10 min read
HIPAA Compliance: What Does It Mean & Why Is It Important?
Mohamed Sekrane
on Jan 24, 2023

We’ve all been there: you’re checking in at the doctor’s office and your signature is needed in a few spots. Just sign your name on the dotted line and go, right? Most people never take much more than a second glance at what we are signing away, but if it’s your responsibility to handle that data, you’ve probably looked over the rules and regulations countless times and…maybe you’re still a bit lost. HIPAA is tricky, storing miles of personal data is risky (but essential), and compliance is mandatory. So, what do you do? Read on to discover the ins and outs of HIPAA, from the rules and regs to the intricate dance we must do to marry security and privacy. Let’s dive in!
What is Personal Data?
We all know that when it comes to protecting personal information, the Health Insurance Portability and Accountability Act (HIPAA) sets the standard for healthcare organizations in the United States. But what exactly is considered personal data under HIPAA rules? Let’s take a closer look at the definition of personal data according to HIPAA regulations as well as the measures healthcare organizations must take to ensure the privacy and security of this sensitive information.
As a healthcare professional, it's important to understand the nuances of personal data, specifically regarding personally identifiable information (PII) and electronic protected health information (ePHI).
- PII: refers to any information that can be used to identify an individual, such as names, addresses, and Social Security numbers.
- ePHI: pertains to an individual's health and medical information, which includes information such as medical history, test results, and treatment information.
The overlap between these two types of information can be seen in situations where PII is used to identify an individual and ePHI is used to provide them with medical treatment. Both are considered personal data and therefore must be kept confidential and protected as per HIPAA regulations.
Now, let’s take a more exhaustive approach to what is considered ePHI within HIPAA rules, and what is expected from covered entities when handling these types of data.
What is ePHI From a HIPAA Perspective?
In our previous blogs, we covered the built-in SITs (Sensitive Info Types) Microsoft offers (there are 307 PII!) as well as your ability to create custom SITs to identify and protect specific data not listed in the built-in SITs. You will recognize most of the following data types from the Microsoft Sensitive Info Type Entity Definitions list.
The following identifiers of the individual or of relatives, employers, or household members of the individual, are all considered ePHI:

If you’re like me, you need to open your car door to find your VIN, so the fact that this information can easily be at someone’s fingertips whether they are 5 or 5,000 miles from your car might give you the willies. We’ve all heard about hacks. What if your patient data gets stolen? Fear not. It’s essential to store data so Microsoft created a solution to make sure you could also protect it. More on that soon but first: consent.
HIPAA: Consent & Privacy Through Transparency
Consent is a crucial component of data protection regulations, particularly in the realm of electronic Protected Health Information (ePHI). Healthcare professionals are required to continuously obtain a patient's consent before accessing, using, or disclosing their ePHI. This means that patients must be informed about the types of information that will be collected, how it will be used, and who it will be shared with, and must give their explicit permission for these actions to take place.
Obtaining consent is an essential ongoing process that requires healthcare professionals to keep patients informed of their rights and of how their data is being used. It ensures that patients' rights to privacy and autonomy are respected and must be treated with care as consent can also be withdrawn at any time. For example, if a healthcare professional wants to share a patient's ePHI with a third party, they must obtain the patient's consent for this specific action and explain the reason for sharing the information. Obtaining and maintaining consent helps to build trust between patients and healthcare professionals, as patients are more likely to share sensitive information when they feel that their privacy is being respected and protected. Additionally, obtaining consent helps to mitigate the risk of unauthorized access or disclosure of ePHI, as healthcare professionals are only able to access and use the information if they have a patient's explicit permission.
Rules of HIPAA
There are four rules that make up the HIPAA standard: Privacy, Security, Breach Notification and Omnibus.
The Privacy Rule: Effective April, 2001
This rule establishes national standards for protecting the privacy of personal health information. It defines what constitutes Protected Health Information (PHI) and lays out the rights that patients have with respect to their PHI. The rule also requires Covered Entities (CE) such as health plans, healthcare providers, and healthcare clearinghouses to implement physical, administrative, and technical safeguards to protect the confidentiality, integrity, and availability of PHI.
