10 min read
What is Microsoft Purview ? Your A to Z Guide to Getting Secure Fast
Mohamed Sekrane
on Dec 19, 2022

You need to bring your business up to regulatory requirements and set up your security in a way that is both easily implemented and still keeps information flowing seamlessly between end-users and external collaborators alike. How? Stick with us!
In this blog we will discuss the data protection and loss prevention tools available in Microsoft Purview Information Protection and how to apply them, so your company purr(views)s along like a well-oiled machine.
Consider this your Purview overview where you’ll learn what it’s made up of and how these components interact to best protect your company.
In upcoming articles, we will go into more detail about the configuration steps and end-user experience for each aspect of Data Protection.
.png?width=1900&height=900&name=Purview%20Infographic%20(1).png)
Microsoft has a simple and highly effective, 3-phase framework which is easy to grasp and apply to your data: Know - Protect - Prevent.
Note: A 4th phase, Data Governance, is a holistic approach that applies the learnings of the first 3 phases, once completed. It consists of the lifecycle management of these 3 phases in interaction with each other over time.
Microsoft 365 Purview: How to Approach the Know-Protect-Prevent Phases for Your Business:
Tools to know your Data:
-
Sensitive Info Types
-
Trainable Classifiers
-
Data Classification
-
Assessments & Assessment templates
Tools to protect your Data:
-
Sensitivity Labels
-
AIP UL Client
-
Double Key Encryption
-
Office 365 Message Encryption
-
Service Encryption with Customer Key
-
Rights Management Connector
-
AIP UL Data Scanner
-
Defender for Cloud Apps
-
Purview Data Map
Tools to prevent the loss of Data:
-
Purview DLP
-
Endpoint DLP
-
Microsoft Compliance Extension
-
Purview DLP on-premises scanner
-
Protection of sensitive information in Microsoft Teams and Chats
Information Protection: Creating Your Framework
Phase 1: Consideration: Know your Data
Before your team can harness the full potential of Microsoft Purview, you first must understand the types of data your organization has and works with, how it should be managed based on internal and external requirements, and how it needs to be accessed.
File Formats
All Office files are supported by Purview, including 97–2003. However, for the older version, limitations should be expected such as Auto-save or Co-authoring, which can result in potential sync issues if the file is opened at the same time by two different users and one of the versions' upload is blocked due to unresolved edit conflicts.
Here, a best practice would be to systematically convert old file formats when opened in Office Desktop, manually as a standard step.
In addition, knowing that Microsoft released a feature to enable co-authoring for encrypted files it would be a waste not to leverage it:
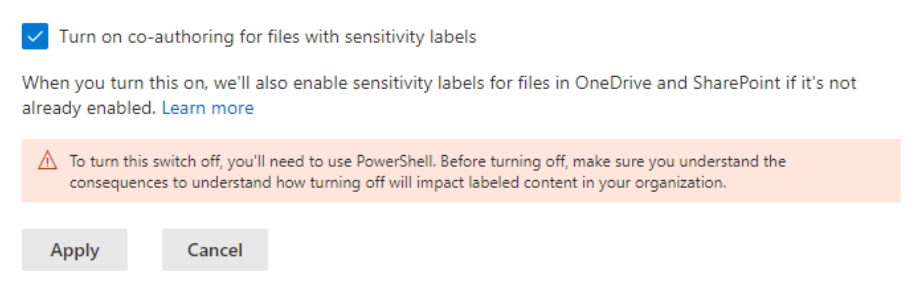
When it comes to deploying file encryption for the first time on a tenant level, it is best to consider a bulk conversion prior to any deployment. This leads to the second point to consider.
File Locations
Before converting your files, you will need to know where they are stored, which may sound obvious but make sure to add this step to your roadmap and consult with each department to learn how they're using their file storage locations. While discovering the location, you should simultaneously consider the file formats and the file architecture as they are all interrelated. Essentially, we need to design a solution that takes into account where the files are stored, who is supposed to have access to each storage location, and with which permissions. This brings us to the file access strategy.
File Access
After establishing File Locations and therefore the membership of each Group/Teams/Site/Folder, we can now define the different levels of permissions and controls that we will enforce through the sensitivity labels.
For Example, in the Teams Site ”Investors”, a group of members is designated internally, and all files related to the company investments are stored in this location and nowhere else.
In addition, a sensitivity label is created and allows a list of external users to View-Only or to Review the documents while the internal users have full rights using one label.
