
The phrase "your cybersecurity is only as strong as your weakest link" is more than a mere saying; it holds a profound truth. You might believe your internal processes are locked up tighter than a vault, but what about those external partners?
Don't assume they're on the same security level as your organization; one of them might just be the weak link we're talking about.
As your business grows, it's only natural for it to increasingly lean on third-party services, whether it's your software provider, equipment manufacturer, or service provider.
Your company's future is intricately intertwined with the vendors you do business with. That’s why understanding a vendor's SOC 2 report is a big deal.
Just as you're held to SOC standards by your customers, turnabout is fair play. As a customer yourself, it's only fair to toss those same questions back at the third parties powering your corporate engines. It's an intricate tango of standards and inquiries, ensuring a robust cybersecurity posture for all involved.
In this blog post you’ll get the answers to the following questions:
- What is an SOC Report?
- Why is it Important to Review Your Vendor’s SOC 2 Report?
- What Does a SOC 2 Report Contain?
- How to Review a SOC 2 Report?
- Frequently Asked Questions (FAQs)
What is an SOC report?
Your company’s management asserts that certain internal controls related to security, availability, processing integrity, confidentiality, and privacy of data have been implemented. But how can you prove those assertions? That’s where SOC 2 comes in.
A SOC (Service Organization Control) report is a comprehensive document that details the internal controls and processes of a service organization after undergoing an audit process conducted by a qualified CPA (Certified Public Accountant) firm.
The report is basically an attestation that details the work done by the CPA assessor and assures clients, stakeholders, and other interested parties about the effectiveness of the organization's controls.
Keep in mind that there are various SOC reports, and in this article, our spotlight will be on SOC 2 compliance. However, it's beneficial for your overall understanding to be aware of the other types:
- SOC 1 focuses on the financial reporting controls of the service organization.
- SOC 2 addresses controls related to the security, availability, processing integrity, confidentiality, and privacy of the service organization.
-
- SOC 2 Type 1 reports evaluate a company’s controls at a single point in time – think of it as a snapshot.
-
- SOC 2 Type 2 reports assess how those controls function over a period, generally 3-12 months.
.png?width=670&height=327&name=soc%202%20type%201%20and%20type%202%20differences%20(1).png)
For more in-depth information, read our article “What is the Difference Between SOC 2 Type 1 and Type 2?”.
- SOC 2 Type 2 reports assess how those controls function over a period, generally 3-12 months.
- SOC 3 summarizes the SOC 2 report, but it excludes the description of the auditor’s testing or the results of the testing.
- SOC for Cybersecurity: Concentrates on evaluating an organization's cybersecurity risk management program.
- SOC for Supply Chains: Offers assurance about the security and reliability of controls implemented within supply chain processes.
Why is it Important to Review Your Vendors’ SOC 2 Report?
Think of SOC 2 reports as the "nutrition labels" for your vendors. Just like how you check food labels to know what you're consuming, reviewing their SOC 2 report gives you a detailed breakdown of how they manage and protect your data. 
It's your way of ensuring that the "ingredients" (security measures, privacy, data handling processes, etc.) meet the standards you expect. By doing this, you empower yourself to make well-informed decisions when evaluating vendors and selecting your business partners.
Taking this matter seriously is crucial because, as previously emphasized, you are directly linked and affected by your vendors. Picture this: a vendor neglects proper measures, succumbs to a data breach, and exposes sensitive information. This not only jeopardizes their reputation but also tarnishes your standing in the eyes of your customers. Vigilance in vendor scrutiny is, therefore, an investment in your own credibility, compliance, and security.
What Does a SOC 2 Report Contain?
Now that you've grasped the nuances of the different SOC reports, the focus of SOC 2 compliance, and recognize the importance of reviewing your vendor’s SOC 2 report, there’s one final stride before we delve into the art or report reviewing.
