In an age where data security is paramount, SOC 2 compliance is a critical framework for businesses handling sensitive information. SOC 2 compliance involves a rigorous evaluation of a company's controls and processes related to data security, availability, processing integrity, confidentiality, and privacy.
However, misconceptions surrounding SOC 2 compliance abound, potentially leading businesses astray. We're here to bust some common myths about SOC 2 and shed light on what it's all about.
So, grab a comfy chair and a snack because we're diving into the fascinating world of SOC 2!
- What is SOC 2?
- Myth 1: SOC 2 is a Certification
- Myth 2: You can use Your Vendor's SOC 2 Report
- Myth 3: Auditors Want to Fail You
- Myth 4: SOC 2 is a One-Size-Fits-All Checklist
- Myth 5: SOC 2 Can Be Achieved in a Couple of Weeks
- How to Achieve SOC 2 Compliance
What is SOC 2?
Before we delve into debunking the myths surrounding SOC 2 compliance, let's briefly define what it entails. SOC 2 is a crucial report for organizations that store, process, or transmit sensitive information, such as customer financial data or healthcare records.
SOC 2 compliance demonstrates a company's commitment to safeguarding this information and ensuring that it remains secure and confidential.

Myth 1: SOC 2 is a Certification
Let's get this straight right off the bat: in reality, SOC 2 is a comprehensive report or attestation, not a certification. But what's the difference? The fundamental distinction between the two lies in their nature and purpose.
Certification implies that an entity has achieved a predefined set of standards, akin to receiving a diploma after completing an educational program. It is a formal qualification that is recognized by an accredited body, such as ISO 27001 or PCI-DSS. In simpler terms, certification means you’ve passed all the required classes (framework criteria) and now you receive your diploma (official certification).
In contrast, SOC 2 attestation means that an organization has undergone an independent audit by a qualified CPA firm, and has received a report that describes the state of its controls and practices related to security, availability, processing integrity, confidentiality, and privacy.
The report does not certify anything, but rather provides evidence and assurance to the users of the organization's services. It is more like a detailed report card that shows how well your company manages its data security (and where it might need some additional work). It describes the controls in place and how well they are working.

SOC 2 is not about being certified but about understanding and improving your organization's data security practices. Therefore, it is more accurate and appropriate to say that an organization has received a SOC 2 attestation, rather than a SOC 2 certification.
So, if someone claims they have a "SOC 2 certification", or they offer to “help you with your SOC 2 certification”, they might have a fundamental misunderstanding of what SOC 2 is and does!
Myth 2: You Can Use Your Vendor's SOC 2 Report
Imagine you’re dining at a restaurant. The restaurant sources its ingredients from various suppliers, each of whom follows strict food safety guidelines. These guidelines ensure that the suppliers handle and process their food products safely and hygienically.
However, as a diner, you’re not just interested in the safety of the individual ingredients. You’re interested in the overall safety of the meal served to you. This includes how the ingredients are stored at the restaurant, how they’re cooked, and how they’re served. For this, you rely on the restaurant’s own adherence to food safety guidelines, which assures that the restaurant follows safe practices in all these areas.
Similarly, an organization might use various vendors (the “suppliers”) each with their own SOC 2 reports (the “food safety guidelines”). However, these reports only cover the services provided by each individual vendor. They don’t cover how the organization (the “restaurant”) uses these services, integrates them into its operations, and manages overall risks.
Your vendor's SOC 2 report only covers the scope of their services, not yours. It does not reflect how you use, manage, protect and monitor the data that you receive from your customers or pass on to your vendor.
Now, while partnering with vendors who have SOC 2 attestations is undoubtedly beneficial, it doesn't absolve your organization from undergoing its independent SOC 2 audit.
If you want to build trust and credibility with your customers, you need to undergo your own SOC 2 audit and obtain your own SOC 2 report that covers the scope of your services and the risks that are relevant to your data. This will also help you identify and address any gaps or weaknesses in your data protection processes and improve your overall service quality and performance.
(Check our article "How to Review Your Vendor's SOC 2 Report" to know how to choose the best partners, and understand what others look for in your own report!)
Myth 3: Auditors Want to Fail You
“Auditors are adversaries hell-bent on uncovering deficiencies” This misconception couldn't be further from the truth. We get it; audits can be intimidating. But here's the thing: auditors aren't the bad guys. They're more like helpful coaches.