This approach not only drives hygiene in your files management posture but also guarantees that even if confidential information fell into the hands of an undesired or unexpected recipient, they would still need to fulfill the preconfigured encryption label access requirements to view the information. Now that's good protection!
Workflow and Internal Processes
The aforementioned considerations, once laid down in an overall company-wide standard, will create a behavioral adoption of more compliance-resilient workflows and processes, creating and encouraging a culture of care around sensitive information.
For example, you might require users to always have a Sensitivity Label on their working files (either Internal or External). This increases their attention and involves them proactively in the Data Life Cycle.
This approach is great for tech-savvy end users willing to take responsibility and control over their daily usage of sensitive information.
Another approach would be to encrypt all files by default or configure an auto-labeling policy that will target specific Information you want to protect. However, in this scenario, the end-users would need to receive clear communication and training prior to kick-off to seamlessly implement the changes and not be stymied by unforeseen access issues.
This approach requires more initial involvement but in the long term requires less effort to maintain.
Industry Regulatory Requirements
This section supports the previous (notice a theme here?). Each business has a relatively large set of regulatory requirements to conduct activities legally, and safely while respecting the privacy of all parties the organization interacts with.
This should not be the only reason why you chose to implement Information Protection, but it certainly is at the top of the list! Additionally, it is your best ally to drive adoption and with realistic, well-designed, globally accepted, and sought-after standards and rules that can give credibility and serenity to your business, employees, customers, or any institution you are involved with.
Information Protection and specifically the Compliance Manager Assessments can help you with HIPAA, SOC1 & 2, FINRA, GDPR, and ISO 27001 via prepopulated and tailored templates for each regulatory rule.
With Compliance Manager Assessments, you get a report of recommended actions to take and you will be able to assign each action and track its progress all in the Compliance Manager. Implementation steps will be recommended and there will be a Testing tab to document the implementation results as well as a Standards & Regulations tab that shows you which standards/regulations are impacted by this specific action.
We will dive deeper into Assessments in our coming HIPAA blogs. Stay tuned!
The list below is only 20 of the available 700+ templates that can be used for customizable assessments:
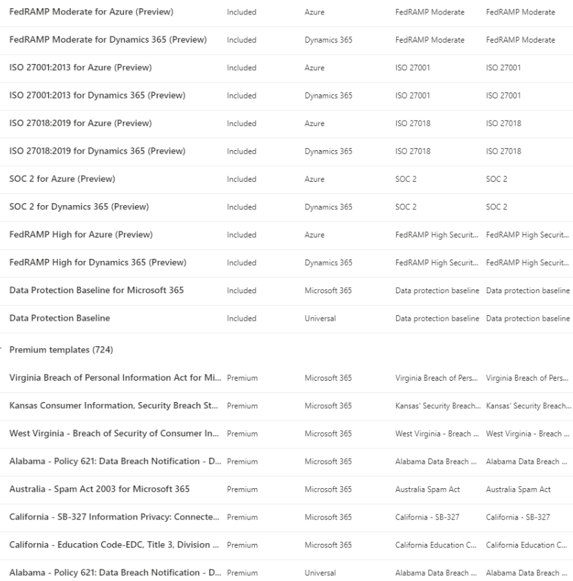
Internal Company Policies
Following industry regulations is essential but there’s another reason you’ll want to implement Information Protection: deciphering how your business wants to conduct its approach to Data Governance from an internal point of view, and from the company's core values perspective.
Of course, you need to follow the laws and regulations, but your solutions will have more staying power if you involve the end-users in the solution architecture process.
Every department in an organization has different daily habits, usual collaborators, internal members, etc. Having the necessary conversations to uncover and discover these habits will nourish the solution design and help both the technical team and the end users.
So, what are your company's core values and how do they reflect and correspond to Information Protection? Creating alignment here will be a huge step in the right direction.
With the current state of cyberattacks, no company is safe unless they are secure, and security starts from within. It is crucial to develop an internal company culture around Information Protection and Data Governance that is periodically maintained through awareness sessions or even Attack Simulations (see: https://docs.microsoft.com/en-us/microsoft-365/security/office-365-security/attack-simulation-training-get-started?view=o365-worldwide). We do these at BEMO throughout the year to keep everyone on their toes and create continued awareness of our security expectations for our team members.
Microsoft Sensitive Information Types
Now that we have gone through the preliminary considerations, the next step of getting to know your data will be strongly facilitated.
