
Microsoft launched the Enterprise Mobility + Security (EMS) in March 2014, in an effort to transition from 'bolted-on' security to 'built-in' security. It was a huge bet at the time, as EMS was meant to bring enterprise-level security that Fortune 500 companies were using to small and medium businesses (SMBs).
Microsoft EMS is a suite of security products that can be purchased as a standalone product or when purchasing Microsoft 365.
Microsoft EMS Pricing
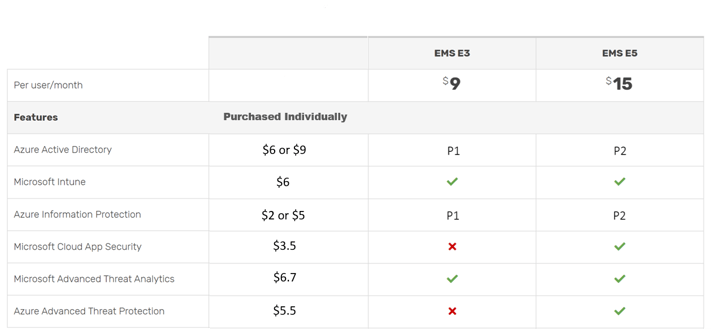
There are two tiers of Enterprise Mobility + Security (EMS) called EMS E3 and EMS E5, which can be bought in four ways:
- EMS E3 can be purchased as a standalone product ($9 per user/month)
- EMS E3 is included in the Microsoft 365 E3 bundle ($32 per month/user)
- EMS E5 can be purchased as a standalone product ($15 per user/month)
- EMS E5 is included in the Microsoft 365 E5 bundle ($57.50 per month/user)
For an in-depth comparison of E3 vs. E5 check out of comparison blog: Microsoft EMS E3 vs. E5
Microsoft EMS Features
The EMS product is made up of six tools, which each have their own features, so we're going to do our best to describe a really complicated product in a short amount of time. In the section below we'll describe what these six tools do in addition to providing a comparison table to see the difference across EMS E3 and EMS E5.
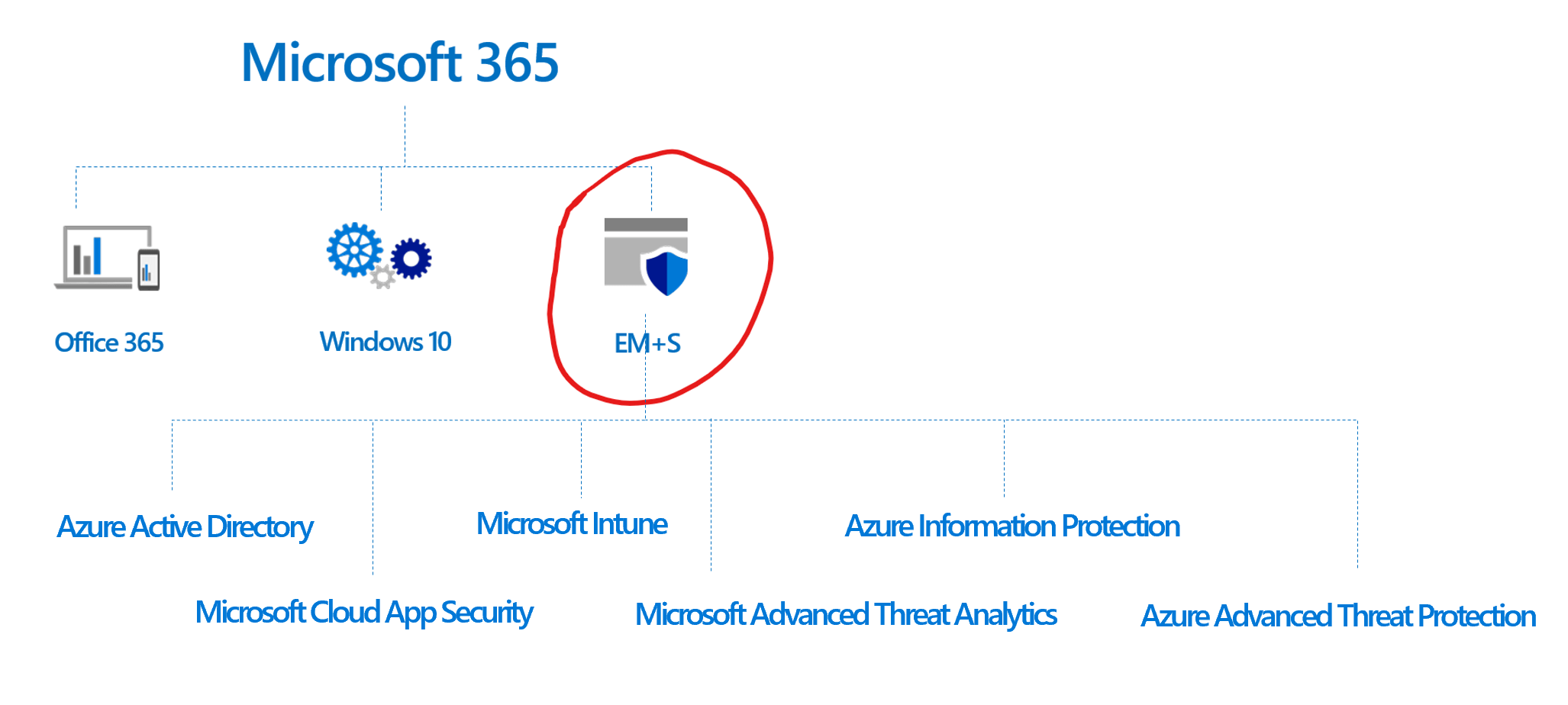
Azure Active Directory
You may not even know you're using Azure AD, it runs in the background of Office 365 and Microsoft 365. It is the technology that manages the identities of all of your users, a.k.a. the thing that checks whether the credentials you wrote are correct or incorrect after you click 'log in' to access an account or an app.
