
I bet you’re familiar with the Trojan horse story. In ancient times, the Greeks, locked in a seemingly endless war with the Trojans, devised a cunning plan. They built a colossal wooden horse, a symbolic gift of surrender, concealing a select group of soldiers within its belly. The Trojans, seeing the horse as a victory trophy, brought it within the city walls, unwittingly welcoming their enemies. As night fell, the hidden soldiers emerged, and Troy fell.
Fast forward to the digital age and a similar saga unfolds within our inboxes. Just as the Trojans faced an unexpected breach, we, too, confront the risk of Business Email Compromise (BEC) attacks. Perpetrators disguise themselves in seemingly harmless emails, gaining entry to our virtual havens. But we have all the intel, so that your kingdom doesn’t perish. Let’s check what you’ll learn in this blog post:
- Business Email Compromise Definition
- Business Email Compromise Examples
- How to Prevent Business Email Compromise
Business Email Compromise Definition
So, what exactly is Business Email Compromise (BEC)? In the digital jungle of scams, BEC is the apex predator. The short definition of BEC is an email-based social engineering attack, targeting organizations to defraud them.
Cybercriminals manage to compromise or impersonate someone within the organization, to play with trust and authority. This could be a high-ranking executive, a trusted vendor, or even the CEO. Once they've slipped into this disguise, they send out seemingly legitimate emails, often requesting financial transactions or sensitive information.
If you want to prevent falling victim to business email compromise, you must understand the basics of how cybercriminals think and work.
First, these are not your run-of-the-mill phishers casting a wide net, hoping for a catch; these criminals do their homework. BEC is much more specialized and carefully crafted.
Cybercriminals stalk their targets, learning the ins and outs of their communication style and business relationships. Social media becomes their hunting ground where they extract personal clues to make their scams all the more convincing. In some cases, they even create mirage-like fake websites, adding layers of deception.
When the time is right, the scammer strikes, impersonating someone you trust. Whether it's a request for a wire transfer, a demand for gift cards, or a subtle extraction of sensitive information, their tactics are varied and cunning.
The secret to their success lies in a technique known as email domain spoofing, where they replicate the email address of a trusted party, leaving you none the wiser and vulnerable.
.png?width=1200&length=1200&name=BEC%20examples%20(8).png)

.jpg?width=1200&length=1200&name=BEC%20examples%20(1).jpg)
In the event of a successful attack, your organization faces a cascade of consequences, not only economically, but also in terms of your reputation. Financial losses ranging from thousands to millions of dollars are a looming threat. Moreover, an attack could impact potential deals, as clients lose trust in your security standards and controls.
Business Email Compromise Examples
Let's dive into the scammers' playbook. BEC comes in various forms, the most common being the false invoice scheme. It's a devious tactic where scammers craft invoice messages that look so authentic, you'd think they were the real deal.
These emails often resemble those you regularly receive from legitimate vendors or partners, making them hard to spot.
Once you take the bait and process the payment, the funds vanish into the digital wilderness. The false invoice scheme preys on trust, exploiting the established relationships and routines of businesses. It's a silent predator, stalking its prey with carefully crafted disguises waiting for the perfect moment to strike.
There are other forms of BEC like lawyer impersonation or CEO fraud. No matter the form, the goal is always the same: hack into a trusted email account, demand money and leave your bank account dry. These tactics may sound like plotlines from a cybercrime thriller, but they're happening in real-time.
According to the FBI’s Internet Crime Report, there were over 21,000 BEC complaints in 2022! You can never be too safe.
Here's a business email compromise example and a few red flags to watch out for:
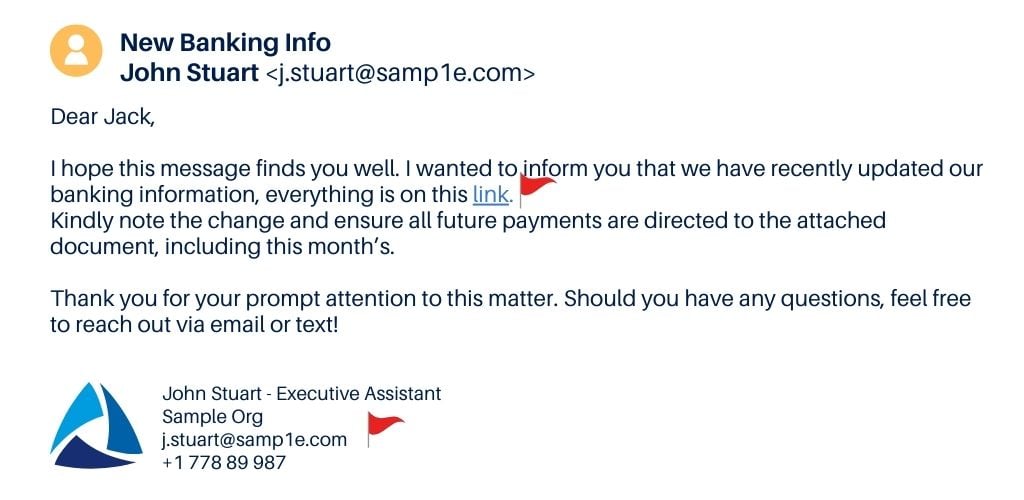
This is a classic case of a tactic known as "typosquatting" or "domain spoofing." In this strategy, attackers create email addresses that are very similar to legitimate ones but contain slight misspellings or alterations. The goal is to trick recipients into thinking the email is from a trusted source.