With the knowledge you’ve gathered, you can now clearly provide a list of Sensitive Info Types that you want to look for within your content and add these as triggers within your Sensitivity Labels Policies and Data Loss Protection Policies.
The policies can be applied to both emails and files, and even Teams chats — so when these Sensitives Info Types have been detected, a predefined set of permissions and access restrictions would be applied and would never leave the file.
But what are Sensitive Info Types?
A sensitive info type is a recognizable pattern of data that can be found in your content.
Microsoft has a very complete list of SIT templates, which are tailored per category and country. Examples are U.S Social Security Number or German ID Number, Bank Account Number, Medical & Health Terms, Physical Address, etc., organized in groups very similar to the Data Protection Compliance Manager Assessment Templates:
While this is a good start, the true power is in selecting your own custom list of PII in this list, or, for an even stronger/more specific approach, creating your own Sensitive Info Types by feeding in Keywords or Dictionaries that contain words, expressions, and IDs.
All existing sensitive information can be added and crawled through in all the locations, to design specific rules for specific content types, in the same policy. Once found, all files and emails adhering to the criteria will be protected and encrypted:
Trainable Classifiers
Microsoft also facilitates the process of organizing or classifying your data to easily search, move, and apply policies (such as protection, retention, or encryption levels), and more. This process can be done either manually or through the help of a built-in, automated tool.
Trainable Classifiers are extremely powerful tools and come in 2 types: Manual and Automated.
Below is what you will see the first time that you open the Trainable Classifiers tab:
Automated:
This category of classification mechanisms includes finding content by:
-
Keywords or metadata values (keyword query language).
-
Using previously identified patterns of sensitive information like social security, credit card, or bank account numbers (Sensitive information type entity definitions).
-
Recognizing an item because it’s a variation on a template (document fingerprinting).
-
Using the presence of exact strings exact data match.
Manual:
Once the first scan is complete, we will be able to create our own Classifiers:
Phase 2: Implementation: Protect your Data
Sensitivity Labels & Policies
At this phase, we now know precisely where our sensitive data resides, who may access it, and when it needs to be shared. When do we need to restrict access to it, and, for how long. We also know if our current practices and policies (if any) correspond to the posture we want to achieve in the short, mid and long term.
With this, we can take the appropriate decisions to plan our deployment.
It is time to create our sets of labels. See the label as a lock that you can attach to each piece of content either based on a specific keyword or PII, or location.
Only a predefined set of users can access the content, and each one of them can be set up with unique permissions.
Labels can be applied by default, manually, or automatically:
Azure Information Protection Unified Labeling Client
This is a very useful application, especially if you want to extend your labeling capabilities to your local files, or file type other than Office (txt, PDF, VBS, JS, JPG, etc.)
If your company uses Intune, it can easily be deployed remotely.
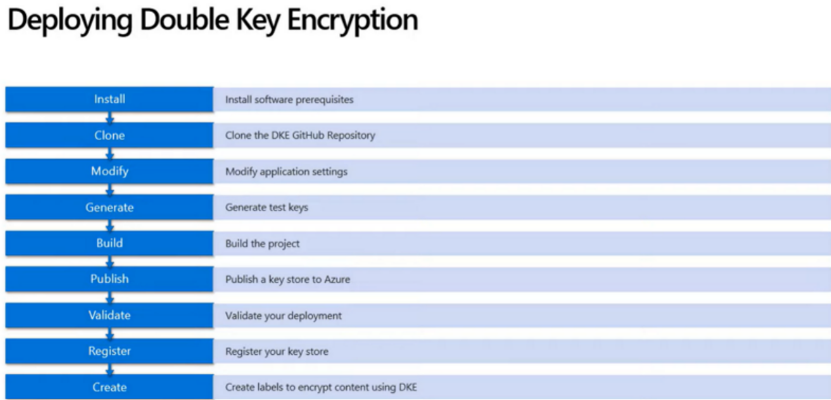
Double Key Encryption
Microsoft Information Protection lets you use your own Encryption Key in addition to a double key stored by Microsoft. Both are required to access the content. The DKE (Double Key Encryption) is used with the AIP UL Client (Azure Information Protection Unified Labeling).
This is especially useful for organizations who want to be sure that in all circumstances no one else but them can access the content. By giving only one key to Microsoft and the second being in an on-premises location under your control you can do just that.
