Achieve SOC 2 Certification With Ease
We handle the entire process for you from start to finish at a fraction of the cost of doing it yourself.
What is SOC 2?
 SOC2 is the American Institute of Certified Public Accountants standardized framework that demonstrates a company's security posture to potential customers.
SOC2 is the American Institute of Certified Public Accountants standardized framework that demonstrates a company's security posture to potential customers.
This certification is essential for service organizations handling customer data, assuring customers and partners of their commitment to cybersecurity and privacy.
An SOC2 audit examines the implementation of 80-100 controls, encompassing data security measures, administrative policies, vendor management, risk assessment, security training, and employee onboarding/offboarding.
Click here to read more about what is SOC 2 in our blog!
Why Achieve SOC 2 Certification?
With any major investment, businesses need to consider if the cost is worth the benefit. Attaining an SOC2 certification is a significant feat with an investment of time and resources, but your investment will pay off. We are SOC 2 Compliant ourselves, so we recommend it based on our experience.

-
Enhance your brand reputation and credibility
Enhance your brand reputation and credibility among your customers, partners, and investors. They'll see you as a reliable and secure provider of services, and they'll want to do more business with you. You'll also avoid any nasty lawsuits or fines that could ruin your reputation. Plus, you get to display the SOC2 seal logo on your website.
-
Reduce the risk of data breaches, cyberattacks, and regulatory fines
You'll have a robust system of controls and policies that will protect your data and assets from threats.
You'll also have less downtime and more productivity, as you'll be able to handle any issues quickly and efficiently. You get the added bonus of speeding up your Zero Trust journey! -
Improve your operational efficiency and performance
You'll have clear goals and objectives and be able to continuously measure and monitor your progress and results, ultimately leading to reduced operational risks and costs.
By having SOC2 certification, you can scale your business without compromising your security and compliance. -
Gain a competitive edge in the market
Demonstrate your commitment to quality and excellence, and beat out competitors who might not have an SOC 2 report. You can leverage new technologies and opportunities that require SOC 2 compliance.
-
Boost the morale and engagement of your employees
Your employees can feel proud of working for a reputable and responsible organization that values their data and privacy.
-
Long-term savings of time and money
Long-term savings of time and money. SOC 2 compliant policies, procedures, and controls will make it easier to achieve other security certifications.
Save time filling out different security questionnaires for every large customer. These questionnaires can be incredibly detailed and difficult to fill out if you don't already have processes and documents in place. You can also save money on audits and cyber-insurance premiums.
BEMO Handles It All
 We handle both the achievement of your SOC 2 Compliance as well as the continual maintenance of it, giving you the peace of mind to sit back and focus on your actual work.
We handle both the achievement of your SOC 2 Compliance as well as the continual maintenance of it, giving you the peace of mind to sit back and focus on your actual work.
Plus we have first hand experience on what to expect from the process, since BEMO is a proudly verified SOC 2 Type II Compliant Company.
BEMO handles the entire process of attaining your SOC 2 Compliance:
- Free Migrations to M365
- Complete audit process
- 3rd Party Penetration Testing
- Development of IT Compliance Policies Handbook
- Achieve Framework Assessment and Certification with a BEMO Compliance Engineer
BEMO handles all the ongoing maintenance that goes into maintaining your SOC 2 Compliance:
- Quarterly Compliance Review
- Annual Audits & Penetration Testing
- Annual IT Compliance Policies Handbook updates
- Continuous Compliance Monitoring Software
- Dedicated BEMO Compliance Team to maintain your 72 hours compliance SLA
Pricing Details
We like to be transparent. Fill out the calculator below to receive a quote.
Pricing begins at $10k per month.
This cost is based on BEMO services & MSRP costs that include the following:
- Compliance Automation Software
- 3rd Party Auditor
- Penetration Testing
- BEMO Managed Compliance Services
- BEMO Platinum Security
- Microsoft 365 E5 Licensing
Questions on SOC 2 Compliance? Want an exact pricing breakdown curated for your organization's needs?
We also offer a variety of other compliance solutions.
