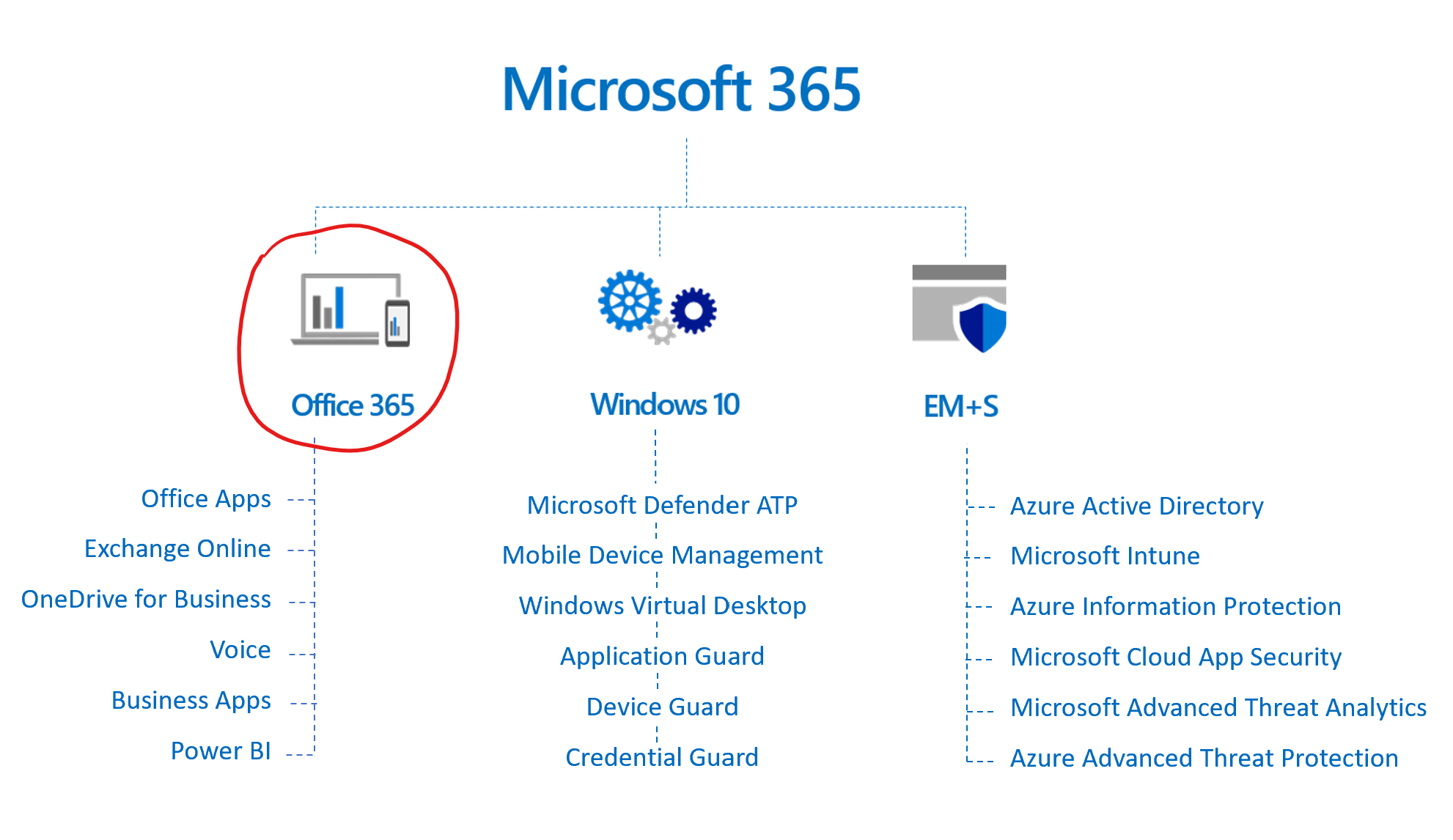
Microsoft 365 is a bundle of Office 365, Windows 10, and Enterprise Mobility + Security (EMS). Microsoft 365 is the parent product of Office 365 and was created to bundle all of Microsoft's 'a-la-cart' productivity, mobility, and security tools into one, so that as a customer you only have to think about buying one tool instead of educating yourself on the hundreds of different tools and features so you can choose between them.
