5 min read
Understanding Entra ID Protection (formerly Azure AD Identity Protection)
![]() Laura Arce Fonseca
on Apr 11, 2024
Laura Arce Fonseca
on Apr 11, 2024

Your digital ID is the VIP pass to your organization's hidden gems, the key that unlocks your internal network, or the vault where all your precious data resides. However, just like coveted treasures attract numerous seekers, your digital identity is a target for those with malicious intent.
Here's a heads-up – if you're not rocking the latest protection, compromising your credentials is a walk in the park; a cybercriminal can easily spread laterally and compromise several accounts within your organization. The harsh truth is leaked credentials on the dark web are a booming business.
Check this out: email admin logins can sell for anywhere between $500 and a jaw-dropping $140,000! And logins to antivirus programs and even seemingly low-profile accounts like social media can be snagged for as little as $10.
So, don't fall into the trap of only safeguarding the identities with high-level privileges. You've got to lock down all identities tight!
Thankfully, Microsoft's got your back with Entra ID protection, a smart solution to keep you ahead in the cyber game. In this article, we'll break down what this revolutionary feature brings to the table.
What is Entra ID Protection
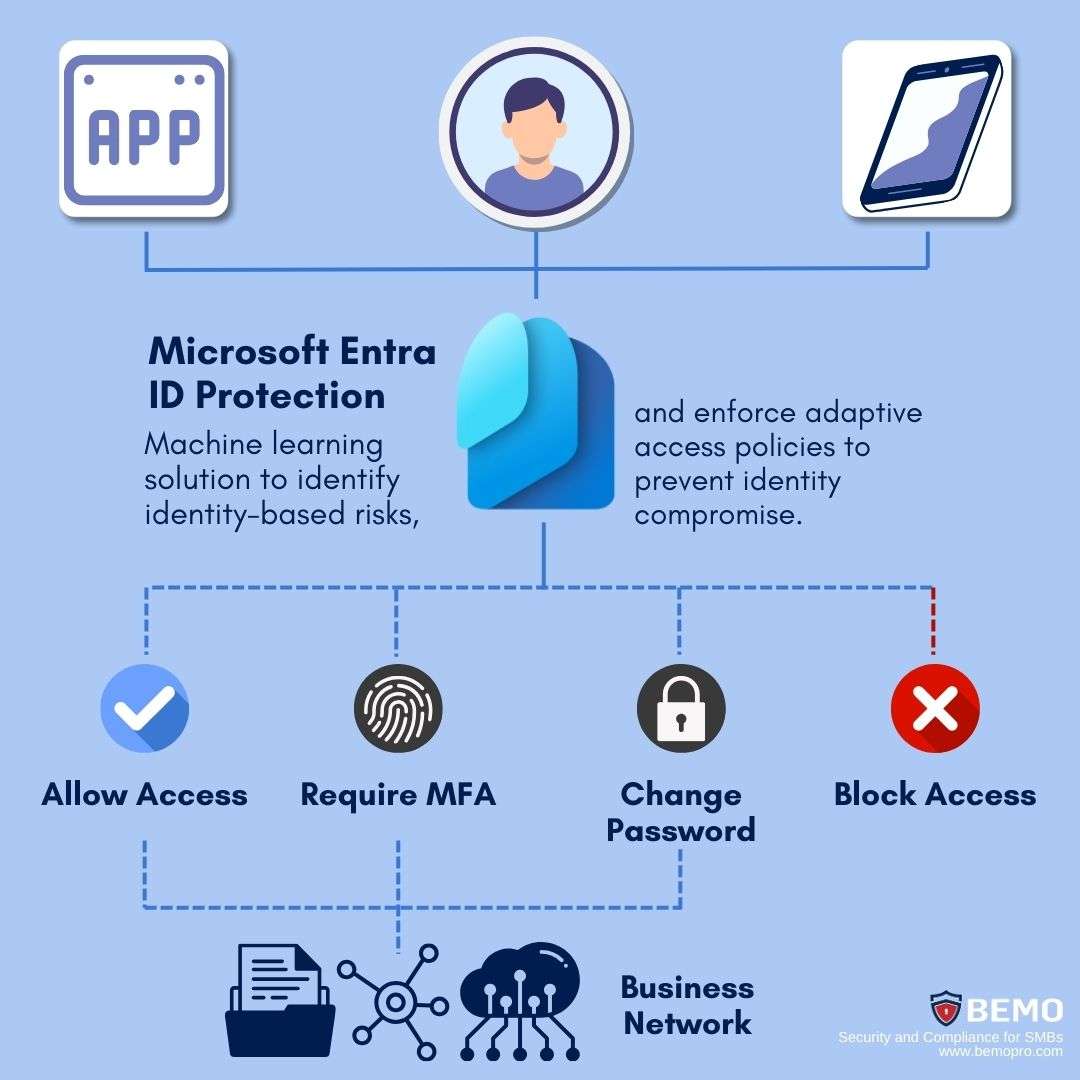
Entra ID protection, previously known as Azure AD Identity Protection, is a tool that uses advanced machine learning and connected intelligence to automate remediation and identify identity–based risks to block, challenge, limit, or allow access.
