7 min read
How to Balance User Experience & Security With Microsoft
![]() Laura Arce Fonseca
on Mar 21, 2024
Laura Arce Fonseca
on Mar 21, 2024

Have you ever walked outside blindfolded? It would be impractical, right? Well, that's what it feels like when security measures turn your digital world into an obstacle course. You're juggling a million passwords, jumping through hoops to verify your identity, and all the while, your data is held hostage behind layers of virtual barbed wire.
Locking everything down tighter than Fort Knox might seem like the safest bet, but trust me, it's a one-way ticket to digital frustration. Let's face it, when your data and devices are under lockdown, they might as well be on a deserted island; unreachable and useless.
Here's the reality check: security doesn’t have to become a synonym for difficulty. And usability is not about throwing caution to the wind. There's a middle ground: a place where security and usability shake hands and agree to coexist peacefully.
In this article, I will show that security and good user experience can work together. I will share ways to balance them and show how usability can improve security measures instead of hurting them.
Why is User Experience Important?
User Experience (UX) refers to the overall experience and interaction that individuals have with technology, encompassing elements such as usability, accessibility, and satisfaction. In the context of cybersecurity and access management, UX plays a critical role in shaping how users perceive and engage with security protocols and systems.
A bad user experience can impact people's commitment to adhering to safety measures and devalue the business’s investment in security solutions.
Streamlining user experience with security measures makes employees more efficient in their daily tasks, and more satisfied with their workflow.
By reducing the time spent on navigating complex systems or troubleshooting access issues, employees can allocate their time and energy towards their core tasks.
And finally, investing in a good user experience balanced with security can result in significant cost savings in the long term. Organizations can avoid the financial repercussions associated with lost productivity plus, by adopting more intuitive platforms can save you resources that would otherwise be spent on training programs.
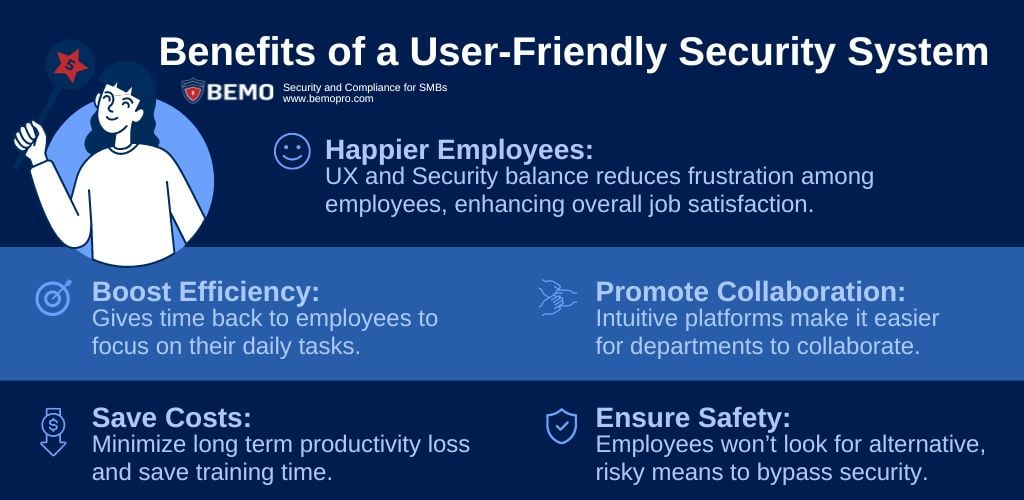
Here are a few things that you should look for in user experiences that support security and compliance:
- Clear Instructions: It might seem obvious, but in practice, many designs lack clarity or a proper communication style! Precise and understandable instructions help users comprehend security procedures and know what actions to take to uphold security standards.
Not everyone has the same level of experience in cybersecurity topics. So, information should be presented simply, not in technical lingo or acronyms. By presenting information in a straightforward manner, users are less likely to make errors or overlook important security measures.
