In our last blog post, What is Microsoft EMS? we gave an overview of the 6 tools that make up the Enterprise Mobility + Security suite. In this post we'll dive into the 13 specific differences between the Microsoft EMS E3 and E5 licenses, so that you can best decide which version fits your needs.
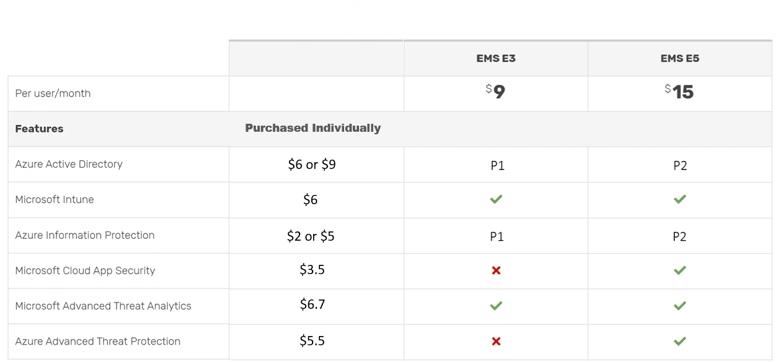
EMS E3 vs E5 Feature Differences
So what do you get for the extra $6 per user/month? With EMS E5 you get the following 13 additional features, the most important of which are highlighted:
- Vulnerabilities and Risky Accounts Detection
- Risk Events Investigation
- Risk-based conditional access policies
- Privileged Identity Management (PIM)
- Access Reviews
- Entitlement Management
- Configure conditions for automatic and recommended classification
- Set labels to automatically apply pre-configured S/MIME protection in Outlook
- Control oversharing of information when using Outlook (warn, justify or block emails)
- Hold Your Own Key (HYOK)
- AIP automated (instead of manual) classification, labeling, and protection
- Microsoft Cloud App Security
- Azure Advanced Threat Protection (ATP)
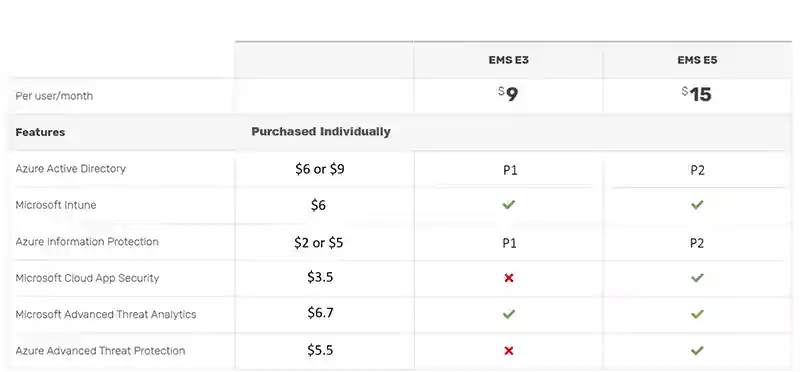
Azure AD: Premium P1 vs P2
Read the Azure AD: Premium P1 vs P2 blog post for the extensive list of features, as we'll only be talking about the 6 additional features you get from the Premium P2 license: vulnerabilities and risk accounts detection, risk events investigation, risk-based conditional access, privileged access management (PIM), access reviews, and entitlement management.
Vulnerabilities and Risky Accounts Detection
- Providing custom recommendations to improve overall security posture by highlighting vulnerabilities
- Calculating sign-in risk levels
- Calculating user risk levels
Here is the full list of vulnerabilities Azure can detect.
Risk Events Investigation
- Sending notifications for risk detections
- Investigating risk detections using relevant and contextual information
- Providing basic workflows to track investigations
- Providing easy access to remediation actions such as password reset
Here is a full list of the risk event types Azure can detect, it's really impressive.
Risk-Based Conditional Access
- Policy to mitigate risky sign-ins by blocking sign-ins or requiring multi-factor authentication challenges
- Policy to block or secure risky user accounts
- Policy to require users to register for multi-factor authentication
For example: you have an employee who is based out of New York City but suddenly Azure detects that that user is logging in from Buenos Aires. Azure can prompt that user to MFA or simply block their account and send a notification to an IT admin to look into the event.
Privileged Identity Management
This tool is especially crucial for IT admins in the company. PIM allows admins to elevate their privilege only when they need to do admin work and require MFA when doing such tasks. This means even if a privileged user's credentials are stolen, the hacker still cannot access the company's resources.
PIM helps you manage the who, what, when, where, and why for resources in Azure. Here are some of the key features of PIM:
- Provide just-in-time privileged access to Azure AD and Azure resources
- Assign time-bound access to resources using start and end dates
- Require approval to activate privileged roles
- Enforce multi-factor authentication to activate any role
- Use justification to understand why users activate
- Get notifications when privileged roles are activated
- Conduct access reviews to ensure users still need roles
- Download audit history for internal or external audit
Access Reviews
Azure Active Directory (Azure AD) access reviews enable organizations to efficiently manage group memberships, access to enterprise applications, and role assignments. User's access can be reviewed on a regular basis to make sure only the right people have continued access. You can learn more by reading the full Azure Access Reviews technical document.
Entitlement Management
This tool can helps you manage access to groups, applications, and SharePoint Online sites for internal users and also users outside your organization. You can learn more by reading the full Azure Entitlement technical document.
Azure Information Protection: Premium P1 vs P2
The essential difference between these two products is that they both allow you to classify and label data but P1 is a manual process whereas P2 can automatically label and recommend classification, which increases effectiveness of your company policies and gives you more control over your data.
Configure conditions for automatic and recommended classification
Normally you have to manually label documents and emails but with EMS E5 /AIP Premium Plan 2 you can automatically classify all documents and emails or prompt a 'change now' option to override the current classification. For more information, you can read the technical document.