More details here: https://learn.microsoft.com/en-us/microsoft-365/compliance/double-key-encryption
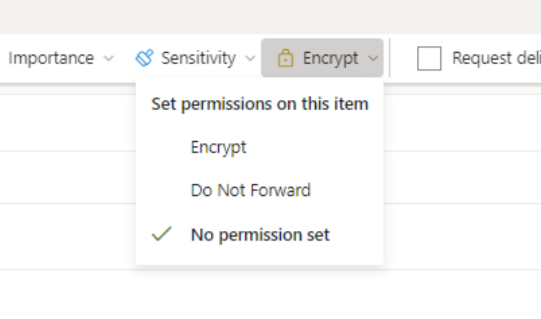
Office 365 Message Encryption
This feature applies to email protection and to the button in the Outlook ribbon button Encrypt/Do Not Forward/No Permissions Set.
This can be applied automatically (using Sensitivity Label Policies or Data Loss Protection Policies) or manually by the user when needed:
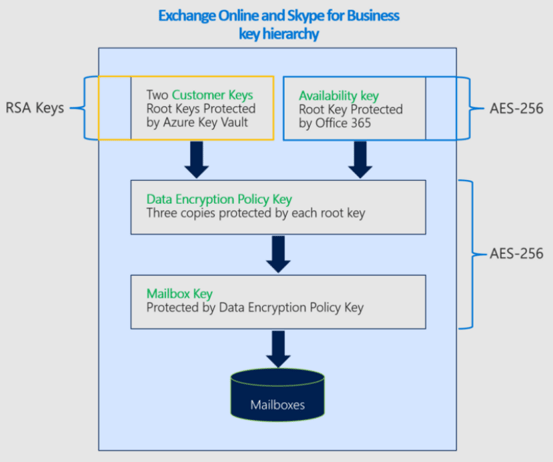
Service Encryption With Microsoft Purview Customer Key
This tool allows you to generate a custom key in Azure and use it as an additional layer to the hardware protection already under BitLocker. Be aware: it is not hybrid capable.
Service Encryption uses DEP (Data Encryption Policies) that define the encryption hierarchy.
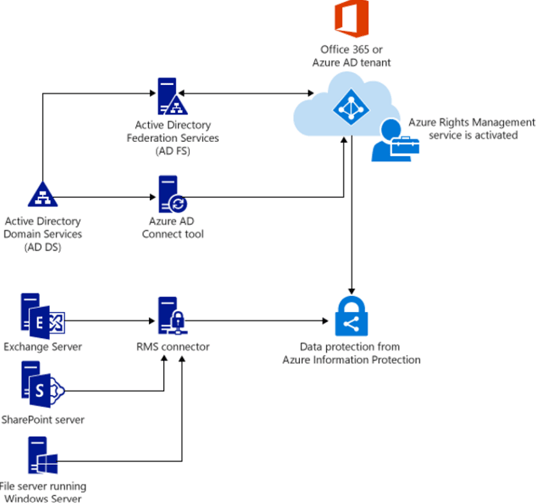
Rights Management Connector
A very lightweight solution to rapidly increase the security of your data transit between your on-premises servers and your Cloud locations.
This is the list that Microsoft provides as supported servers:
Exchange Server, SharePoint Server, and file servers that run Windows Server and use File Classification Infrastructure to classify and apply policies to Office documents in a folder.
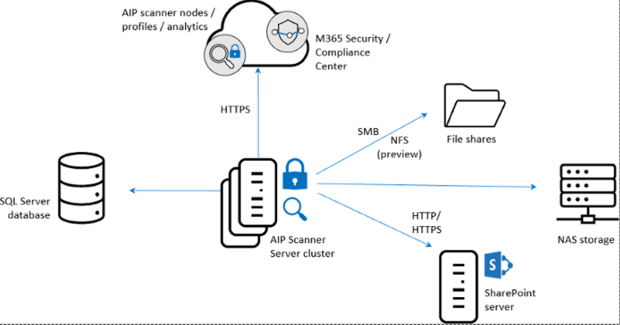
AIP Unified Labeling Scanner
This scanner is ideal if you want to keep your files stored locally and still leverage your Microsoft 365 Sensitivity Labels.