- Visual Cues: Visual cues, such as icons, graphs, and alerts, serve as visual prompts that draw attention to critical security information or actions. These cues can signify the status of security measures, indicate potential risks, or highlight necessary steps to take, thereby guiding users through the security process effectively.
Many of us are visual learners, and being presented with visual aids makes things easier and more engaging than plain text.
- Simplified Processes: Simplifying security processes involves streamlining workflows and minimizing complexity to make security measures more accessible and user-friendly.
Any security or compliance step that gets in the way of accessing data, login into sites or apps, feels like a burden. This often leads to pushbacks and help desk calls. On the flip side, when these features are too subtle or do not appear within their main workflows, security and compliance is often ignored.
The text highlights three key Microsoft Solutions and features that balance user experience with security and compliance. When security procedures are overly complicated, users may resort to bypassing them or finding workarounds, inadvertently increasing the risk of security breaches.
Simplified processes remove barriers to compliance, making it easier for users to adhere to security protocols without compromising efficiency.
Providing a great user experience begins with empathy. To understand the challenges of user experience and security, as well as the diverse users within your company, read the following table and try to put yourself in the shoes of each role.
|
ROLE |
CHALLENGES |
|
IT Administrator |
- Complexity of managing access across multiple systems - Timely provisioning and deprovisioning of user access - Maintaining accurate user identity information - Integration issues with existing infrastructure and applications |
|
Chief Information Security Officers (CISOs) |
- Risk management and mitigation - Budget constraints for implementing robust solutions - Staying ahead of emerging cybersecurity threats - Vendor selection and alignment with organizational needs |
|
End User |
- Frustration with complex password policies - Confusion with multiple authentication methods - Delays in access requests approval - Productivity hindrance because of overly restrictive access controls - Lack of sufficient training and awareness on security best practices |
Microsoft Solutions to a Secure and Frictionless User Experience
Embracing the Microsoft environment comes with a distinct advantage: an ongoing commitment to improving usability and security. With Microsoft's suite of licenses, you can enjoy a comprehensive toolkit, eliminating the necessity for third-party add-ons or services, which typically incur extra expenses and training requirements.
Now let’s talk about some of the many Microsoft Solutions to balance usability and security:
Defender for Office 365 (formerly known as Advanced Threat Protection)
Microsoft Defender for Office 365 is a cloud-based security solution that provides advanced threat protection for Microsoft 365. It is designed to protect users from a wide range of cyber threats, including phishing, malware, and spam.
Defender for Office 365 uses machine learning and other advanced technologies to detect and respond to threats in real-time, providing a comprehensive and proactive approach to security. Let’s highlight two of its features:
Native Link Rendering
We've all been there... You get an email that gets your Spidey senses going. Intuitively, it seems suspicious, but it is also quite convincing! Maybe it comes from a trusted sender, but the request seems odd, or you simply don't feel right about clicking the embedded link.
No need to worry, because with Defender's Native Link Rendering, you can hover over the link and reveal its true source. Even though the link may look harmless on the surface, Outlook ensures that you can see the native link while it conducts a thorough analysis in the background to keep you safe from potential threats.
This approach balances user experience with security, as users can see the actual links they are clicking on while maintaining protection against threats.