Main objective: to ensure that individuals' health information is kept private and that individuals have control over who can access their information.
The Security Rule: Effective April, 2005
This rule sets standards for protecting the confidentiality, integrity, and availability of electronically protected health information (ePHI).
It lays out specific requirements for CEs to implement technical safeguards, such as access controls, audit trails, and encryption, to protect ePHI from unauthorized access, use, or disclosure.
Main objective: to ensure that electronic protected health information is secure and protected from unauthorized access or disclosure.
The Breach Notification Rule: Effective September, 2009
This rule requires Covered Entities to notify individuals and the Department of Health and Human Services (HHS) when there is a breach of unsecured protected health information.
Main objective: To ensure that individuals are notified in a timely manner if their protected health information is compromised and to make sure that the Covered Entities report the breaches to the Department of Health and Human Services.
The Omnibus Rule: Effective March, 2013
This rule made significant changes to the HIPAA Privacy, Security, and Breach Notification Rules.
It strengthened the requirements for obtaining patient's consent, implementing risk analysis and management, and provided guidance on how to handle business associates under the rules.
Main objective: to update and strengthen the privacy and security provisions of HIPAA to better protect the privacy of individuals' health information and to keep up with the advances in technology and the changes in the healthcare industry.
How HIPAA Compliance is Enforced
While HIPAA sets a standard for protecting personal health information, the rules and regulations are applied differently between states.
HIPAA is a federal law, primarily enforced by the Department of Health and Human Services (HHS) Office for Civil Rights (OCR). However, there is no standard of enforcement in place. This means that the OCR can investigate complaints and take enforcement action when necessary, but the states have the authority to adopt their own laws and regulations that provide additional protections for personal health information.
However, some states have implemented their own enforcement rules individually.
.png?width=2200&height=1237&name=HIPPA%20blog%20quote%20graphic%20(2).png)
For example, California's Confidentiality of Medical Information Act (CMIA) provides more stringent requirements for obtaining consent for the disclosure of protected health information and provides fines and penalties for violations of the state law.
Similarly, the states of Massachusetts, Nevada, New Hampshire and Texas have laws that are specific to personal information protection, but not specific to HIPAA.
The main takeaway? If you operate in one of the five aforementioned states, you need to abide by both state and federal regulations (which may not be the same).
HIPAA Controls for ePHI Protection
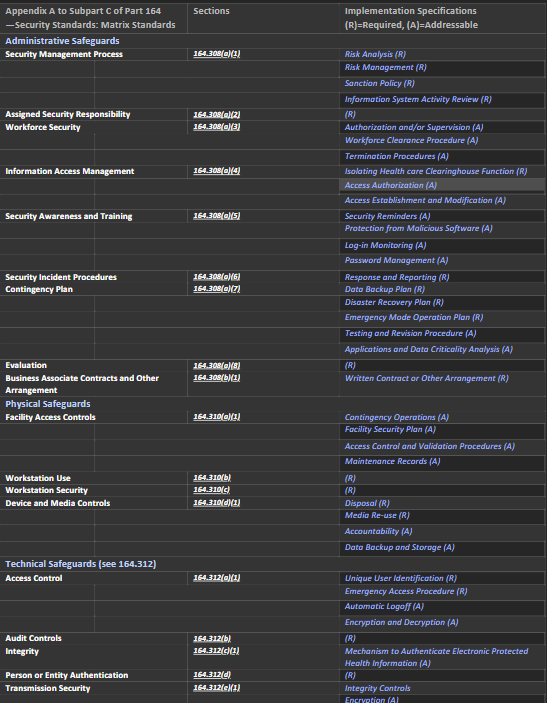
So, how do we map HIPAA rules and regs to action? For this introduction blog, we went straight to the source (so you don’t have to). We went through the combined rules text and extracted the sections that are relevant to our discussion here.
This list gives a closer and more accurate understanding of the relationship between the HIPAA standards and how they translate into clear procedures and implementations within an organization at 3 main levels: Organizational/Administrative Safeguards, Physical Safeguards, and Technical Safeguards.
Source: HHS.GOV
Where did we find the information? In Subpart C—Security Standards for the Protection of Electronic Protected Health Information we discover what is expected from Covered Entities, their business associates, and IT providers.