Entra doesn't just stop at preventing identity compromise by identifying threats and enforcing adaptive access policies based on risk. Beyond that, it offers a centralized control plane for reviewing insightful signals and reports, and the recognized risks seamlessly integrate into tools like Conditional Access, ensuring well-informed access decisions.
Furthermore, these risks can be fed into a Security Information and Event Management (SIEM) tool, enabling thorough investigation and response by your Security Operations Team
For more details on how Microsoft Entra ID Protection helps you quickly and effectively prevent identity compromise Click to watch the video.
Risk Detection and Investigation
ID Protection draws information from the sign-in activities of individual users. As it processes this data, it learns the typical patterns, including the paths taken and associated policies to determine the probability that a given authentication request isn't the authorized identity owner but a disguised attacker.
Risk can be detected at the User and Sign-in level. Additionally, there are two methods, or modes, of detection and calculation available: Real-time (as the event occurs it will reflect after a few minutes) and Offline (outside of real-time, shown by analyzing historical data or batches of information after the fact).
We will mention a few risk detections; if you’d like to dig deeper and review a complete list, click here.
User Risk Policy vs Sign in Policy
“If users are the ones doing the sign-ins, aren’t these policies the same?” It might be confusing at first, but our goal in this article is to simplify these concepts for you.
No, contrary to initial impressions, user risk and sign-in risk are not interchangeable terms. Let's delve into the nuances and clarify these distinctions.
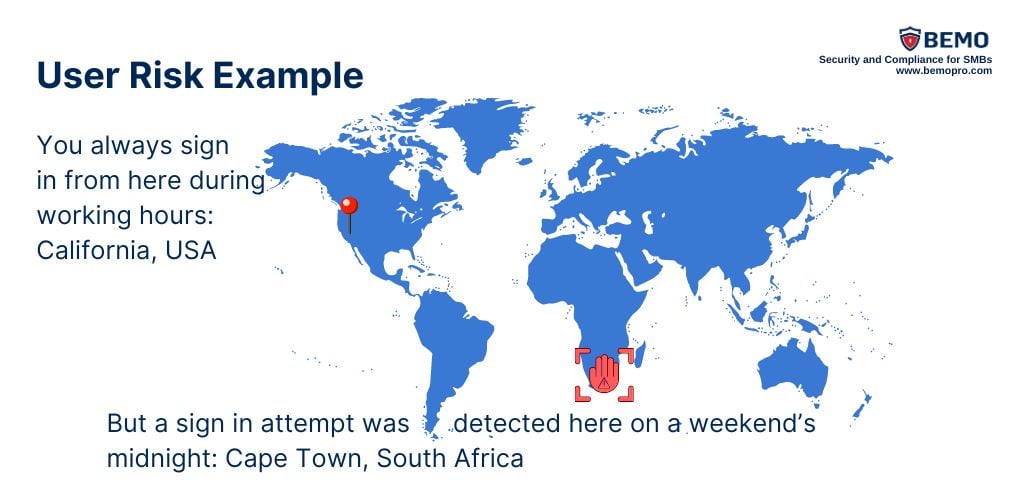
- User Risk Policies look at the overall behavior of a user to detect any unusual patterns that might indicate a compromised identity. For example, if a user typically logs in from a specific location during certain hours but suddenly attempts to log in from a completely different location at an odd time, the User Risk Policy might flag this as a potential risk that the specific identity has been compromised.
- Sign-in Policies focus on individual login attempts' details. For instance, if there's an attempt to log in with an incorrect password multiple times within a short period, the Sign-in Policy might trigger alerts or additional security measures to ensure the legitimacy of the authentication request.
Leaked Credentials
Through password hashes, Entra ID protection can tell if your employee's credentials were leaked on the internet or are being sold on the dark web. A password hash is a cryptographic representation of a password, and by comparing the hashes, a system can identify instances where the password has been leaked or compromised. (These calculations are done offline).
And on top of that, if an employee tries to change their password to one that Microsoft knows has already been leaked, then the system won't allow that employee to choose that password.