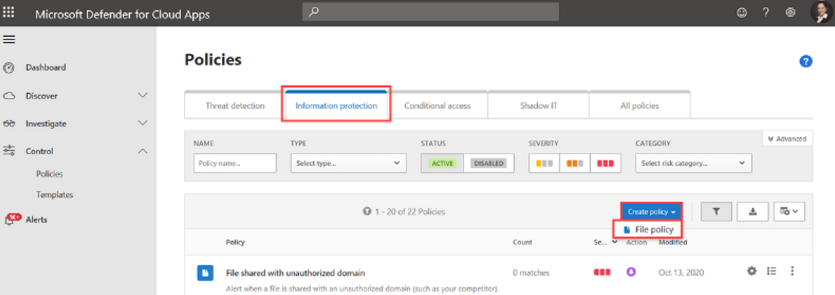
Defender for Cloud Apps
This portal is specifically designed to give you control over the users’ sessions and app-level protection and monitoring. The range of capabilities is lengthy but let us start with an example that is related to Information Protection in our case:
Using File Policies, you can apply labels to files based on a comprehensive set of contextual filters allowing you to narrow down the files you need to protect efficiently.
In addition, file monitoring is also improved in the Defender for Cloud Apps portal when using the Sensitivity Label Policies at the same time.
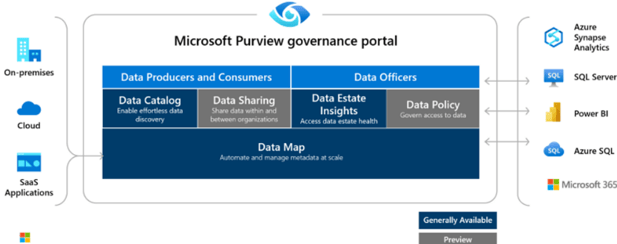
Purview Data Map
This is the most expandable tool in this list. While it is a complex topic, we will present it for now as a Governance portal that ingests the data present and draws reports, recommendations, and tools to assign ownership and curation tasks to Information Officers or even create secure and in-place org-to-org sharing solutions.
It extends the security ecosystem to even more particular data sources and offers organizations with demanding and eclectic IT environments the possibility to leverage Microsoft Purview Information Protection features across all their data map, with source connections to a wide range of 3rd party cloud solutions (Amazon, Salesforce), your on-premises servers, or your cloud-hosted databases.
Phase 3: Prevention: Data Loss Protection
Data Loss Protection Policies
The Data Loss Protection policies contribute toward stopping data from going outside the organization or being shared inside without applied protections if it fits specific metadata or contains sensitive information.
It is a complementary solution to Sensitivity Labels but can be leveraged in a powerful way and simply. For example: by systematically encrypting all emails that contain PII and are shared Externally.
The Data Loss Protection also supports attachments in emails and can be tweaked to avoid false positives, as some errors might occur.
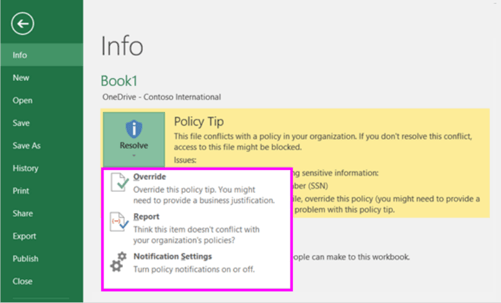
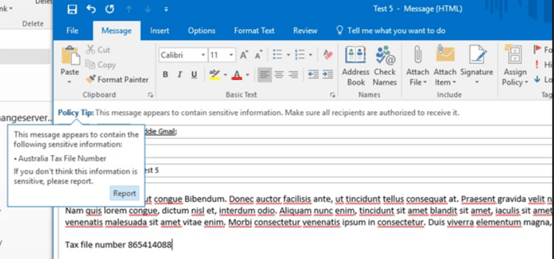
DLP policies also can help guide the users by notifying them via email or policy tips when sensitive content matches the policy settings.
Endpoint DLP
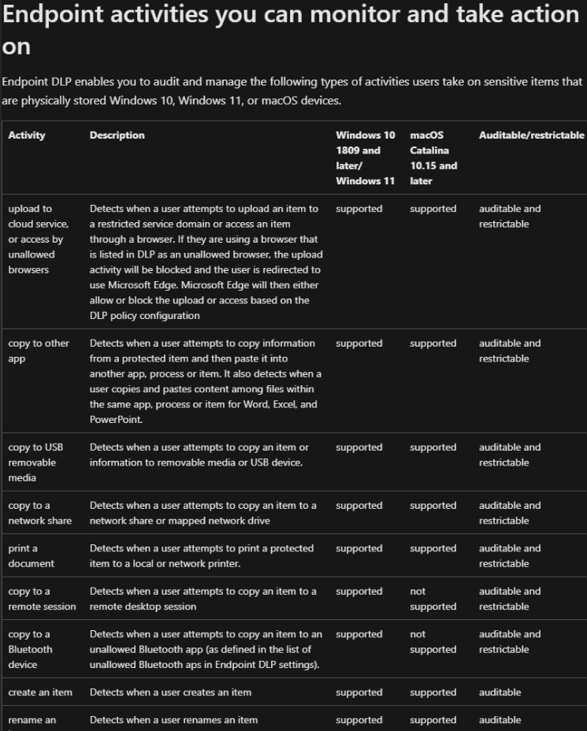
Protect and monitor sensitive information directly stored on the user’s physical devices.
