2 is security and privacy, you should be careful to choose a Managed Security and Compliance Provider that not only understands the SOC 2 process (and is SOC 2 Type 2 compliant themselves, like BEMO), but can provide a team of Microsoft 365 experts that can migrate your data to the Microsoft 365 cloud and fully secure it up front, before the SOC 2 compliance process begins.
At BEMO, we believe that preparation is key, and our goal is to reduce the time spent in remediating (fixing) things in the middle of the SOC 2 process.
Let’s Recap!
Building a home is a huge commitment of time, money, and skilled effort that will ultimately pay off when you get your Certificate of Occupancy, certifying that the building structure complies with current building codes and is suitable for occupancy (you finally get to move in).
The same goes for SOC 2, with the payoff being your successful SOC 2 report that proves you are complying with current security and privacy standards and suitable for customers and partners to trust to do business with!
Achieving SOC 2 compliance requires an investment in time, money, and skills. But the payoff is worth the sacrifice, if planned correctly.
If you’d like to discuss how partnering with BEMO can help you overcome the challenges of achieving SOC 2, we are here to help!
Top 10 Posts
-
Google Workspace to Office 365 Migration: A Step-by-Step Guide
-
Office 365 MFA Setup: Step-by-Step Instructions
-
How to Migrate from GoDaddy to Office 365
-
Migrate From Gmail to Office 365: 2024 Guide
-
CMMC Meaning : A Comprehensive Guide for Startups
-
How to remove Office 365 from GoDaddy (tips and tricks)
-
What is Microsoft Purview ? Your A to Z Guide to Getting Secure Fast
-
What is The CIA Triad?
-
How to Set Up Office Message Encryption (OME)
-
What are the 4 types of Microsoft Active Directory?





Leave us a comment!