In this blog, we will discuss the following:
Disclaimer 3/4/22: Microsoft is currently undergoing a transition for their pricing structure. Please check with your BEMO Rep for the most up-to-date, accurate pricing. We will continue to update the page as developments arise.
Microsoft 365 vs Office 365 Pricing
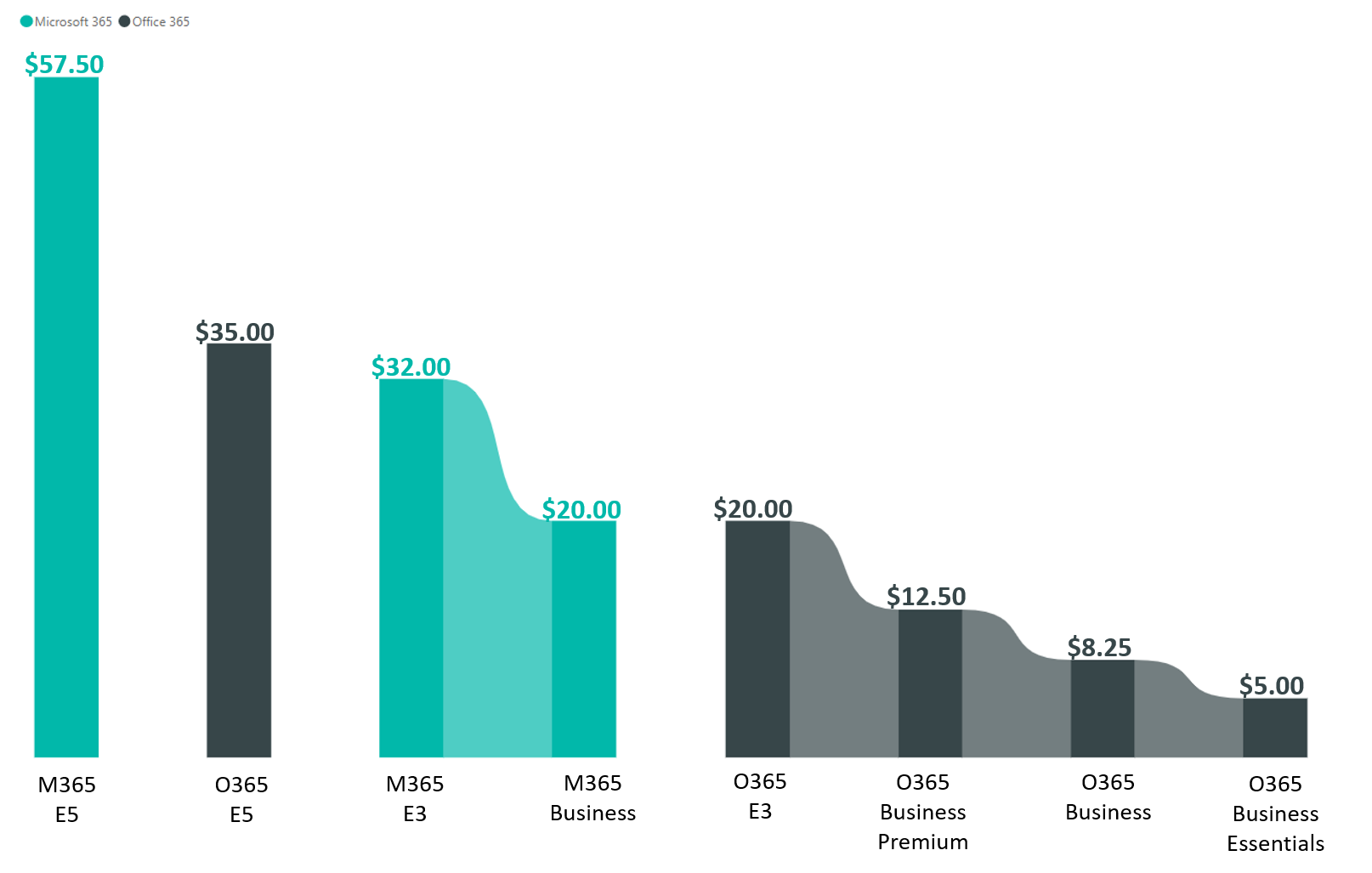
Across M365 (Microsoft 365) and O365 (Office 365) there are 8 licenses to choose from, ranging from $5.00 per user/month to $57.50 user/per month. The graph below describes the pricing difference across the 8 licenses:
The graphic below shows which licenses fall under the SMB and Enterprise categories. The licenses boxed by the grey dotted line are both the most popular licenses and the ones that bring up the most customer questions: Microsoft 365 Business Standard (formerly Office 365 Business Premium), Office 365 E3, and Microsoft 365 Business Premium (formerly known as Microsoft 365 Business).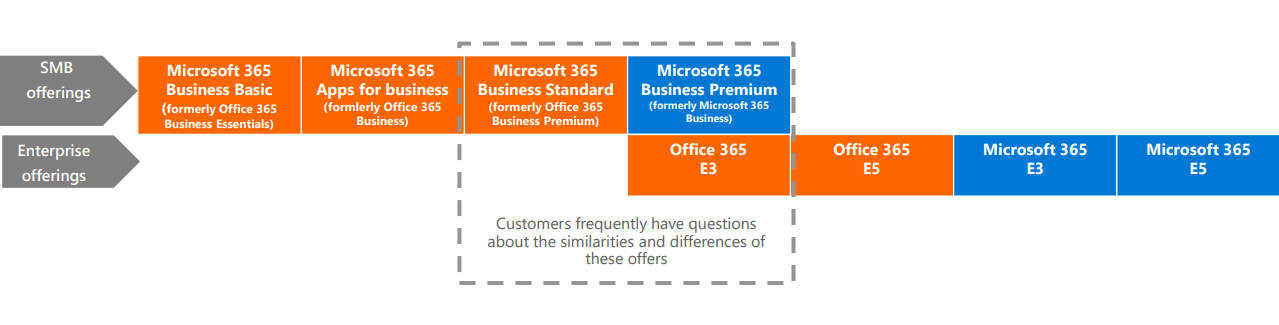
To see the specific feature differences across the licenses and understand why some are more expensive than others, then check out the O365/M365 Enterprise comparison table and the O365/M365 SMB comparison table.
For Microsoft's comparison deck of all these licenses, click the button below:
Microsoft 365 vs Office 365 Features
This blog post will not cover every single feature in Microsoft 365, but I will do my best to cover the 'big ticket' items. If you're looking for a more in-depth read, check out the following posts or reach out to us for more information:
- What is Microsoft EMS?