If you treat them as an enemy, you might be tempted to lie, hide, or manipulate information to pass the audit. This is not only unethical, but also risky! And, as we learned in Myth #1, SOC 2 is not a pass/fail exam.
The auditor’s goal isn't to catch you off guard but to work with you. Auditors collaborate with companies to ensure that audit procedures go smoothly. They want you to succeed and meet the SOC 2 standards. They bring expertise and objectivity to the table, helping you identify areas for improvement and ultimately enhancing your data security posture.
Myth 4: SOC 2 is a One-Size-Fits-All Checklist
SOC 2 compliance is often misunderstood as a rigid, one-size-fits-all checklist of controls that organizations must adhere to. In reality, SOC 2 compliance is a flexible framework that adapts to the unique needs and circumstances of each organization.
Imagine SOC 2 as a puzzle, but instead of a single, predetermined image, it can take various forms depending on your organization and the chosen Trust Service Categories (TSCs). While there are foundational controls that should be in place, the beauty of SOC 2 lies in its adaptability. Organizations must tailor their controls to align with their specific risks and requirements.
For example, let’s consider a company that operates entirely in the cloud and doesn’t have any physical servers or data centers. One of the common controls in SOC 2 is the management of physical security, which includes controls around secure access to data centers, surveillance systems, and environmental protections like fire suppression systems.
However, for a company that operates entirely in the cloud and doesn’t own any physical servers or data centers, this control might not apply. Instead, they would rely on the physical security controls of their cloud service provider and focus more on controls related to data access management, encryption, and secure software development within their cloud environment.
Certainly, having a checklist for the basics is a helpful starting point, but it should not be mistaken for the entirety of SOC 2 compliance. Flexibility and customization are essential elements in crafting an effective SOC 2 compliance strategy.
Myth 5: SOC 2 Can Be Achieved in a Couple of Weeks
If you think you can achieve SOC 2 compliance in a couple of weeks, think again. It's more like a marathon than a sprint.
The timeline for attaining SOC 2 compliance varies depending on several factors, including the complexity of your organization and the type of audit you pursue (Type 1 or Type 2).
For example, a Type 1 audit may take from 3 to 6 months and a Type 2 audit a year or more.
