
We're diving deep into the choppy waters of cybersecurity, explicitly focusing on advanced protection against phishing and how to avoid cyber attacks. Why? Well, did you know that mail is the top gateway for ransomware?
At some point you've probably received an email that looked legitimate, only to realize it was a cleverly disguised phishing attempt. If so, you are not alone. Over 90% of cyber-attacks start with email!
It is easier for attackers to trick someone into clicking a malicious link in a well crafted email than it is to break through a computer’s defenses.
Therefore, getting an email defender is critical, but with collaboration tools such as Teams Chat on the rise, email is no longer the only form of communication we need to protect. And with the ever-evolving threat landscape, it can be tough to spot advanced attacks.
.png?width=590&height=288&name=intro%20(1).png)
You may ask how can your SMB possibly afford to put all these defenses in place?
Fear not, because Microsoft Business Premium is here to save the day with sophisticated protection against all new threat factors that may come your way, ensuring that you can rest easy knowing that your organization is fully protected! So buckle up, and let's set sail!
- What Are the Types of Phishing?
- What Does Impersonation Look Like?
- How to Protect Your Email From Being Hacked?
- ,Extra Security Best Practices
- BEMO Security Tips
The Phishing Pond: What Are the Types of Phishing?
When it comes to cyber-attacks, there are a few distinct types that you should be aware of: phishing, spear phishing and whaling These attacks can range in sophistication and specificity, but they all have one goal: trick you into giving up sensitive information.
And while your basic email filter may catch generic spam and phishing attempts, more sophisticated attacks require a more intelligent solution. So let's dive in and explore each of these concepts, as well as how to prevent cyber attacks and protect your business with Business Premium.
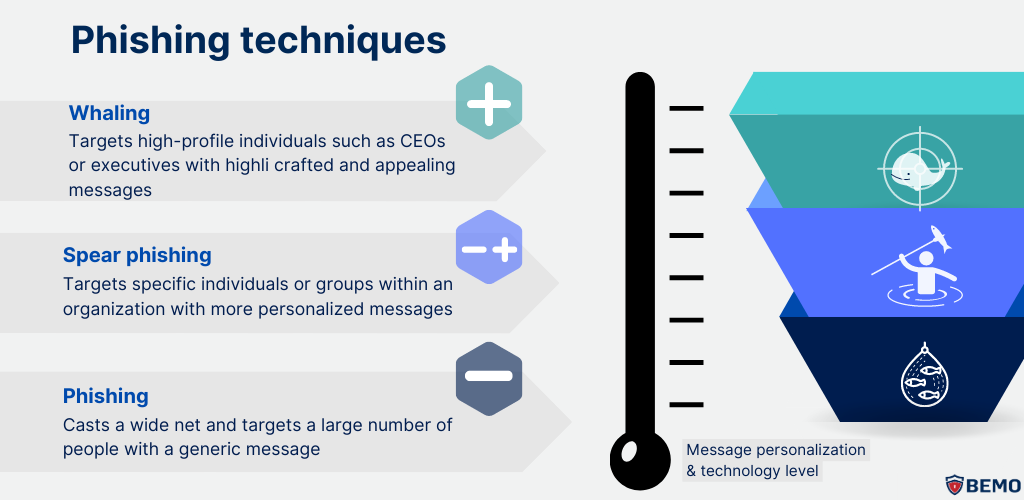
Phishing:
Phishing is the most common type of cyber-attack, and it's often the first thing that comes to mind when we think of email security. Phishing attacks involve sending fraudulent emails to many targets, hoping that some will take the bait.
These emails typically use generic language and may ask you to click on a link or download an attachment. But don't be fooled! These links and attachments can contain malware that can infect your system or steal your personal information. Fortunately, basic email protection tools like Microsoft Exchange Online Protection can catch these types of attacks.
Spear Phishing:
As digital platforms continue to evolve, attackers are becoming savvier in their methods. Spear phishing is a more targeted form of phishing, where attackers will send fraudulent emails to a handful of well-researched employees in one organization. They typically gather information about the targets, such as their job roles, email addresses, and other details, to craft highly personalized and convincing messages.
Whaling:
On the other hand, whaling is even more targeted and focused on high-level executives or top-tier members of an organization. These attacks are carefully crafted to look safe and realistic, and basic email protection tools may not be able to catch them.
Whaling can be of two types – either the attacker targets high-level executives, or they impersonate a high-level executive to create a sense of urgency for an employee. Either way, the motive behind the attack is almost always financial gain.
Business Premium includes intelligent protection against these impersonation email attacks.
What does Impersonation Look Like?
Attackers may use various techniques to make the fraudulent email appear to come from a trusted source, such as a senior executive or a well-known brand.
But how do they manage to make these messages seem so realistic? The answer: social engineering.