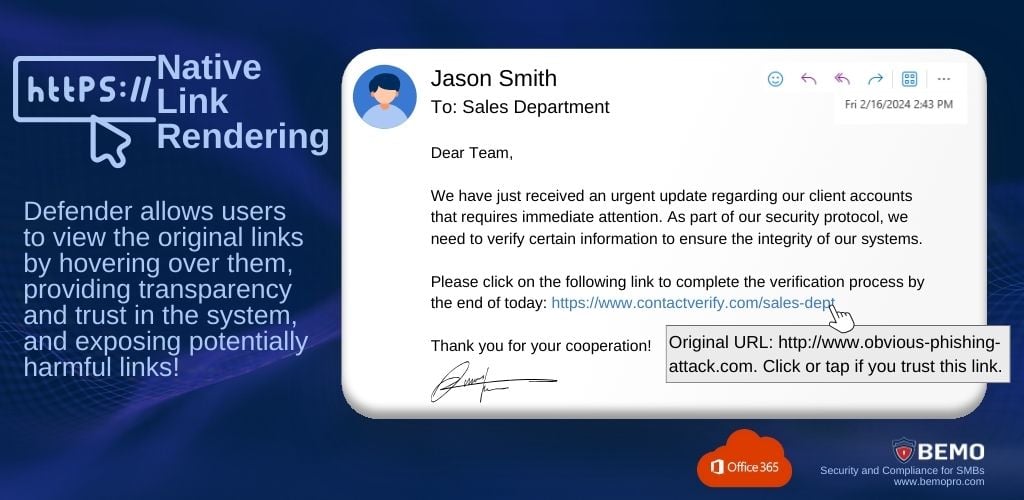
For example, in the image above the email comes from a verified coworker, but the red flag is that it is an unusual and urgent request that involves sensitive data. By hovering over you can see that the links do not match, making it sketchier.
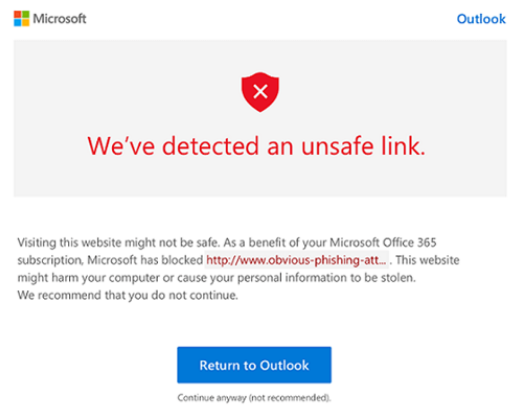
Enhanced Safe Links Warning Pages
The introduction of Enhanced Safe Links Warning Pages further enhances the end user experience by providing detailed information about why a warning is generated.
This level of transparency helps users understand the security measures in place and empowers them to make informed decisions when interacting with potentially risky links in the future.
Microsoft Intune (previously known as Endpoint Manager)
Think about how many devices your organization uses for work these days. It’s not just the company laptops or smartphones you use daily, it’s the printers, projecting systems, monitors or routers that each employee has access to or that personally owns and connects to your business network. (And the number exponentially grows if you have people working remotely!)
With so many devices floating around, the risk of cyberattacks goes up. But with Intune, you can protect and administer all your endpoints from a single place, make sure they are updated, and watch out for any threats trying to sneak in.
Intune’s admin center interface is easy to use and combines graphics like the software adoption score and startup score with actionable recommendations tailored to your system’s needs.
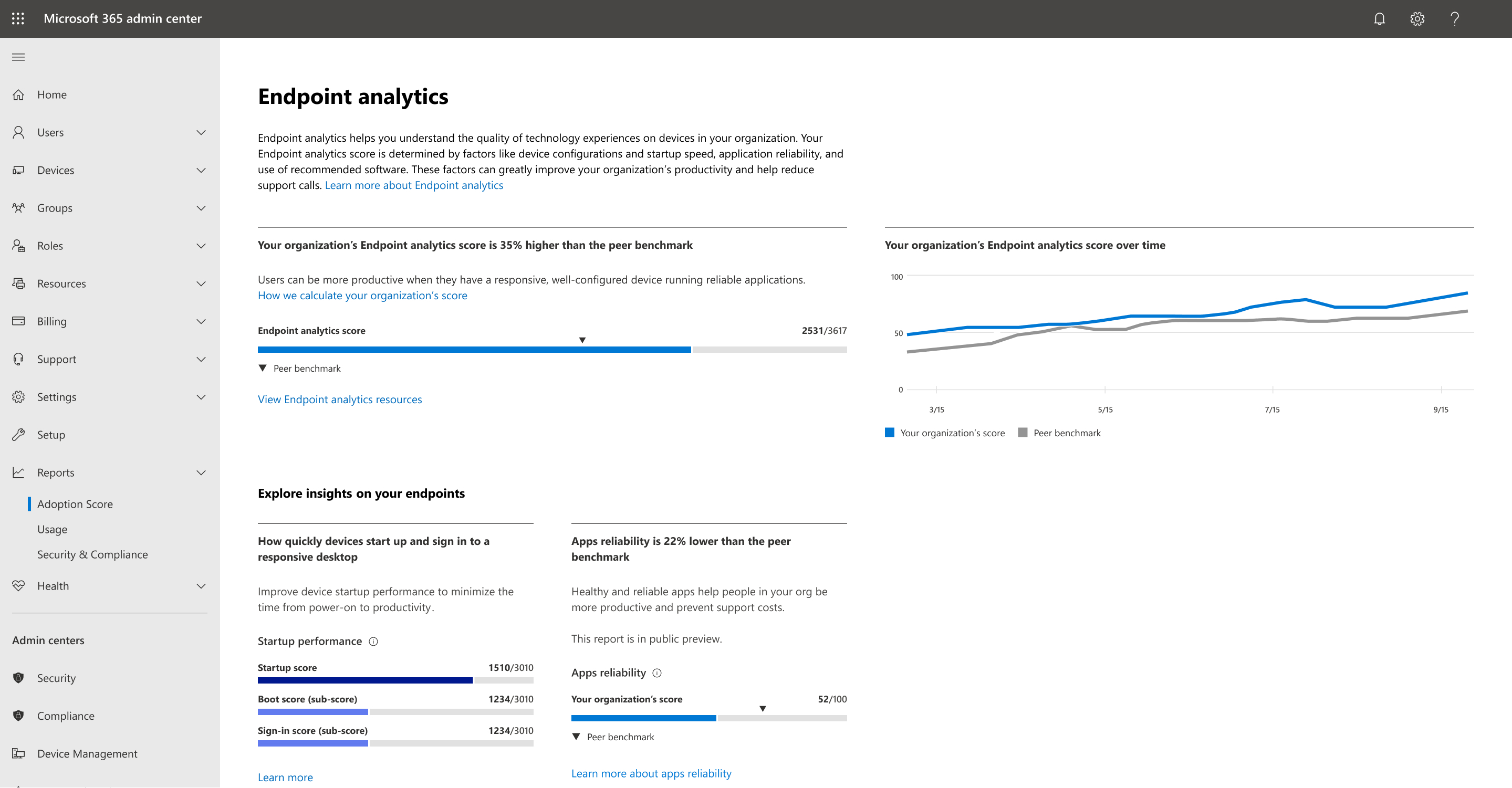