- Microsoft EMS E3 vs E5
- Office 365: E3 vs E5
- Office 365: Business Standard (Formerly Business Premium) vs E3
Ok, now that we've gotten the groundwork laid, we'll move on to the following videos and descriptions of the additional features you get with Microsoft 365 (that you don't have access to when just buying Office 365)
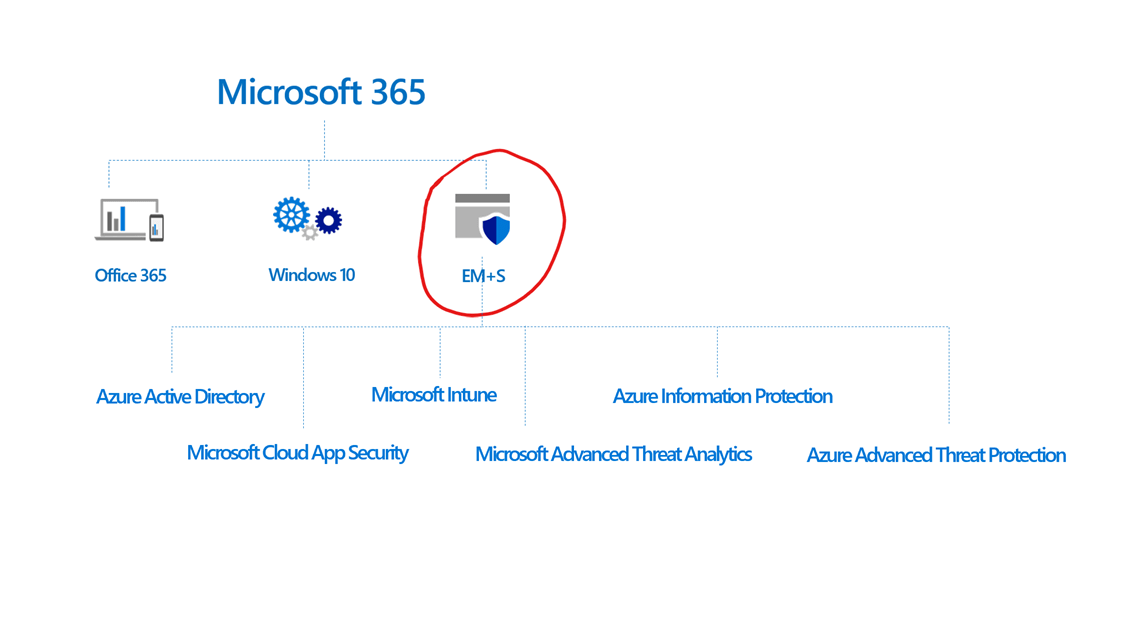
Enterprise Mobility + Security (EMS)
EMS is suite of 6 products that make it easier to centrally manage identities, data, and devices across an organization, all while staying secure from cyber attacks. Below I offer a high-level overview of these features. For an in-depth dive read our other blog post, What is Microsoft EMS? and for a comparison of EMS offerings, check out Microsoft EMS E3 vs E5.
Azure Active Directory
You may not even know you're using Azure AD, it runs in the background of Office 365 and Microsoft 365. It is the technology that manages the identities of all of your users, a.k.a. the thing that checks whether the credentials you wrote are correct or incorrect after you click 'login' to access an account or an app.
There are two Azure Active Directory licenses sold with EMS. EMS E3 comes with Azure AD Premium P1 and EMS E5 comes with Azure AD Premium P2. Read our Azure AD: Premium P1 v P2 blog post to learn about the specific feature differences between the two.
Microsoft Intune
Intune allows your company to finally have control over your company's data. With employees bringing their own devices to work, from their smartphones to their own laptops, it's easy to lose control over what is happening with your company data. Are employees saving company files on their laptops? Are your employees keeping their anti-malware up to date or are they streaming illegal movies online that could then affect your company files if malware is downloaded? Intune fixes those types of issues by setting company policies on rules on all devices housing your data.
Some things you can do with Microsoft Intune:
- Manage the mobile devices and PCs your workforce uses to access company data.
- Manage the mobile apps your workforce uses.
- Protect your company information by helping to control the way your workforce accesses and shares it.
- Ensure devices and apps are compliant with company security requirements.
The video above is a quick 15-minute demo of enabling and managing Intune. If you want an extensive walk-through of everything Intune has to offer, then watch the video below of the Ignite 2018 session.
Azure Information Protection
With AIP (Azure Information Protection), you can identity your company's sensitive data. Microsoft is smart in that it can detect things like credit card numbers and social security numbers written within a document automatically. AIP also allows you to create custom rules for identifying sensitive information, so you don't have to read every file. Once you've identified the sensitive data, you can classify it by labeling it 'secret' or 'sensitive' or one of the many out of the box labels Microsoft provides you. Then, you can apply protection policies, such as not allowing an employee to copy and paste from certain documents.