This ploy relies on psychological manipulation rather than technical exploits to achieve its goals. Cybercriminals use a variety of strategies to make their messages seem realistic and urgent, such as impersonating authority figures, creating a sense of urgency, or exploiting emotions like fear or curiosity.
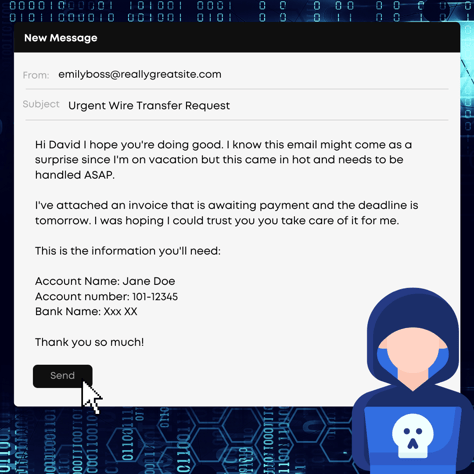
Attackers may use a similar email address or display name, or even copy the organization's logo and branding to make the email look more legitimate. This is known as email impersonation.
Unfortunately, these tactics can be highly effective, making it even more important to have a robust email security solution like Defender for Office365 in Business Premium to protect your organization against these types of attacks.
Don't Get Hooked! How to Avoid Getting Caught in These Nets
How to Protect your email from being hacked
As we mentioned earlier, hackers are constantly evolving their tactics, which means you need a robust email security solution to keep up.
That's where Business Premium comes in and where we can prove just how effective is Microsoft Defender.
In addition to traditional anti-spam and anti-malware protection, Premium includes features to provide an additional layer of security against phishing and malware attacks.
.png?width=1024&height=500&name=phishing%20results%20(1).png)
If you want to go down the right path and be protected in real-time throughout all your apps, OneDrive, Teams, email, and more, these are the features you can customize and turn on with Premium:
Safe Links:
When a user clicks on a URL in an email message, Defender for Office365 checks the link in real-time to determine if it is malicious. If the link is deemed unsafe, the user is shown a warning message indicating that the link is blocked.
And you may question why this feature is needed since we assume that the basic email filters should block any type of dangerous site. Well, cyber attackers use a technique called "URL hijacking" or "URL redirecting." to cheat the system. They first create a legitimate-looking shortened URL, then send it to the target in a phishing email, and after it goes through, they can edit its destination.
Once the target clicks on the shortened URL, they are redirected to a malicious website or a fake login page, where the attacker can steal their login credentials or sensitive information.
However, with Business Premium, these links are caught in real-time.
Safe Attachments:
Now, Safe Attachments takes things a step further by launching any attachments you receive in a sandbox environment.
This virtual machine allows your system to look for behavior patterns that might indicate the presence of zero-day malware – meaning it's a brand-new form of ransomware that traditional anti-virus software might not have seen before. By analyzing what the attachment is trying to do, is it trying to change your registry? Is it trying to install a keylogger so it can record your keystrokes? Etc. Safe Attachments can detect and block any suspicious behavior before it has a chance to do any harm.
You can see the coverage that Defender for Office365 provides in comparison to Exchange Online Protection, making it harder for hackers but way easier for you!
If you're interested in learning more about enabling and customizing these features to your SMB's needs, be sure to check out our Office Hours video "Uh oh, don't click on that! Defend your email documents against attacks". There you can check detailed scenarios and a demo of the Business Premium platform, so you can see firsthand how it can help protect your organization against the latest threats.
Extra Security Best Practices:
It can never hurt to have an ally on your corner. We help you set and manage Business Premium features correctly and with our Silver Cybersecurity Package you can fortify your email security.
On the other hand, we have primarily focused on email protection, but as we stated earlier, we currently have so many communication channels and applications that we cannot afford to ignore them.
Luckily, Business Premium also lets you protect files in SharePoint, OneDrive, and Teams to give you 360 security.
.png?width=793&height=387&name=Phishing%20blog%20types%20%20(1).png)
We want to be involved in your sailing expedition across cybersecurity waters, if you'd like BEMO to be part of your crew and manage this topic for you, make sure to check out our security packages!
Also, don't hesitate to book a call with us to get more information: 
Top 10 Posts
-
Google Workspace to Office 365 Migration: A Step-by-Step Guide
-
Office 365 MFA Setup: Step-by-Step Instructions
-
How to Migrate from GoDaddy to Office 365
-
Migrate From Gmail to Office 365: 2024 Guide
-
CMMC Meaning : A Comprehensive Guide for Startups
-
How to remove Office 365 from GoDaddy (tips and tricks)
-
What is Microsoft Purview ? Your A to Z Guide to Getting Secure Fast
-
What is The CIA Triad?
-
How to Set Up Office Message Encryption (OME)
-
What are the 4 types of Microsoft Active Directory?

Leave us a comment!