Intune makes it easy for end users to self-enroll their corporate and personal devices (Windows, IOS, Android, macOS, Linux) so they can securely access organizational resources with security and compliance policies you create.
If you have corporate issued Windows laptops, then Autopilot is the ultimate balance of end user experience and security.
Microsoft Entra
MFA, SSPR, SSO
MFA (Multifactor Authentication) enhances security by requiring users to verify their identity through multiple authentication methods before accessing their accounts. It's straightforward: in addition to the correct password, it scans your face or fingerprint to ensure your identity or sends a one-time password (OTP) to your Microsoft Authenticator App.
You can streamline the user experience by combining Multi-Factor Authentication (MFA) setup with Self-Service Password Reset (SSPR). This way, users can manage both simultaneously, reducing complexity.
SSO (Single Sign-on), streamlines user access by letting them authenticate once to access multiple systems or applications. This means you don't need to re-verify your credentials or create new logins to remember.
We can help you configure these tools to meet your business security needs while enhancing the end user experience. Click here to book a meeting and understand how our support team assists with the transition for your end users.
Entra Verified ID
Microsoft Entra Verified ID is a managed verifiable credentials service based on open standards. It uses blockchain technology to provide a secure and decentralized identity system that is resistant to cyber-attacks and data breaches.
This means that individuals and organizations can trust that their digital identities are secure and private, which is essential for a secure user experience.