Let’s describe each section as thoroughly as possible.
§ 164.302 Applicability
Simply, any covered entity must perform the recommendations listed in the regulation.
§ 164.304 Definitions.
In this section of the document, the foundation of our planification is set. Here are the terms used and their definition:
- Access: The ability to read, write, modify, or transmit data/information or use any system resources.
- Administrative Safeguard: Include management actions, policies, and procedures to protect ePHI and manage workforce conduct.
- Authentication: The process of verifying the identity of a person by comparing their credentials with the information on file, to ensure only authorized access to the system or resources.
- Availability: Ensuring that authorized personnel as well as patients (data owners) can access and use data or information whenever they need it.
- Confidentiality: Refers to keeping data or information from being disclosed to unauthorized individuals or processes.
- Encryption: Encryption is the method of converting data into a coded form that can only be accessed using a secret key or process, making it unreadable to unauthorized parties.
- Facility: Refers to the physical location where ePHI is stored, processed, or transmitted, including its infrastructure and technology.
- Information system: A group of information resources that are connected and controlled by the same entity and share common functionalities. It typically includes hardware, software, information, data, applications, and communications.
- Integrity: Refers to the property of maintaining the completeness, accuracy and consistency of data or information, without any unauthorized changes or destruction.
- Malicious software: Designed to damage, steal or disrupt systems. It comes in various forms, spreads through various means, and can cause various problems such as data loss, system crashes, unauthorized access, and financial loss.
- Password: Secret series of characters used to confirm identity and grant access to a system or information. It is considered confidential and is used for authentication purposes.
- Physical Safeguards: Include security measures, policies, and procedures that are implemented to protect electronic information systems, buildings, and equipment of a covered entity or business associate from hazards, unauthorized access and natural disasters. These measures can include physical barriers, security personnel, surveillance cameras, security protocols, and more.
- Security or Security measures: Include a combination of technical, administrative, and physical safeguards that are implemented in an information system to protect it from potential threats. These measures work together to ensure the confidentiality, integrity, and availability of the system and its data. They can include firewalls, encryption, access controls, security protocols, and more.
- Security Incidents: An attempt or successful unauthorized access, use, disclosure, modification, or destruction of information or interference with the normal functioning of an information system.
- Technical Safeguards: The technology and policies and procedures used to protect electronic protected health information and control access to it. These measures can include encryption, firewalls, access controls, and monitoring systems.
- User: User refers to a person or entity that has been granted authorized access.
- Workstation : Workstation is an electronic device, such as a laptop or desktop computer, or any other device that performs similar functions, and the electronic media stored in its immediate environment.
These definitions will greatly help in our next steps are essential for coherent understanding, planification, and management for becoming (and remaining) HIPAA compliant.
The following sections in the document go into more details about each of the controls, starting with General Rules. We invite you to read the linked document if you want to read more about each section:
- § 164.306 Security standards: General rules.
- § 164.308 Administrative safeguards.
- § 164.310 Physical safeguards.
- § 164.314 Organizational requirements.
- § 164.316 Policies and procedures and documentation requirements.
- § 164.318 Compliance dates for the initial implementation of the security standards.
We will focus here on this table: Appendix A to Subpart C of Part 164—Security Standards: Matrix.
It gives us a very clear map of the essential sections of the HIPAA Rules sets and the corresponding safeguards.
This, in addition to the definitions above, will allow us to map these standards to the Microsoft 365 solutions ecosystem – so we will be able to answer your most important question:
Can Microsoft 365 Purview get my company to be compliant with HIPAA?
(Spoiler alert. Yes! it can!! )
If your next question is: Can BEMO help me with this, so I don’t have to do it myself? Spoiler alert X2: Yes, we can, and we are happy to help. Reach out to schedule a free consultation.
We will map this matrix to Microsoft 365 Purview solutions and features in our next blog, for now, save the following image for future use in understanding what it entails for your organization at the moment.
Addressable specifications are up to the covered entity to deploy entirely, partially, or not at all as long as the choice is documented and reasonable. Required specifications are just that: required.