There are two Azure Active Directory licenses sold with EMS. EMS E3 comes with Azure AD Premium P1 and EMS E5 comes with Azure AD Premium P2. Read our Azure AD: Premium P1 v P2 blog post to learn about the specific feature and pricing differences between the two.
Microsoft Intune
Intune allows your company to finally have control over your company's data. With employees bringing their own devices to work, from their smartphones to their own laptops, it's easy to lose control over what is happening with your company data. Are employees saving company files on their laptops? Are your employees keeping their anti-malware up to date or are they streaming illegal movies online that could then affect your company files if malware is downloaded? Intune fixes those types of issues by setting company policies for rules on all devices housing your data.
Some things you can do with Microsoft Intune:
- Manage the mobile devices and PCs your workforce uses to access company data.
- Manage the mobile apps your workforce uses.
- Protect your company information by helping to control the way your workforce accesses and shares it.
- Ensure devices and apps are compliant with company security requirements.
The video above is a quick 15-minute demo of enabling and managing Intune. If you want an extensive walk-through of everything Intune has to offer, then watch the video below of the Ignite 2018 session.
Azure Information Protection
With AIP, you can identity which of your data is sensitive. Microsoft is smart in that it can detect things like credit card numbers and social security numbers within a document. Or you can create custom rules for how to identify sensitive information, so you don't have to read every file you have. Once you've identified the sensitive data, you can classify it by labeling it 'secret' or 'sensitive' or one of the many out of the box labels Microsoft provides you. Then, you can apply protection policies, such as not allowing an employee to copy and paste from certain documents.
Or lets say the CEO accidentally sends an internal memo for the execs to the whole company. Even if the other employees receive the file, they won't be able to read it, unless they have the right credentials. Pretty cool, right? Watch the video below to see it in action.
Microsoft Cloud App Security
This tool is a Cloud Access Security Broker (CASB), which is necessary for IT compliance, configuring how your data travels, and for visibility into security threats across Microsoft and 3rd party apps.
The Microsoft technical documents describe the following uses cases for using Microsoft Cloud App Security:
-
Discover and control the use of Shadow IT: Identify the cloud apps, IaaS, and PaaS services used by your organization. Investigate usage patterns, assess the risk levels and business readiness of more than 16,000 SaaS apps against more than 80 risks. Start managing them to ensure security and compliance.
-
Protect your sensitive information anywhere in the cloud: Understand, classify, and protect the exposure of sensitive information at rest. Leverage out-of-the box policies and automated processes to apply controls in real-time across all your cloud apps.
-
Protect against cyberthreats and anomalies: Detect unusual behavior across cloud apps to identify ransomware, compromised users or rogue applications, analyze high-risk usage and remediate automatically to limit the risk to your organization.
-
Assess the compliance of your cloud apps: Assess if your cloud apps meet relevant compliance requirements including regulatory compliance and industry standards. Prevent data leaks to non-compliant apps, and limit access to regulated data.
Microsoft Advanced Threat Analytics
This is an on-premises platform that helps protect enterprises from advanced cyber-attacks and insider threat by leveraging port mirroring from domain controllers and DNS servers and through deploying the ATA Lightweight Gateway on top of your domain controller.
Azure Advanced Threat Protection
Azure ATP is meant to protect hybrid IT environments by leveraging on-premise infrastructure to identify, detect, and investigate advanced threats, compromised identities, and malicious insider actions directed at your organization. Microsoft technical docs give some of the following examples:
- Monitor users, entity behavior, and activities with learning-based analytics
- Protect user identities and credentials stored in Active Directory
- Identify and investigate suspicious user activities and advanced attacks throughout the kill chain
- Provide clear incident information on a simple timeline for fast triage
Now that you know everything about the common features of Microsoft 365 E3 and E5, it's time to dig into their differences. Dig in with our follow-up blog: Microsoft EMS E3 vs. E5
Still have questions? Schedule a complimentary consult below:
Top 10 Posts
-
Google Workspace to Office 365 Migration: A Step-by-Step Guide
-
Office 365 MFA Setup: Step-by-Step Instructions
-
How to Migrate from GoDaddy to Office 365
-
Migrate From Gmail to Office 365: 2024 Guide
-
CMMC Meaning : A Comprehensive Guide for Startups
-
How to remove Office 365 from GoDaddy (tips and tricks)
-
What is Microsoft Purview ? Your A to Z Guide to Getting Secure Fast
-
What is The CIA Triad?
-
How to Set Up Office Message Encryption (OME)
-
What are the 4 types of Microsoft Active Directory?


Leave us a comment!