Visit our webpage to learn more about them and start your journey!




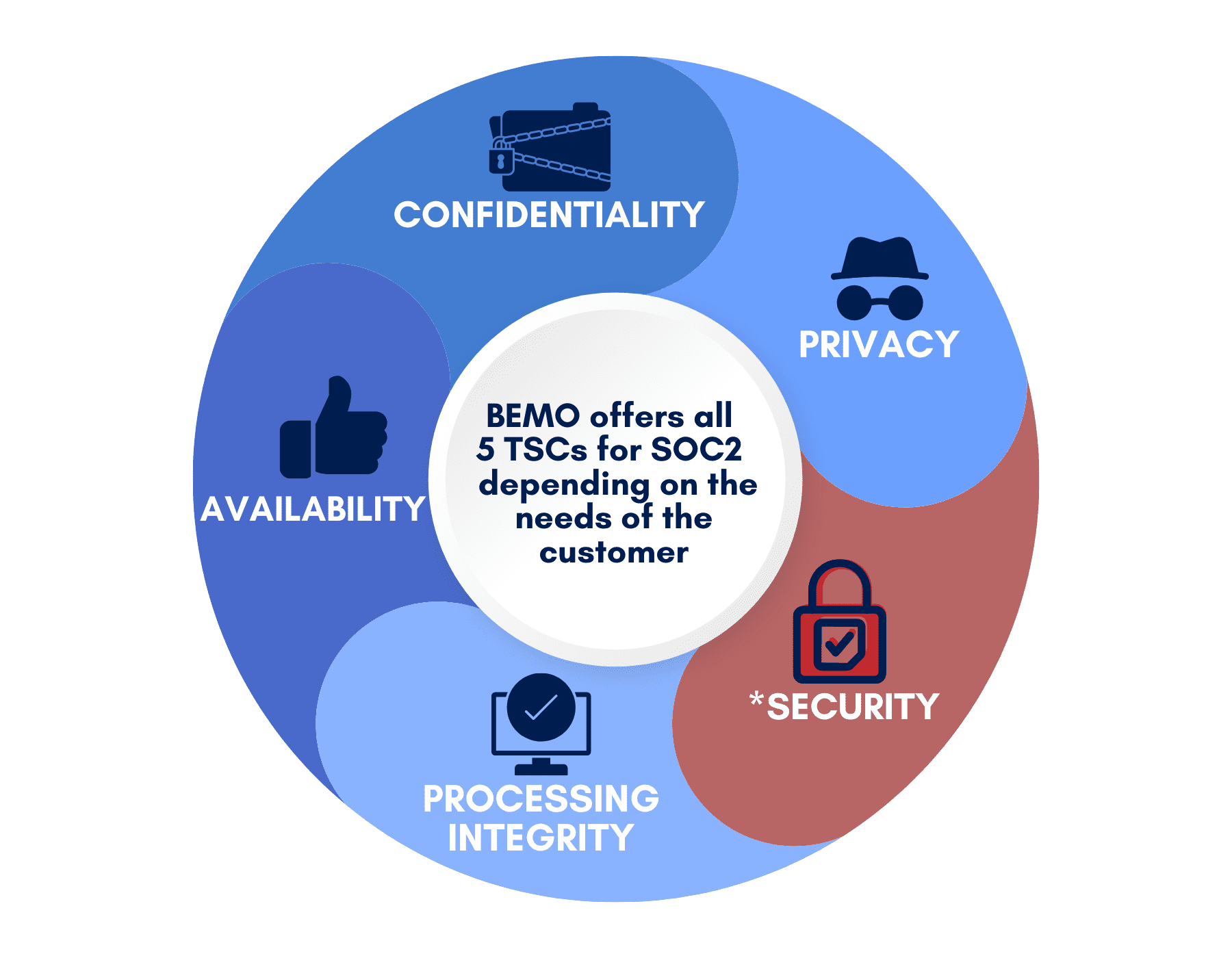
SOC 2 Trust Services Criteria (TSC)
The security criteria is a mandatory requirement for SOC 2 attestation. We will engage in a collaborative discussion with you to determine any other appropriate TSCs that align with your organization's objectives.