Set labels to automatically apply pre-configured S/MIME protection in Outlook
S/MIME is an encryption protocol based on public key infrastructure that ensures authentication, message integrity, and non-repudiation of origin (using digital signatures) of emails. It is built into Office 365 Message Encryption, which is an automated, policy-based encryption service based on Transport Layer Security/Secure Sockets Layer (TLS/SSL), Internet Protocol Security (IPSec), and Advanced Encryption Standard (AES). This service allows for an addition level of granular configuration. For more information, read the Microsoft technical document.
Control oversharing of information when using Outlook (warn, justify or block emails)
This feature pairs well with Office 365 Data Loss Prevention (DLP) to help prevent the oversharing of sensitive company data by educating your users with interactive pop-up messaging.
For example, John Doe in your company needs the company credit card to buy food for the company lunch so he asks Finance for the information. So Finance responds to John with the credit card number and security code, and then clicks send. When they click send the message below pops up as Azure detected that credit card data was being sent.

Hold Your Own Key (HYOK)
HYOK is a feature for a very specific use case that users may need if they have on-premise infrastructure, the following is an excerpt from the TechNet blog post:
For the current Active Directory Rights Management Services (AD RMS) users that cannot use a cloud-based key for regulatory or technical reasons, this left them without the Classification capabilities provided by AIP and the collaboration features provided when using a cloud key. Luckily, the amazing AIP product group has come up with a solution that provides customers with a method to allow AIP labels to use AD RMS for protection.
Even for the organizations that use HYOK protection, it is typically suitable for a small number of documents that need to be protected. As guidance, use it only for documents and when they match all the following criteria:
- The content has the highest classification in your organization ("Top Secret") and access is restricted to just a few people
- The content is not shared outside the organization
- The content is only consumed on the internal network
Azure Information Protection scanner for automated classification, labeling, and protection of supported on-premises files
This is obviously the biggest bonus of paying for the Premium P2 license because the user does less work and Azure can do a better job at consistently applying the right labels and classification. This creates a seamless end user experience and doesn't increase the burden of being secure on the end user.
Microsoft Cloud App Security
This tool is a Cloud Access Security Broker (CASB), which is necessary for IT compliance, configuring how your data travels, and for visibility into security threats across Microsoft and 3rd party apps.
The Microsoft technical documents describe the following uses cases for using Microsoft Cloud App Security:
-
Discover and control the use of Shadow IT: Identify the cloud apps, IaaS, and PaaS services used by your organization. Investigate usage patterns, assess the risk levels and business readiness of more than 16,000 SaaS apps against more than 80 risks. Start managing them to ensure security and compliance.
-
Protect your sensitive information anywhere in the cloud: Understand, classify, and protect the exposure of sensitive information at rest. Leverage out-of-the box policies and automated processes to apply controls in real-time across all your cloud apps.
-
Protect against cyberthreats and anomalies: Detect unusual behavior across cloud apps to identify ransomware, compromised users or rogue applications, analyze high-risk usage and remediate automatically to limit the risk to your organization.
-
Assess the compliance of your cloud apps: Assess if your cloud apps meet relevant compliance requirements including regulatory compliance and industry standards. Prevent data leaks to non-compliant apps, and limit access to regulated data.
Azure Advanced Threat Protection
Azure ATP is meant to protect hybrid IT environments by leveraging on-premise infrastructure to identify, detect, and investigate advanced threats, compromised identities, and malicious insider actions directed at your organization. Microsoft technical docs give some of the following examples:
- Monitor users, entity behavior, and activities with learning-based analytics
- Protect user identities and credentials stored in Active Directory
- Identify and investigate suspicious user activities and advanced attacks throughout the kill chain
- Provide clear incident information on a simple timeline for fast triage
Curious how your security stacks up? Take our quick cybersecurity risk calculator quiz (2 minutes) to see.
Prefer a consultation? Schedule a free meeting here: 👇






Leave us a comment!