This tool gives IT admins a lot of insight into their users and gives them the ability to create automated workflows if risk events do occur, both minimizing the work for IT staff and reducing the opportunity for hackers to play on your network.
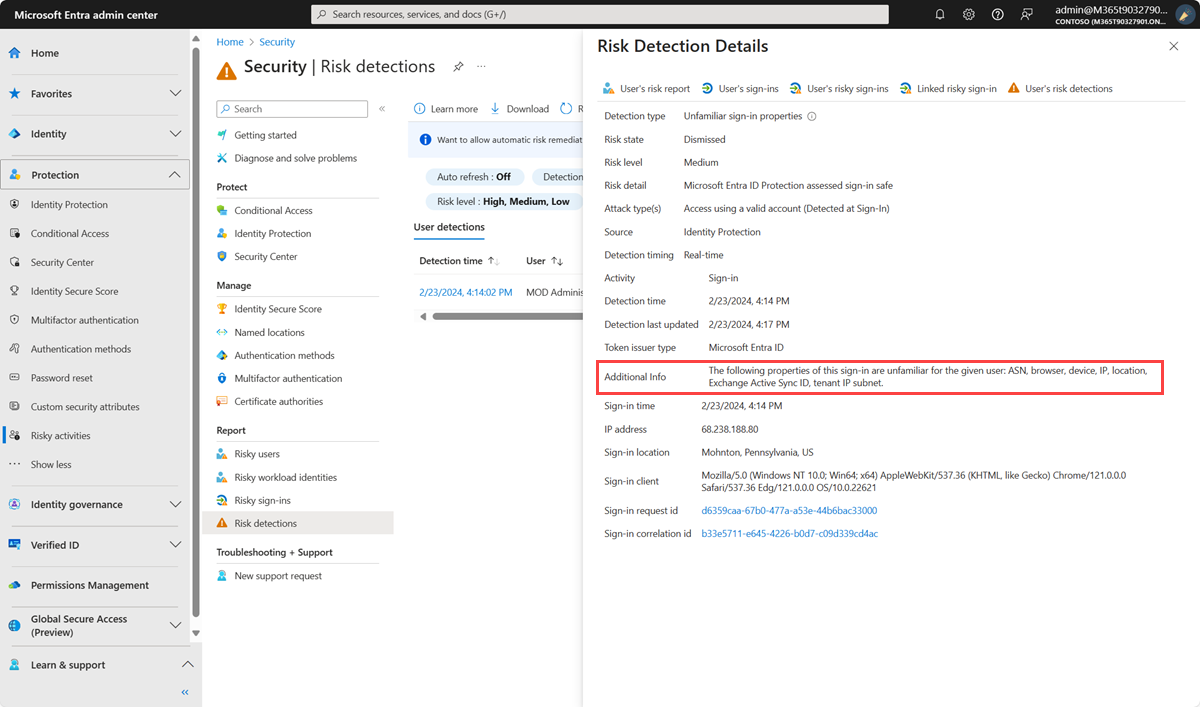
Unfamiliar Sign-in Properties
This type of risk detection happens in real-time by examining past sign-in history to identify unusual sign-ins. It only takes 5 days for the algorithm to gather enough information about the user's sign-in patterns!
The system stores information about previous logins and triggers a risk alert when a login has characteristics unfamiliar to the user, such as a different IP address, location, device, browser, etc.
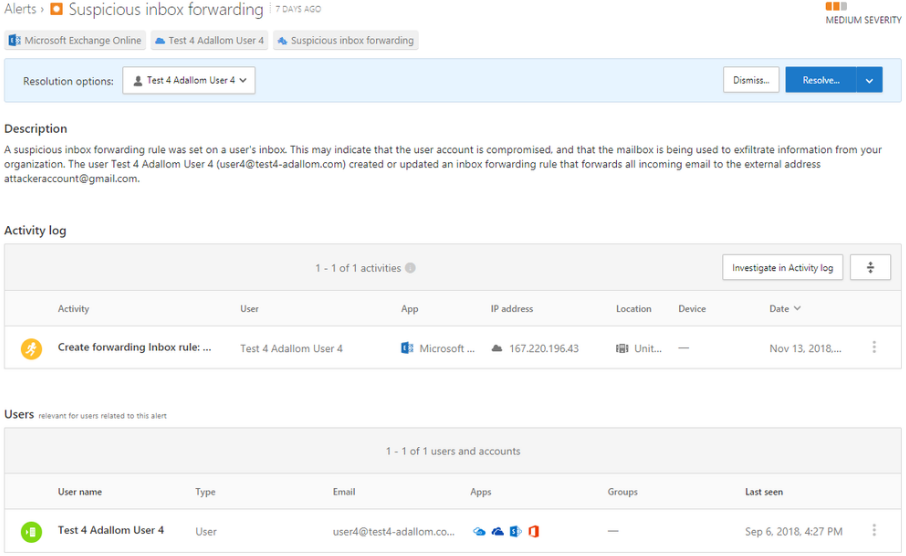
Suspicious Inbox Manipulation Rules
This risk detection keeps an eye on your email inbox for any fishy business. It looks out for unusual changes to your email rules that control how messages are managed. If someone is messing around with these rules in a way that seems off, the system flags it as a potential risk.