-
Security
Required proof that your systems are protected against unauthorized access and other risks.
Example: Security policies, risk assessment and mitigation, protection and monitoring, security controls, and configuration management.
-
Privacy
PII Protection: Personally identifiable information.
Example: Storing social security numbers, email and physical address, etc. Use encryption, access control, and retention.
-
Confidentiality
Evaluates how your business protects confidential information.
Examples: business intellectual property, financial reports, any confidential info. Use access control, encryption, information protection, and policies.
-
Availability
Determines whether your employees and clients can rely on your systems.
Examples: Disaster recovery, performance monitoring, business continuity, and incident response.
-
Processing Integrity
Determines whether a system works properly.
Example: Transaction processing is accurate to avoid fraud. to avoid fraud. Use process monitoring, quality control, etc.
Is SOC 2 Type I or Type II Best For Your Business?
There are many factors that go into the decision whether to pursue a Type 1 or 2. A combination of your goals, cost, and timeline constraints will more than likely dictate the choice. Your customers or partners may make the decision for you by asking specifically for a Type 2.
The table below lays out some of the more important distinctions between the two types.
For a more in depth explanation of Type I and Type II check out our blog here.
.png?width=1024&height=500&name=soc%202%20type%201%20and%20type%202%20differences%20(1).png)
| Type I | Type II | |
|---|---|---|
⌚ Time to Achieve |
3-6 Months |
6-12 Months |
💰 Cost |
Least expensive |
Most expensive |
❓ What It Does |
Short-term. Snapshot of security controls at a single point in time |
Long-term. Ongoing effectiveness of security controls over time |
✅ Pros |
Shorter audit windows; faster and less expensive |
Provides a greater level of trust with clients and partners |
🚫Cons |
May not provide enough assurance and eventually produce the need for Type II |
Longer audit window & more expensive |
🔁 Renewal |
Every 12 months |
Every 12 months |
Start your compliance journey with BEMO today
Free Download - The Ultimate Guide to SOC 2
Experience a stress free achievement of SOC 2 while BEMO navigates the world of compliance for you. Fill out the form to download your free copy of our SOC 2 eBook!
Frequently Asked Questions
-
What are the differences between SOC 2 Type I and Type II?
Type I is a snapshot in time - it looks at the controls you have in place at that moment in time. Type II examines how your controls perform over time. Type II takes longer and is more costly to achieve, but it is generally more requested (and respected) by customers, partners, and prospects.
To learn more in depth details, read our blog here.
-
If we start with SOC2 Level 1 and decide to go with Level 2 later, do we pay the full price for Level 2?
Your security will be in place with Level 1 and you will be paying a monthly subscription price for Platinum security. That won't change. You will only pay the difference in the SOC 2 Level 1 and 2 compliance package.
-
Once we are SOC 2 certified, how can our company demonstrate proof to requestors?
BEMO Compliance customers are provided a public-facing compliance page that they can share with their customers, partners, etc. This portal displays the current status of your compliance framework and security control status in your environment, assuring that you are meeting the requirements. The SOC 2 Attestation report is an internal document (generated by a 3rd-party auditor) that describes the organization's systems and process in-depth. This report can be shared with customers via a secure portal or email under a non-disclosure agreement (NDA).
Become a SOC 2 Pro Yourself
Check out our most recent SOC 2 compliance blog posts, written and researched by our experts.
Stay always one step ahead of the game!
4 min read
How Rushing SOC 2 Compliance Can Cost You a Major Deal (What to Do Instead)
5 min read
What You Should Do the First Time You're Tackling SOC 2 Compliance
BEMO is a Microsoft US Partner of the Year Winner whose mission is to empower any SMB in Microsoft cloud environments to grow securely and stay compliant—without the complexity. We have helped over 1,000 small businesses since 2010.
Services
Resources
© 2026 BEMO. All rights reserved.


.png?width=320&height=500&name=SOC%202%20eBook%20(April24).png)