Let’s get you familiarized with the anatomy of the soc 2 report to answer what is in a SOC 2 report once and for all. The following sections or chapters form the backbone of a SOC 2 report: 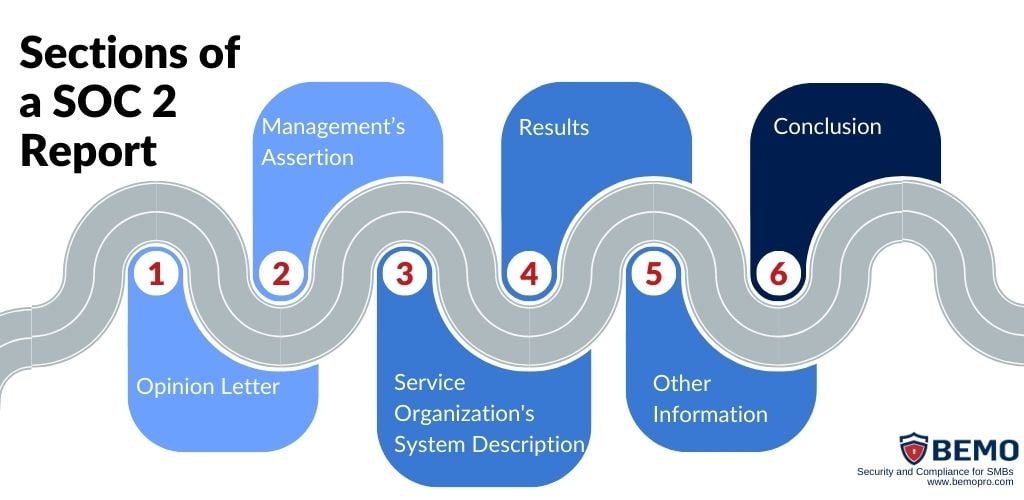
-
Opinion Letter (Auditor’s Report):
provides a summary of the audit and highlights key details like the scope of the audit, the period covered, the auditor’s opinion on your vendor’s security controls and criteria, and any other relevant findings.

There are 4 possible opinions stated in this section:
| Opinion Status | Meaning |
|---|---|
Unqualified (Clean) 😃 |
Indicates that the organization's controls are suitably designed and effectively operated to meet the specified criteria. No significant issues or deficiencies are identified. |
Qualified 🙂 |
This opinion is issued when there are some limitations or exceptions in the controls. It suggests that, while most controls are effective, there are specific areas where improvements are needed, or certain criteria are not met. |
Adverse 😕 |
An adverse opinion is the most critical. It means there are significant deficiencies or failures, raising concerns about how the organization's controls are not designed or operating effectively to meet the specified criteria. |
Disclaimer 🤔 |
This opinion is issued when the auditor is unable to form an opinion due to significant limitations or uncertainties in the examination. It may occur if the auditor lacks sufficient information or encounters obstacles that prevent a thorough assessment. |
The auditor summary may state that the "controls operated effectively" but there may be details further down in the report that suggest areas of improvement. It would be important to analyze those to see if they are areas of concern.
2. Management's Assertion:
This section is a statement from the management of the service organization asserting their adherence to the defined Trust Services Criteria (TSC).
3. Service Organization's System Description:
Gives you more detailed information about the systems, infrastructure, and processes relevant to the security, availability, processing integrity, confidentiality, and privacy of data.
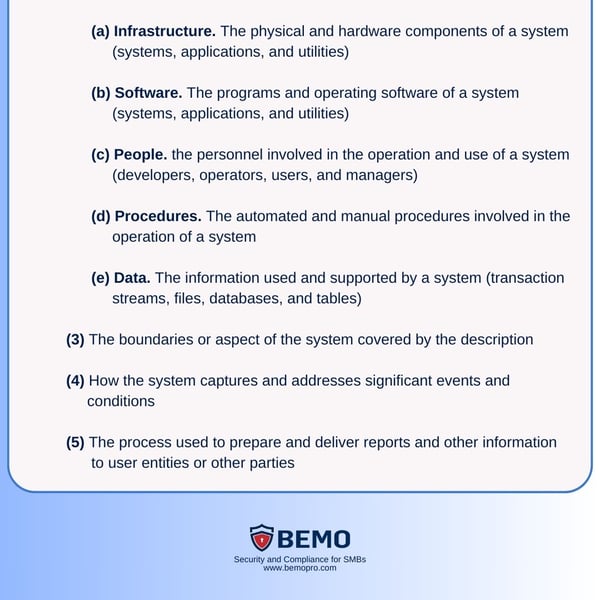
a. Control Objectives and Descriptions: identifies and explains the control objectives and related activities implemented to address the TSC.
b. Control Testing: describes the methods used to test the effectiveness of the implemented controls, and the results of the testing, including any identified issues or exceptions.