Or lets say the CEO accidentally sends an internal memo for the execs to the whole company. Even if the other employees receive the file, they won't be able to read it, unless they have the right credentials. Pretty cool, right? Watch the video below to see it in action.
Microsoft Cloud App Security
This tool is a Cloud Access Security Broker (CASB), which is necessary for IT compliance, configuring how your data travels, and for visibility into security threats across Microsoft and 3rd party apps.
The Microsoft technical documents describe the following uses cases for using Microsoft Cloud App Security:
-
Discover and control the use of Shadow IT: Identify the cloud apps, IaaS, and PaaS services used by your organization. Investigate usage patterns, assess the risk levels and business readiness of more than 16,000 SaaS apps against more than 80 risks. Start managing them to ensure security and compliance.
-
Protect your sensitive information anywhere in the cloud: Understand, classify, and protect the exposure of sensitive information at rest. Leverage out-of-the box policies and automated processes to apply controls in real-time across all your cloud apps.
-
Protect against cyberthreats and anomalies: Detect unusual behavior across cloud apps to identify ransomware, compromised users or rogue applications, analyze high-risk usage and remediate automatically to limit the risk to your organization.
-
Assess the compliance of your cloud apps: Assess if your cloud apps meet relevant compliance requirements including regulatory compliance and industry standards. Prevent data leaks to non-compliant apps, and limit access to regulated data.
Microsoft Advanced Threat Analytics
This is an on-premises platform that helps protect enterprises from advanced cyber-attacks and insider threat by leveraging port mirroring from domain controllers and DNS servers and through deploying the ATA Lightweight Gateway on top of your domain controller.
Azure Advanced Threat Protection
Azure ATP is meant to protect hybrid IT environments by leveraging on-premise infrastructure to identify, detect, and investigate advanced threats, compromised identities, and malicious insider actions directed at your organization. Microsoft technical docs give some of the following examples:
- Monitor users, entity behavior, and activities with learning-based analytics
- Protect user identities and credentials stored in Active Directory
- Identify and investigate suspicious user activities and advanced attacks throughout the kill chain
- Provide clear incident information on a simple timeline for fast triage
Windows 10 Enterprise
It's important to mention that while Microsoft 365 Business comes with upgrade rights from Windows 7/8.1 Pro, but the other licenses (Microsoft 365 E3 and E5) do not. Windows 10 Enterprise is actually a set of add-ons to Windows 10 Pro and does not replace Windows 10 Pro.
Microsoft Defender ATP
Not to be confused with Office 365 ATP (thanks Microsoft for the confusing naming conventions), Windows Defender works at the operating system level to detect breaches, investigate them, and respond automatically using machine learning and analytics to contain attacks on your computers. The dashboard will give your IT team insights into the types of malware detected, on which devices, and will tell you the users most at risk of attacks. Coupled by the intelligence aggregated from Microsoft's 1 billion devices using Windows, your anti-virus will continuously get smarter.
Windows Virtual Desktop (WVD)
WVD is the newest technology in virtualization and will eventually replace Virtual Desktop Infrastructure (VDI). Microsoft 365 gives you the rights to purchase and use WVD and VDI. You can hear BEMO's CEO talk about it in our interview, 5 Things To Know about Microsoft's 'Revolutionary' Windows Virtual Desktop with CRN.