For example, if suspicious rules are established, like deleting or relocating messages or folders in a user's inbox, it prompts an offline alert. This allows you to catch anyone trying to compromise your account, send spam or malware in your organization or hide messages.
Malware Linked IP Address
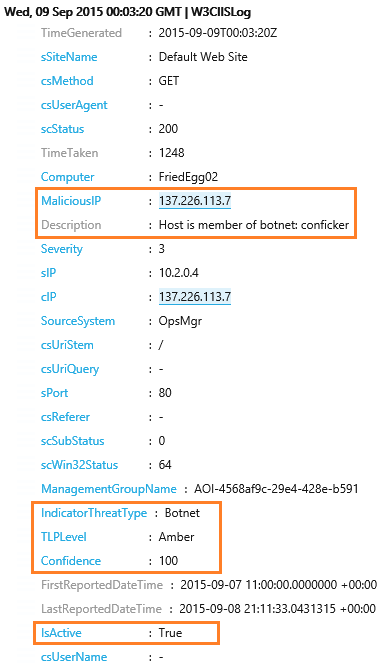 This offline detection mechanism operates on the premise that if your identity's IP address has a history of being in contact with a recognized bot online, it is treated as potentially infected with malware.
This offline detection mechanism operates on the premise that if your identity's IP address has a history of being in contact with a recognized bot online, it is treated as potentially infected with malware.
For instance, in the context of Bring Your Own Device (BYOD) or remote workers and contractors, if they connect remotely to the organizational network, and the device's IP address is flagged for past association with a known bot, it raises concerns. This scenario could indicate that the device, and by extension, the user's identity, might unknowingly harbor malware.
How to Get Entra ID Protection
To integrate Entra ID Protection into your organization, you will need Microsoft Entra ID P2 or Microsoft 365 E5. Entra ID Protection offers powerful Risk Detection and Investigation capabilities, but it's not just about detecting risks - it's about understanding their significance and taking informed action.
It’s no good to know that something is happening if there is no plan on how to fix it. It'd be like catching a whiff of something burning in the kitchen and just hoping the house won't go up in flames. You should check it out, grab a fire extinguisher, or dial up the fire department, depending on how bad it is.
We get that some people might want to look the other way (“out of sight, out of mind” mentality) - but not you! That’s where we want to help you.
We can assess the situation and react to it so that you don’t find yourself in this situation:

No way, it is NOT fine!
That's why for a streamlined process, enhanced cybersecurity measures, and additional benefits, consider acquiring these licenses through BEMO. By choosing BEMO as your provider, you can complement Entra ID Protection with one of our comprehensive cybersecurity solutions, creating a powerful duo.
Our expert team takes charge of deploying and monitoring the security features on your behalf, ensuring a seamless integration into your existing infrastructure.
Furthermore, BEMO goes beyond just security support, offering break-fix assistance for your Office Suite, ensuring a holistic approach to your organization's digital well-being.

Explore our Silver Solution, as a starting point, and as your business grows and needs evolve, you can seamlessly level up to our Gold or Platinum packages.
Read more about Silver Cybersecurity here.
This scalable approach allows your organization to adapt to changing requirements while maintaining a robust cybersecurity framework. What are you waiting for? Let’s talk!
Top 10 Posts
-
Windows 10 Pro vs Enterprise
-
Migrate From Gmail to Office 365: Step-By-Step Guide
-
Windows 10 Enterprise E3 vs E5: What's the Difference?
-
What are the 4 types of Microsoft Active Directory?
-
How to Migrate from GoDaddy to Office 365
-
Google Workspace to Office 365 Migration: A Step-by-Step Guide
-
How to Set Up Office 365 Advanced Threat Protection
-
10 Benefits of Microsoft Teams
-
Top 3 Reasons to Move From Google Drive to Microsoft OneDrive
-
How to remove Office 365 from GoDaddy (tips and tricks)
-2.png?width=1080&height=1080&name=Untitled%20design%20(5)-2.png)





Leave us a comment!