
Zero Trust is a security model that assumes that any network, device, app, or user could be compromised and therefore requires verification for every access request.
If you would like to dig deeper on the concept of Zero Trust, before diving into how your business can implement it, please check our What is Zero Trust blog post.
After reading the first Zero Trust blog, you should be aware that your Zero Trust journey needs to begin now! Different organizational requirements, existing technology implementations, and security stages all affect Zero Trust security model implementation planning.
SMBs can begin to assess their readiness and organize their approach around these key areas:
- Secure Identities
- Secure Endpoints
- Secure Applications
- Secure Data
- Visibility, Automation and Orchestration
- Employee Awareness
Let the journey towards Zero Trust begin!
Secure Identities
When it comes to “verify explicity” as part of Zero Trust, your first investment in the field of securing identities should be to enforce multi-factor authentication (MFA) for all users and devices, utilizing passwordless technology when possible.
To secure identities with Microsoft technology, you will need Azure Active Directory (AAD) - a cloud-based identity and access management service that provides authentication and authorization services for users and applications. It can be used to enforce access policies and to ensure that only authorized users and devices have access to sensitive data and resources.
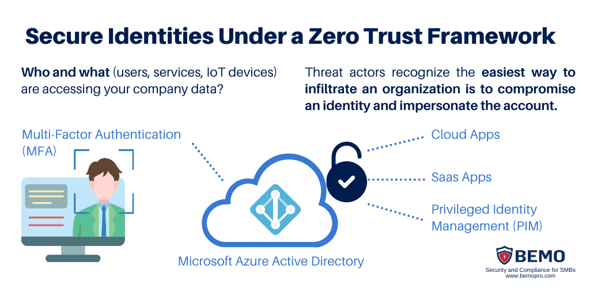
Additionally, use least-privilege with just-in-time (JIT) access policies, granting users only the minimum level of access they need to perform their job for specific periods of time and revoke it when they no longer need it. This can reduce the risk of data leakage or misuse by insiders or outsiders who gain access to privileged accounts (accounts that have the highest level of access to systems, applications, data, and resources). With an AAD P2 license, you can utilize Privileged Identity Management (PIM) with JIT access and Azure Identity Protection to deliver real-time continuous detection, automated remediation, and connected intelligence to investigate risky users and sign-ins to address potential vulnerabilities.
Secure Endpoints
Do you have visibility into what devices are accessing your company data and how are you managing and protecting them? Once an identity has been granted access to a resource, data can flow to a variety of different endpoints, creating a massive attack surface area.
Utilize a comprehensive solution to discover, monitor, and protect endpoints against cyberthreats, including desktops, laptops, smartphones, tablets, and other devices. Include vulnerability management, endpoint protection, and endpoint detection and response (EDR).
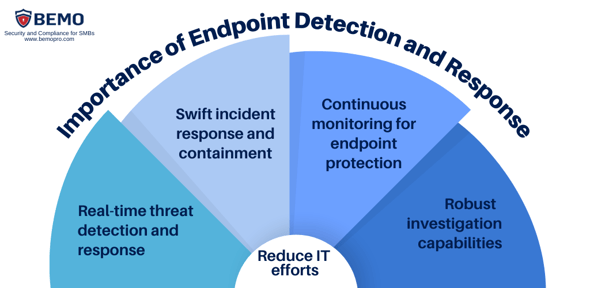
Microsoft Intune provides visibility across your many devices, including mobile devices, desktop computers, and virtual endpoints. You can protect access and data on organization-owned and users personal devices. And, Intune has compliance and reporting features that support the Zero Trust security model.
If you’ve grasped the concept of “assume breach” with the Zero trust model, you’ll recognize the need to not only manage the endpoints, but also to defend them and analyze and respond to anything that may seem suspicious. Microsoft Defender for Endpoint not only provides next-generation antivirus and malware protection, but also detects and responds to advanced attacks.
Secure Applications
Do you have control over which applications have access to your company data and are they kept up to date (including operating systems)?