4. Results:
This chapter highlights the results of the control testing and assessments, often in the form of a summary or opinion.
5. Other Information:
Here you can find additional relevant information, such as complementary user entity controls, third-party certifications, or any supplementary information or disclosures deemed necessary for a comprehensive understanding of the SOC 2 report.
6.Conclusion:
Includes the overall conclusion, opinion, or summary regarding the service organization's adherence to the TSC.
You can click here to see an Illustrative Type 2 SOC 2 Report from AICPA.
How to Review a SOC 2 Report:
Step 1: Understand your Vendor’s Scope and Objectives
Begin by grasping what aspects the vendor's SOC 2 report covers: the audit scope, objectives, and the period covered. (This last one is crucial to make sure it is a recent version that properly gives you an insight in the current state of your vendor’s controls)
Examine the control objectives to ensure they align with the services this vendor provides to your business.
Step 2: Assess the Management’s Assertion
In this section, the vendor's management formally asserts its responsibility for the design and operating effectiveness of controls.
Ensure that the management's assertion is clear, comprehensive, and aligns with the scope and objectives of the SOC 2 examination. 
Step 3: Evaluate Control Descriptions
Carefully review the system description section to understand the architecture of the vendor's systems and the services provided. Here you’ll get an idea of any system boundaries, if your vendor’s third parties affect your risk management, etc.
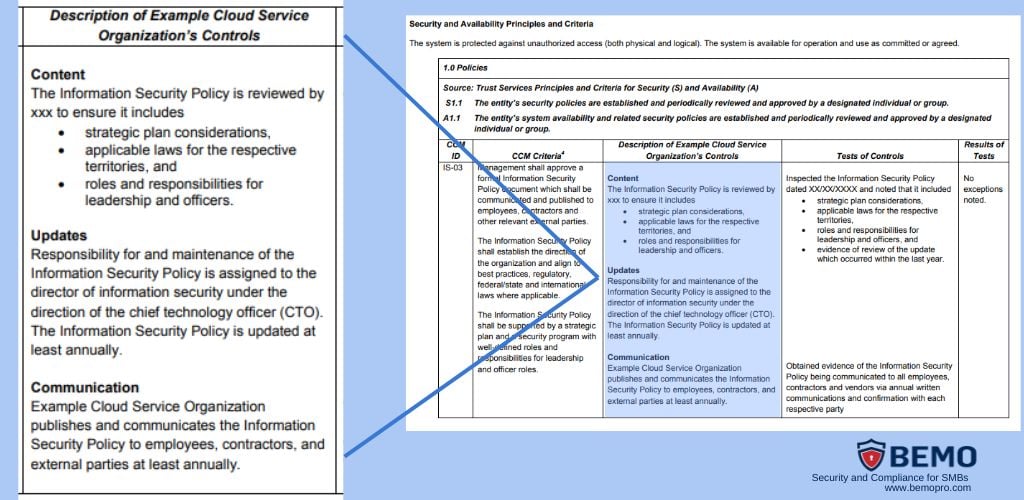
Step 4: Examine Control Environment and Control Objectives:
Check the control environment, which outlines the policies and procedures the vendor has in place to achieve its objectives. Ensure that these policies align with your expectations and industry standards.
Evaluate the control objectives and activities to verify that they address the key security and compliance requirements relevant to your organization.
Step 5: Analyze the Testing of Controls
Assess the results of the testing of controls section, where the auditor provides details on the testing performed to validate the effectiveness of the controls.
Verify that the testing is thorough and covers a representative sample of the controls.