In our example, the legitimate email is j.stuart@sample.com, while the fake one is j.stuart@samp1e.com, switching the “l” for a number one. To the casual observer, especially in a quick glance, these addresses might look nearly identical.
The attacker actually registers the misspelled domain name days before the attack in an attempt to trick the basic email filters that a company may have in place.
The attacker’s goal is to get the email to land into the target’s inbox without going to spam or quarantine. To enhance the illusion, they even added the company's logo. But remember, anyone can download a logo from the internet.
Stay cautious and verify contact information by cross-referencing it with your established contacts - a phone call, or a Teams message, rather than relying solely on the details provided.
Also, do not open suspicious links! If you hover over the hyperlinked section, it'll reveal the actual web address the link leads to.
How to Prevent Business Email Compromise
Now, the million-dollar question: How can you shield your business from the cunning clutches of BEC? Fear not, here are some battle-tested strategies:
- Secure Your Email with Microsoft Defender for Office 365:
Defender for Office 365 is not just about protecting your emails; it's a comprehensive shield for Microsoft Teams, SharePoint, OneDrive, and all the Office apps. Get protection against advanced cyberattacks, such as phishing, malware, spam, and business email compromise, internal email protection, and detailed reporting. Keep those virtual gates locked tight! - Use Email Authentication Tools:
Implement email authentication protocols like Domain-based Message Authentication, Reporting & Conformance (DMARC), DomainKeys Identified Mail (DKIM), and Sender Policy Framework (SPF). These acronyms might sound like alphabet soup but think of them as your digital bodyguards—ensuring that only emails with verified authenticity make it to your inbox.
If you’d like to learn what each of them does and how to set them up, check out our blog post “How to Enable SPF, DMARC, and DKIM.”
- Employee Awareness Training:
Arm your team with knowledge. Educate them on the subtle red flags that signal potential phishing emails and stress the importance of verifying unexpected requests for money or information.
At BEMO, we use KnowBe4 to enhance our cybersecurity defenses. KnowBe4 specializes in providing comprehensive cybersecurity awareness training. Through their platform, we conduct simulated phishing campaigns that replicate real-world threats, allowing us to assess and reinforce our team's ability to recognize and respond to potential phishing attacks.
It's a proactive approach to security that empowers our staff with the knowledge and skills needed to stay vigilant in the ever-evolving digital landscape. A well-informed team is a powerful line of defense.
- Multi-Factor Authentication (MFA):
MFA refers to using multiple methods of identity verification to allow access to users. Typically, in addition to a password, users are required to provide an extra authenticator, like a one-time password (OTP), a fingerprint scan or face recognition.
That way if an unauthorized person gets access to an email’s username and password, they won’t be able to go in any further, making that information useless for their cunning scheme plans. Add this extra layer of protection. It's like having a secret handshake – only those with the right combination get in.
- Get Third-Party Support:
Consider partnering with cybersecurity experts like BEMO. Our BEMO experts can deploy proven, advanced security configurations that are designed to protect your business from BEC attacks. You can leverage our expertise and let us monitor your email for any suspicious activity, while you focus on your core business activities.
We have 5 different Cybersecurity Solutions you can choose from depending on how leveled up you want your security to be. All of them include email security but make sure to compare the other advanced features you’d like to unlock with different packages, here.
.png?width=1024&height=500&name=BEC%20examples%20(9).png) Plus, if you’re one of our Managed IT customers, we go beyond monitoring and alerting you of any threats, we act on alerts on your behalf, before scammers can make a move.
Plus, if you’re one of our Managed IT customers, we go beyond monitoring and alerting you of any threats, we act on alerts on your behalf, before scammers can make a move.
Follow these best practices to prevent a breach and avoid responding to a compromised email account.
Don't let cyber scoundrels turn your inbox into a playground. By staying vigilant, leveraging the right tools, and arming your team with knowledge, you can outsmart the tricksters and keep your business safe from the lurking dangers of Business Email Compromise. Stay cyber-savvy, and happy emailing!
Top 10 Posts
-
Windows 10 Pro vs Enterprise
-
Migrate From Gmail to Office 365: Step-By-Step Guide
-
Windows 10 Enterprise E3 vs E5: What's the Difference?
-
What are the 4 types of Microsoft Active Directory?
-
How to Migrate from GoDaddy to Office 365
-
Google Workspace to Office 365 Migration: A Step-by-Step Guide
-
How to Set Up Office 365 Advanced Threat Protection
-
10 Benefits of Microsoft Teams
-
Top 3 Reasons to Move From Google Drive to Microsoft OneDrive
-
How to remove Office 365 from GoDaddy (tips and tricks)
-2.png?width=1080&height=1080&name=Untitled%20design%20(5)-2.png)



Leave us a comment!