Employees access data through applications (like Microsoft Office) and 3rd party apps (like printing applications, HR apps, etc). If the application itself is insecure, it can be an open entry point for unauthorized access to company data. Only trusted applications should be used. Applications should be kept up to date to reduce vulnerability. SaaS apps
Microsoft Defender for Cloud Apps provides full protection of SaaS applications, from app discovery to app approval and integration with Azure AD to enforce MFA.
Secure Data
The crown jewels are your company data – whoever controls the data, controls the business. Where possible, data should remain safe even if it leaves the devices, apps, infrastructure, and networks the organization controls.
Can you identify what data is sensitive, who has access to it, and how it is protected from unauthorized access? Is the data backed up? How is it backed up (disaster recovery)?
To ensure protection and restrict data access to authorized users, data should be inventoried, classified, labeled, and -- where appropriate -- encrypted. Encryption can prevent unauthorized parties from reading or modifying data even if they intercept it or access it without permission.
Microsoft Azure Information Protection (AIP) is a cloud-based information protection service that allows organizations to classify and protect their sensitive data. It can be used to automatically classify and label data, and to apply encryption and access controls to sensitive data.
Visibility, Automation, and Orchestration
SMBs should have visibility into who is accessing what data and systems, when, where, and how. This can help detect and respond to suspicious or anomalous behavior , such as login attempts from unusual locations or devices as well as data transfers to external sources.
Do you have a unified method for monitoring and quickly responding to alerts as well as proactively assessing for vulnerabilities? An integral part of a Zero Trust strategy is the ability to detect, investigate, and respond to threats quickly (assume breach).
Microsoft Threat Protection provides the visibility needed into activities going on in your environment, as well as automated investigations and remediation.
Employee Awareness
Do you educate and train employees in security best practices? Employees are often the weakest link in any security strategy.
SMBs should make sure that their employees are aware of the common cyber threats -- such as phishing emails, malware infections, or social engineering attacks -- and how to avoid them. Employees should also know how to use security tools and policies correctly, such as MFA, password managers, VPNs, or secure file sharing platforms.
Here are three Employee Awareness security tools that BEMO uses internally and offers as add-ons for our customers:
Wrap-up
Zero trust is not a one-time project, but it’s an ongoing process that requires constant evaluation and improvement. SMBs should leverage the guidance and resources provided by security experts who can help them properly implement zero trust.
By using Microsoft security solutions with the help of a Microsoft partner, SMBs can enhance their security and resilience against cyberattacks, while also enabling them to improve their productivity and efficiency, while maintaining customer and business partner trust.
Here’s what you get when you take your Zero Trust journey with BEMO :
- Microsoft licensing guidance and purchase
- Up-to-date best practices security deployment by seasoned experts in Microsoft security
- Different packages for different stages of zero trust maturity
- Ongoing security Monitoring and Maintenance and notifications
- Access to our friendly and knowledgeable Support desk with ticketing system
- Dedicated Customer Success Manager to provide ongoing assistance during your zero-trust journey
A phased approach targeting high impact, low-effort areas first can lead to rapid improvements and clarify which steps to take next. You can build a larger strategy as you go. The important thing is to get started!
Don’t have the time or expertise to make start your move towards Zero Trust? Partner with BEMO, your trusted Microsoft Managed Security Partner!
Want to learn more about how you can keep your business cybersecure?
.png?width=224&height=350&name=Top%209%20Cybersecurity%20Tips%20for%20SMBs%20(1).png)
Top 10 Posts
-
Windows 10 Pro vs Enterprise
-
Migrate From Gmail to Office 365: Step-By-Step Guide
-
Windows 10 Enterprise E3 vs E5: What's the Difference?
-
What are the 4 types of Microsoft Active Directory?
-
How to Migrate from GoDaddy to Office 365
-
Google Workspace to Office 365 Migration: A Step-by-Step Guide
-
How to Set Up Office 365 Advanced Threat Protection
-
10 Benefits of Microsoft Teams
-
Top 3 Reasons to Move From Google Drive to Microsoft OneDrive
-
How to remove Office 365 from GoDaddy (tips and tricks)
-2.png?width=1080&height=1080&name=Untitled%20design%20(5)-2.png)







Leave us a comment!