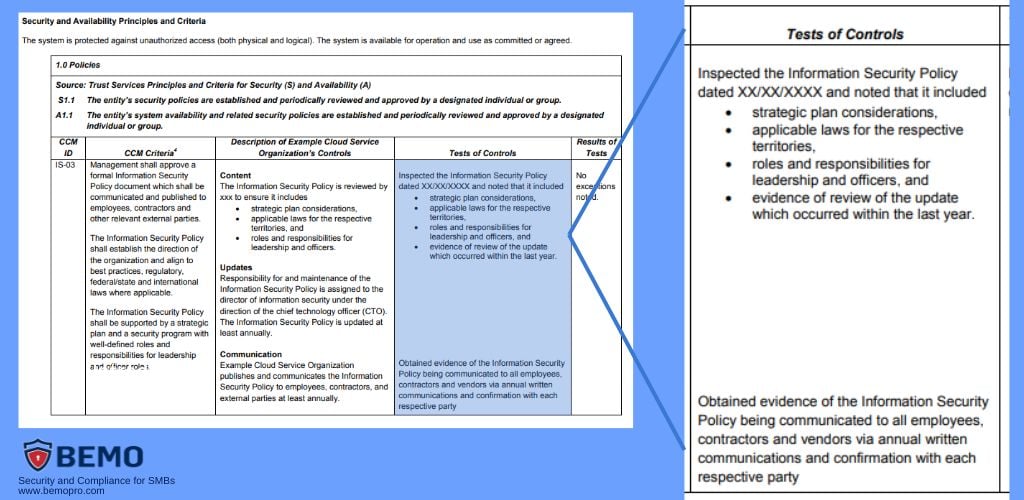
PRO TIP: Don’t forget to review the Results of Tests column to check for any identified exceptions or issues and assess their significance!
Step 6: Compare with your Organization’s Requirements and reach a final decision
Evaluate if the findings in the vendor's SOC 2 report align with your organization's security, compliance, and risk management requirements. Consider the sensitivity of the data involved and how well the vendor's controls and processes match the services they provide.
Frequently Asked Questions - FAQs
-
Can I use my vendor's SOC 2 report to guarantee my own compliance?
No. While you can use your vendor's report as part of your risk management strategy, it doesn't automatically ensure your own compliance.
SOC 2 assessments are specific to each organization and its unique controls, meaning you need to conduct your own SOC 2 audit to evaluate the effectiveness of your controls.
If you need help achieving your SOC 2 attestation, contact us or learn more about this compliance framework here. -
How long is a SOC 2 report valid for?
A SOC 2 report is valid for one year. This periodic audit ensures that the information provided in the report remains current and relevant.
-
How frequently should I assess my vendors' SOC 2 reports?
The frequency of reviewing your vendor's SOC 2 report is at your discretion. While most organizations release reports annually, some opt for more frequent intervals like six months or three months.
We recommend an annual review for each vendor.
-
Can I rely solely on a vendor's SOC 2 report to assess their security posture?
While SOC 2 reports provide valuable insights, it's recommended to complement this with other assessments, like penetration testing or on-site visits, to gain a more comprehensive understanding of a vendor's security measures.
SOC 2 focuses on controls at a specific point in time, and additional assessments enhance your overall risk management strategy.
-
How should I handle the gap between the reporting period and my organization's year-end?
If there's a gap, your vendor's management might issue a SOC 2 Bridge Letter, addressing material changes post-reporting period.
Review both the letter and the SOC report to stay informed about any changes.
-
I found exceptions in the report that weren't adequately addressed. What should I do?
If the SOC report contains exceptions that concern you, reach out to your vendor to understand the measures they've taken post-audit to address your concerns.
-
What happens if a vendor doesn't have a SOC 2 report?
If a vendor lacks a SOC 2 report, it's essential to assess their security practices through other means.
Request information on their security measures, policies, and procedures to ensure they align with industry standards. You may also consider discussing the possibility of the vendor undergoing a SOC 2 assessment to provide additional assurance.
You can even share with them this article as a source to educate them on the importance of achieving SOC 2 and providing clients their report!
Top 10 Posts
-
Google Workspace to Office 365 Migration: A Step-by-Step Guide
-
Office 365 MFA Setup: Step-by-Step Instructions
-
How to Migrate from GoDaddy to Office 365
-
Migrate From Gmail to Office 365: 2024 Guide
-
CMMC Meaning : A Comprehensive Guide for Startups
-
How to remove Office 365 from GoDaddy (tips and tricks)
-
What is Microsoft Purview ? Your A to Z Guide to Getting Secure Fast
-
What is The CIA Triad?
-
How to Set Up Office Message Encryption (OME)
-
What are the 4 types of Microsoft Active Directory?


Leave us a comment!