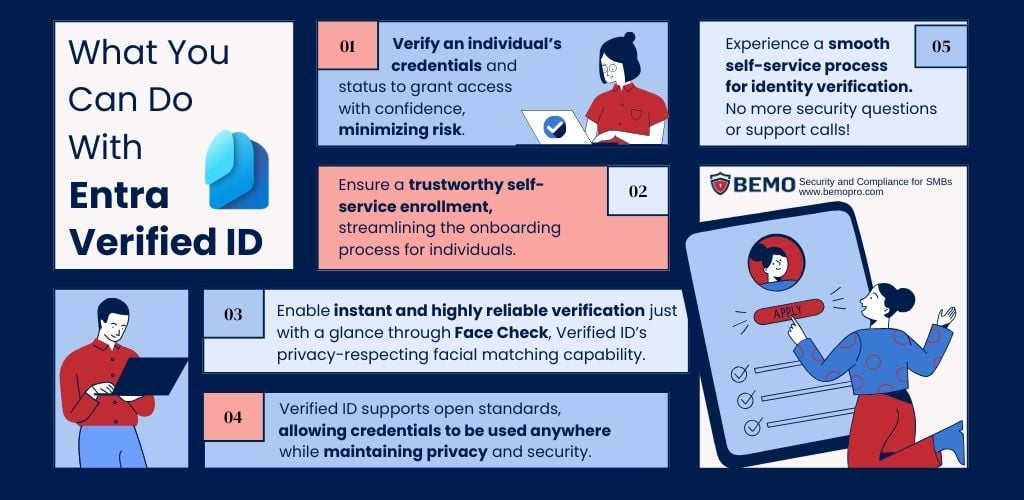
Face Check technology is a feature of Entra Verified ID that enables users to verify their identity using facial recognition. This simplifies processes by no longer having to remember complex passwords or go through lengthy authentication processes.
At BEMO we’ve integrated Verified ID in our helpdesk offering to provide an easier and more secure experience for our customers when submitting privileged requests. Click here and go to page 6 of Microsoft’s Entra Verified ID Whitepaper to read about BEMO's success in automating helpdesk ticketing.
Or book a meeting with us, here to enroll in this security feature!
Get a Better Security Experience
“As BEMO cybersecurity protection is 100% based on Microsoft Technology, I am proud that we offer world-class cybersecurity protection for SMBs that were once only available and affordable by big corporations.”
- Bruno Lecoq, BEMO CEO, CISO
Indeed, the landscape of technology, propelled by advancements in AI, has leveled the playing field, allowing SMBs to participate in the conversation at the same table as industry giants.
If you’re new to it, partnering with a Microsoft-certified expert like BEMO ensures seamless deployment, vigilant monitoring, and timely updates to the latest Microsoft security technologies, freeing you to focus on your core business, and continue wowing your customers!
We recognize that a smooth cybersecurity experience hinges on keeping people at the heart of everything you do. Through our extensive experience with Microsoft's solutions, we've witnessed firsthand how they streamline operations internally and enhance customer interactions, creating a positive ripple effect throughout the ecosystem.
Our approach to security isn't solely about mitigating risks; it's about empowering users to access data effortlessly, thus fostering their success, driving your business forward.
Schedule a meeting today with one of our cybersecurity experts. Let's drive your business forward!
Top 10 Posts
-
Windows 10 Pro vs Enterprise
-
Migrate From Gmail to Office 365: Step-By-Step Guide
-
Windows 10 Enterprise E3 vs E5: What's the Difference?
-
What are the 4 types of Microsoft Active Directory?
-
How to Migrate from GoDaddy to Office 365
-
Google Workspace to Office 365 Migration: A Step-by-Step Guide
-
How to Set Up Office 365 Advanced Threat Protection
-
10 Benefits of Microsoft Teams
-
Top 3 Reasons to Move From Google Drive to Microsoft OneDrive
-
How to remove Office 365 from GoDaddy (tips and tricks)
-2.png?width=1080&height=1080&name=Untitled%20design%20(5)-2.png)






Leave us a comment!