Notification Requirements for A HIPAA Breach
One aspect of HIPAA that is often overlooked are notification requirements. In 2022 the CIRCIA (Cyber Incident Reporting for Critical Infrastructure Act) was signed by President Biden. Although CIRCIA doesn’t directly refer to HIPAA, considering what we said earlier on the overlap between PII and ePHI, HIPAA and those who must follow its regulations, are directly affected.
In this section of the blog, we go quickly through the Notification Rules and Requirements as listed in the HIPAA standards and this will put in perspective the relationship between Data Protection & Data Privacy:
§ 164.404 Notification to individuals.
As it indicates, in case of a breach (as defined earlier) each concerned individual must be notified.
A breach is treated as discovered the first day the covered entity finds out about it or could have found about it if reasonable measures were taken by the covered entity.
Timeliness of notification: within 60 days.
Content of notification: a brief description of the events, time of occurrence, time of discovery, type of ePHI involved, steps that the individual should themselves take, what the covered entity is doing about it in all aspects as well as contact procedures for information (which shall include a toll-free number, an email address, web site, or postal address).
All in plain language.
§ 164.406 Notification to the media.
If a breach involves 500 or more residents of a state or jurisdiction, the covered entity must notify prominent medias servicing that state or jurisdiction, in the same timeliness as the Notification to individuals.
§ 164.408 Notification to the Secretary.
Maintain a log of breaches involving 500 or more individuals, and notify - within 60 days after the end of the calendar year - the Secretary of the DHS.
§ 164.410 Notification by a business associate.
Business associates must notify covered entities in case of breach.
Same standards for timeliness as 164.404.
§ 164.412 Law enforcement delay.
If a written statement is issued by law enforcement, impeding the notification of the breach, covered entities and business associates must delay their notification.
If an oral statement is made, the notification must be delayed 30 days after the oral statement was issued, this includes the official who made the statement.
Privacy & Protection: The Need For Both
As we saw in the start of this blog, HIPAA is made of four main rules. The most significant one is the Omnibus Rule (Main objective: to update and strengthen the privacy and security provisions of HIPAA to better protect the privacy of individuals' health information and to keep up with the advances in technology and the changes in the healthcare industry). In addition to modernizing and reinforcing each of the previous rules, the emphasis for Omnibus is on Privacy.
In an article from the HuffPost, former DHS Director Michael Chertoff responded when asked What frustrates you about what Congress and the press say about technology and security?
.png?width=642&height=361&name=HIPPA%20blog%20quote%20graphic%20(1).png)
This is an excellent illustration of the work we are going to do when we use Microsoft 365 Purview to achieve compliance with HIPAA. We will use the protection as well as the privacy features (they are clearly defined and separated in Purview) and that will help us design a comprehensive solution that will cover all of our HIPAA bases!
Wrap Up
In our previous blogs (What is Microsoft Purview? and Microsoft Sensitivity Labels) we went through the Microsoft Purview Information Protection Framework, which will help us in our compliance journey.
We covered the Phases 1 through 3 (Know, Protect, Prevent) in a standard environment without any specificities on HIPAA. Remember that we kept phase 4 to discuss Data Governance. We’ll get ready to jump into Data Governance and with a healthcare-specific focus!
In our upcoming blog, we will show you how Microsoft 365 features map perfectly to HIPAA requirements, specifically within the Microsoft Purview solutions ecosystem.
Stay tuned and you will be HIPPA compliant soon!
Questions? Comments? Reach out to me on LinkedIn!
Top 10 Posts
-
Windows 10 Pro vs Enterprise
-
Migrate From Gmail to Office 365: Step-By-Step Guide
-
Windows 10 Enterprise E3 vs E5: What's the Difference?
-
What are the 4 types of Microsoft Active Directory?
-
How to Migrate from GoDaddy to Office 365
-
Google Workspace to Office 365 Migration: A Step-by-Step Guide
-
How to Set Up Office 365 Advanced Threat Protection
-
10 Benefits of Microsoft Teams
-
Top 3 Reasons to Move From Google Drive to Microsoft OneDrive
-
How to remove Office 365 from GoDaddy (tips and tricks)
-2.png?width=1080&height=1080&name=Untitled%20design%20(5)-2.png)




Leave us a comment!