To make the initial necessary adjustments to meet the framework's requirements, you’ll need a preliminary preparation period (1- 2 months) and a readiness assessment of another 2 months, to identify any gaps and prepare the organization for the audit. This will give you the chance to implement all controls and build up a strong security program, as well as document all policies, procedures and evidence that must be handed to the auditor. 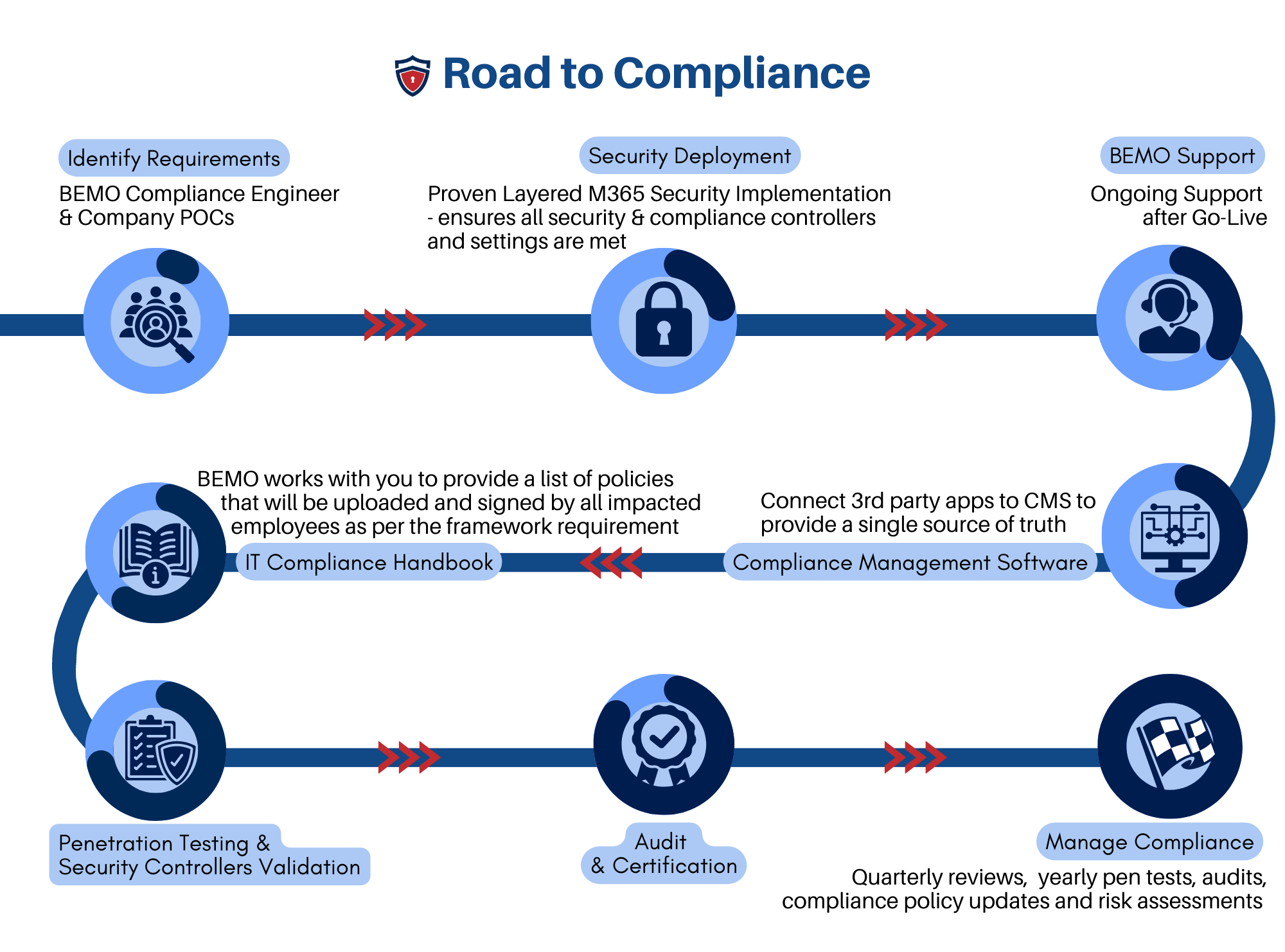
It’s only once you’re in month 4 or so that you can officially kick-off the audit itself. During this time (which can stretch anywhere from 3 to 12 months depending on what you’re testing) the audit firm will evaluate the controls in place and assess their design and effectiveness.
Lastly the auditors must compile their findings and generate the SOC 2 report.
So, don't rush it; take the time you need to ensure your data security is rock-solid.
How to Achieve SOC 2 Compliance
Understanding that SOC 2 is not a certification, recognizing the importance of independent audits, appreciating the collaborative role of auditors, acknowledging the flexibility of SOC 2 controls, and embracing the time-intensive nature of compliance are vital steps toward effectively navigating the world of SOC 2.
Now that you're armed with the truth about SOC 2, you might be wondering, "How can I make sure my organization is SOC 2 compliant?"
Reach out to BEMO for expert help in achieving SOC 2 compliance! Our experienced team stands ready to guide you through the complexities of SOC 2 compliance, ensuring that your organization's data remains secure, and your compliance efforts are both effective and efficient.
If your plate is full and you need help with your Microsoft365 cloud security and SOC 2 compliance, contact our BEMO Security and Compliance Experts. For more information on what SOC 2 Compliance with BEMO is like, download our one-pager here.
Or fill out the following form to get your copy of our eBook - The Ultimate Guide to SOC 2. Get actionable tips on how to make your compliance journey smoother!

Free Download - The Ultimate Guide to SOC 2
Top 10 Posts
-
Google Workspace to Office 365 Migration: A Step-by-Step Guide
-
Office 365 MFA Setup: Step-by-Step Instructions
-
How to Migrate from GoDaddy to Office 365
-
Migrate From Gmail to Office 365: 2024 Guide
-
CMMC Meaning : A Comprehensive Guide for Startups
-
How to remove Office 365 from GoDaddy (tips and tricks)
-
What is Microsoft Purview ? Your A to Z Guide to Getting Secure Fast
-
What is The CIA Triad?
-
How to Set Up Office Message Encryption (OME)
-
What are the 4 types of Microsoft Active Directory?


Leave us a comment!