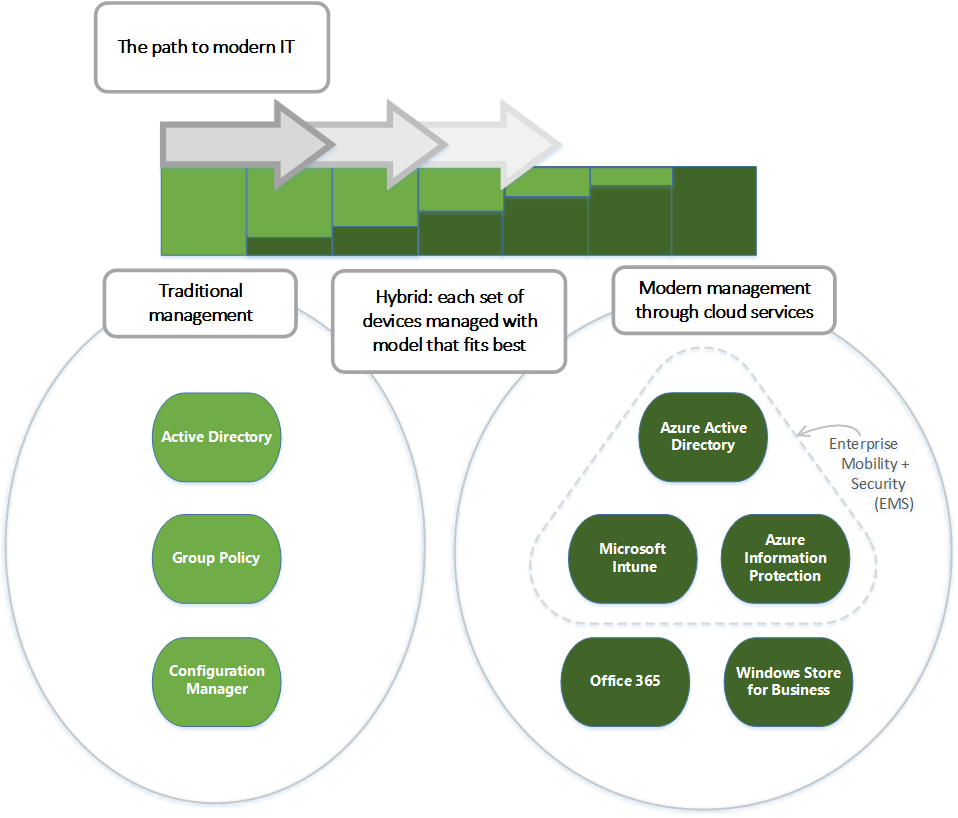
Mobile Device Management
IT used to have to use group policies, Active Directory, and Config Manager to manage PCs, but now IT can manage all devices with Microsoft MDM, using one interface. Microsoft MDM is a combination of EM+S, Office 365, and Windows Store for Business.
Application Guard
This tool stops browser-based attacks from ever reaching your operating system (Windows 10 Pro).
Device Guard
This tool allows IT to white-list the applications that can be run on a device. This means if a hacker were to gain control of the kernel/system level, they would have a much tougher time installing their own malicious code, as IT enumerated the specific applications that can be run. For more detail, read the Windows Defender Device guard technical document.
Credential Guard
This tool isolates your user's credentials from your operating system (Windows 10 Pro) to prevent credential theft via system-based attacks. This protects you from pass-the-hash and brute force attacks.
Wrap-Up
Whether you're choosing Office 365 and adding on a la carte options or streamlining with Microsoft 365, knowing what you do and don't need is key. Hopefully this article helped clear up the differences between Microsoft 365 and Office 365.
Questions? Our team is always happy to help solve your Microsoft and cybersecurity questions. Use the button below to schedule a free meeting:
Top 10 Posts
-
Google Workspace to Office 365 Migration: A Step-by-Step Guide
-
Office 365 MFA Setup: Step-by-Step Instructions
-
How to Migrate from GoDaddy to Office 365
-
Migrate From Gmail to Office 365: 2024 Guide
-
CMMC Meaning : A Comprehensive Guide for Startups
-
How to remove Office 365 from GoDaddy (tips and tricks)
-
What is Microsoft Purview ? Your A to Z Guide to Getting Secure Fast
-
What is The CIA Triad?
-
How to Set Up Office Message Encryption (OME)
-
What are the 4 types of Microsoft Active Directory?


Leave us a comment!