There are multiple rules that either Audit or Restrict activities like Copy to USB or to a Bluetooth Device.
The setting up of this feature is done by configuring the DLP policy, and below you can see the list of activities available:
Microsoft Compliance (Chrome) Extension
This is an extension for the Chrome web browser that enforces the DLP Policies of your organization to the users’ devices.
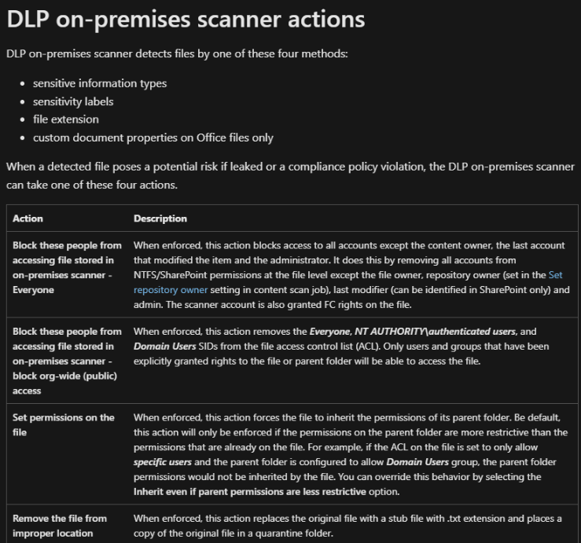
Purview DLP On-premise Scanner
After setting up the Azure Information Protection scanner you can also use this scanner to enforce DLP Policies instead of Sensitivity Label Policies.
For more details: https://learn.microsoft.com/en-us/microsoft-365/compliance/dlp-on-premises-scanner-learn
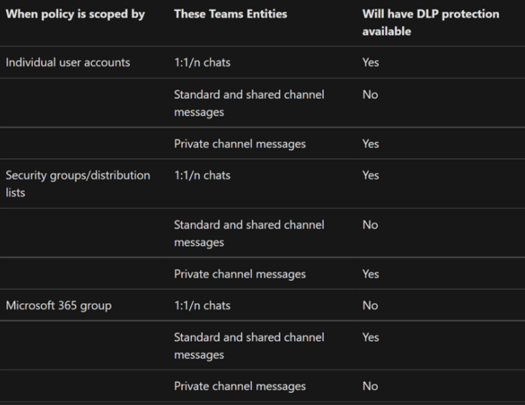
Protection of Sensitive Information in Microsoft Teams & Chats
Like the DLP for Files or Emails, this time it is for Teams, here are the detailed capabilities from Microsoft:
Licensing Requirements
With the number of features, we mentioned in this article, the direct answer would be to have Microsoft E5 to benefit from all the features.
If you are on another licensing plan, feel free to contact us to give you a detailed list of features you can use with your current subscription, or help you choose the best one to fulfill your needs.
Summary
As regulations continue to stack up, it is exciting to look at what Microsoft is bringing to the table to meet this challenge. Their goal is to provide end users with a framework they can creatively apply to their individual situations to design their ideal setup.
Further, this framework should apply to both internal and external access without compromising the company’s security or compliance, and without overloading the flow of information communication and collaboration.
If you have any comments or questions, feel free to leave us a comment or contact me on LinkedIn.
Top 10 Posts
-
Google Workspace to Office 365 Migration: A Step-by-Step Guide
-
Office 365 MFA Setup: Step-by-Step Instructions
-
How to Migrate from GoDaddy to Office 365
-
What is The CIA Triad?
-
What is Microsoft Purview ? Your A to Z Guide to Getting Secure Fast
-
How to remove Office 365 from GoDaddy (tips and tricks)
-
When Will CMMC 2.0 Be Required for DoD Contracts?
-
How to Set Up Office Message Encryption (OME)
-
Migrate From Gmail to Office 365: 2024 Guide
-
SharePoint vs. OneDrive (What's the Difference Again?)


Leave us a comment!