Imagine a world where your business can seamlessly manage its mobile applications, ensuring security, efficiency, and compliance without compromising user experience.
Does it sound too good to be true? You can actually achieve it! In this blog post, we'll unlock the mysteries behind Mobile Application management (MAM) and explore how it can help your company navigate the mobile landscape with confidence.
- What is Mobile Application Management?
- How Does Mobile Application Management Work?
- Why is Mobile Application Management Important for my Business?
- Implementing Mobile Application Management
What is Mobile Application Management (MAM)?
Alright, let's start with the basics. Mobile Application Management, or MAM for short, is a set of technologies and practices designed to manage and secure mobile applications used within an organization.
MAM software allows IT admins to control how company apps are used and how company data is stored on devices, ensuring compliance with security policies and protecting sensitive data.
Deployment, updates, and removal of company apps can all be supervised and applied from one centralized console, without having direct control over the user’s device.
That’s right, MAM does not grant control over the device directly (that would be through Mobile Device Management). MAM only manages certain applications used specifically for business purposes, without touching users’ personal apps and personal data.
Let’s take a closer look at how this technology makes app management and security possible.
How does Mobile Application Management Work?
MAM software works by using a variety of methods to control mobile apps. These methods can include:
App Containment
You probably have a mobile device that you use for both personal and business purposes. With app containment, your business apps would be kept in a separate, secure section of your device, like a virtual compartment.
This separation ensures that your business apps and data remain isolated from your personal apps. So, even if someone gains access to your apps, they won't be able to accidentally or intentionally share any enterprise data with your personal apps and vice versa.
It pretty much acts as a barrier between your personal and professional lives, ensuring that the business's intellectual property stays where it belongs.
Data Encryption
With data encryption, your data is transformed into a secret code that can only be deciphered with a special key. It's like having a secret language that only you and authorized users understand.
This encryption ensures that even if someone manages to access your device or intercept your data, they won't be able to make sense of it without the encryption key. So, your data remains protected and unreadable to unauthorized users, adding an extra layer of security to your business information.
App Security Policies
Let's say you're an IT administrator responsible for managing the mobile apps used by your company's employees. With app security policies, you can establish rules that dictate how these apps should be used.
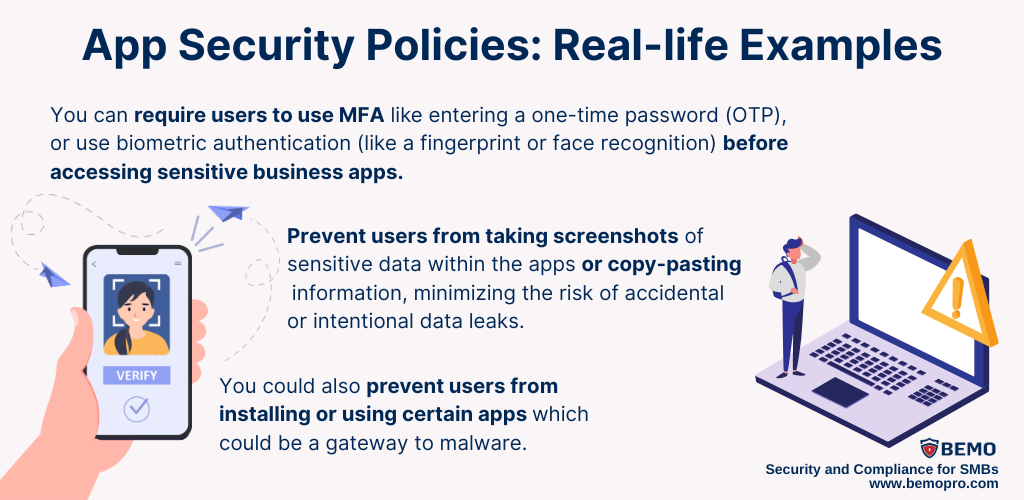
These policies act as a set of rules that help maintain a secure and controlled environment for your business apps, reducing the likelihood of unauthorized access or data breaches.
Remote wipe
In the event of a security breach, if a device is lost or stolen, IT administrators can use MAM to remotely wipe data from mobile devices. This can also be useful if you have a person who's no longer going to work for the company, you can delete all the enterprise apps and information stored or accessed through their devices.
Why is Mobile Application Management Important for my Business?
Small and medium-sized companies are increasingly using mobile devices to conduct business. If security and remote management are taken lightly, your brand could be at higher risk of being the next victim of a cyber attack.
MAM can help you conduct your business securely and efficiently, acting as a preventative method against advanced threats.
There are a few reasons why MAM is especially important for SMBs:
Resource Constraints
Let's face it, resource constraints, including limited IT personnel and expertise, are a reality for a lot of SMBs.
MAM allows IT staff to set policies and controls around apps, such as email, messaging, and other business tools, without requiring full management of the endpoint. This is particularly useful for SMBs where the IT staff is often a single person or even the principal or owner of the business.
Rapid Business Growth & the Need for Agility
Another good reason is that SMBs often experience rapid growth and changing business needs. MAM offers scalability and flexibility, allowing businesses to adapt their app management and security measures as they expand.
It supports a wide range of mobile devices and platforms, ensuring compatibility with the evolving technology landscape.
Bring Your Own Device (BYOD)
And finally, if your company adopts Bring Your Own Device (BYOD) policies, to allow employees to use their devices for work-related tasks, have you considered the security risks it may present? The good news is we have that covered.
MAM software addresses this concern by enabling data protection on personal devices through the methodologies we mentioned earlier: app containment, data encryption, security policies, and more.
Implementing Mobile Application Management
Microsoft has its own Mobile Application Management solution, incorporated into Microsoft Intune, providing an array of app management capabilities for different endpoints - Android, macOS, iOS, and Windows.
However, if you're considering implementing it on your own, you should be aware that it can be a time-consuming and complex process.
If you're considering implementing MAM, partnering with an expert like BEMO can simplify the process and ensure a seamless transition. We have extensive experience in implementing and managing MAM solutions to get them done quickly, easily, and securely. 
Mobile Application Management (MAM) is a game-changer for businesses looking to enhance their cybersecurity and streamline app management. With MAM, you can strike the perfect balance between security and user experience, protecting your business applications and sensitive data without compromising productivity, or resorting to invasive device management.
So, why wait? Take charge of your mobile application management and fortify your business against cyber threats today.
Top 10 Posts
-
Windows 10 Pro vs Enterprise
-
Migrate From Gmail to Office 365: Step-By-Step Guide
-
Windows 10 Enterprise E3 vs E5: What's the Difference?
-
What are the 4 types of Microsoft Active Directory?
-
How to Migrate from GoDaddy to Office 365
-
Google Workspace to Office 365 Migration: A Step-by-Step Guide
-
How to Set Up Office 365 Advanced Threat Protection
-
10 Benefits of Microsoft Teams
-
Top 3 Reasons to Move From Google Drive to Microsoft OneDrive
-
How to remove Office 365 from GoDaddy (tips and tricks)
-2.png?width=1080&height=1080&name=Untitled%20design%20(5)-2.png)



Leave us a comment!