
A successful Zero Trust strategy requires seamless and flexible access to applications, systems, and data while maintaining security for both users and the resources they need to do their jobs. It requires being cloud-ready, starting with identity, and then taking steps that will help secure all areas of your environment. Here's what you need to implement for Azure AD Identity Protection:
- Strengthen your credentials
- Reduce your attack surface area.
- Automate threat response
- Increase awareness
- Enable user self-help
To implement these 17 recommendations, you will need to Azure AD Premium License. Read our other blog post, Azure AD: Premium P1 vs P2 to learn about the differences in pricing and features.

Part 1 - Strengthen Your Credentials
Most security breaches originate from a compromised account with one of a handful of methods such as password spray, breach replay, or phishing. If users in your identity system are using weak passwords and not strengthening them with MFA, it isn’t a matter of if or when you get compromised—just how often you will be compromised
Protect Privileged Accounts with MFA
Attackers who get control of privileged accounts can do tremendous damage, so it's critical to protect these accounts first. Enable and require Azure Multi-Factor Authentication (MFA) for all administrators in your organization using Baseline Protection. If you haven't implemented MFA, do it now! It's that important.
Require Your Organization To Use Strong Authentication
Given the frequency of passwords being guessed, phished, stolen with malware, or reused, it's critical to back the password with strong credentials. In Azure AD B2C you can enforce the standard 'strong' password policy across all users or create a custom rule.
Ban Commonly Attacked Passwords and Turn Off Traditional Complexity and Expiration Rules
Many organizations use conventional complexity (requiring special characters, numbers, uppercase, and lowercase) and password expiration rules. Microsoft's research has shown these policies cause users to choose passwords that are easier to guess.
Microsoft recommends adopting the following modern password policy based on NIST guidance:
- Require passwords have at least eight characters. Longer isn't necessarily better, as they cause users to choose predictable passwords, save passwords in files, or write them down.
- Disable expiration rules, which drive users to easily guessed passwords such as "Spring2019!"
- Disable character-composition requirements and prevent users from choosing commonly attacked passwords, as they cause users to select predictable character substitutions in passwords.
Protect Against Leaked Credentials and Add Resilience Against Outages
If your organization uses a hybrid identity solution with pass-through authentication or federation, then you should enable password hash sync for the following two reasons:
- Users with leaked credentials report in the Azure AD management warns you of username and password pairs, which have been exposed on the "dark web." An incredible volume of passwords is leaked via phishing, malware, and password reuse on third-party sites that are later breached. Microsoft finds many of these leaked credentials and will tell you, in this report, if they match credentials in your organization – but only if you enable password hash sync!
- In the event of an on-premises outage (for example, in a ransomware attack), you'll be able to switch over to using cloud authentication using password hash sync. This backup authentication method will allow you to continue accessing apps configured for authentication with Azure Active Directory, including Office 365. In this case IT staff will not need to resort to personal email accounts to share data until the on-premises outage is resolved.
Implement AD FS Extranet Smart Lockout
Organizations, which configure applications to authenticate directly to Azure AD benefit from Azure AD smart lockout. If you use AD FS in Windows Server 2012R2, implement AD FS extranet lockout protection. If you use AD FS on Windows Server 2016, implement an extranet smart lockout. AD FS Smart Extranet lockout protects against brute force attacks, which target AD FS while preventing users from being locked out in Active Directory.

Part 2 - Reduce Your Attack Surface
Given the pervasiveness of password compromise, minimizing the attack surface in your organization is critical. Eliminating the use of older, less secure protocols, limiting access entry points, and exercising more significant control of administrative access to resources can help reduce the attack surface area. To make life harder for hackers, eliminate using older, less secure protocols, limit access entry points, and exercise more significant control of administrative access to resources.
Block Legacy Authentication
Apps using their own legacy methods to authenticate with Azure AD, and access company data, pose another risk for organizations. Examples of apps using legacy authentication are POP3, IMAP4, or SMTP clients. Legacy authentication apps authenticate on behalf of the user and prevent Azure AD from doing advanced security evaluations. Modern authentication will reduce your security risk because it supports multi-factor authentication and Conditional Access. We recommend the following three actions:
- Block legacy authentication if you use AD FS.
- Setup SharePoint Online and Exchange Online to use modern authentication.
- Use Conditional Access policies to block legacy authentication.
Block Invalid Authentication Entry Points
Using the 'assume breach' mentality, you should reduce the impact of compromised user credentials when they happen. For each app in your environment, consider the valid use cases: which groups, which networks, which devices and other elements are authorized – then block the rest. With Azure AD Conditional Access, you can control how authorized users access their apps and resources based on specific conditions you define.
Block End-User Consent
By default, all users in Azure AD are allowed to grant applications that leverage OAuth 2.0 and the Microsoft identity consent framework permissions to access company data. While consenting does enable users to easily acquire useful applications that integrate with Microsoft 365 and Azure, it can represent a risk if not used and monitored carefully. Disabling all future user consent operations can help reduce your surface area and mitigate this risk. If an end-user consent is disabled, previous consent grants will still be honored, but all future consent operations must be performed by an administrator. Before disabling this functionality it is recommended to ensure that users will understand how to request admin approval for new applications; doing this should help reduce user friction, minimize support volume, and make sure users do not sign up for applications using non-Azure AD credentials.
Implement Azure AD Privileged Identity Management
Another impact of "assume breach" is the need to minimize the likelihood a compromised account can operate with a privileged role.
Azure AD Privileged Identity Management (PIM) helps you minimized account privileges by helping you:
- Identify and manage users assigned to administrative roles.
- Understand unused or excessive privilege roles you should remove.
- Establish rules to make sure privileged roles are protected by multi-factor authentication.
- Establish rules to make sure privileged roles are granted only long enough to accomplish the privileged task.
Enable Azure AD PIM, then view the users who are assigned administrative roles and remove unnecessary accounts in those roles. For remaining privileged users, move them from permanent to eligible. Finally, establish appropriate policies to make sure when they need to gain access to those privileged roles, they can do so securely, with the necessary change control.
As part of deploying your privileged account process, follow the best practice to create at least two emergency accounts to make sure you have access to Azure AD if you lock yourself out.
Part 3 - Automate Threat Response
Azure Active Directory has many capabilities that automatically intercept attacks to remove the latency between detection and response. You can reduce the costs and risks when you reduce the time criminals use to embed themselves into your environment. Here are the concrete steps you can take.
Implement User Risk Security Policy Using Azure AD Identity Protection
User risk indicates the likelihood a user's identity has been compromised and is calculated based on the user's risk detections that are associated with a user's identity. A user risk policy is a Conditional Access policy that evaluates the risk level to a specific user or group. Based on Low, Medium, High risk-level, a policy can be configured to block access or require a secure password change using multi-factor authentication. Microsoft's recommendation is to request a secure password change for users at high risk.
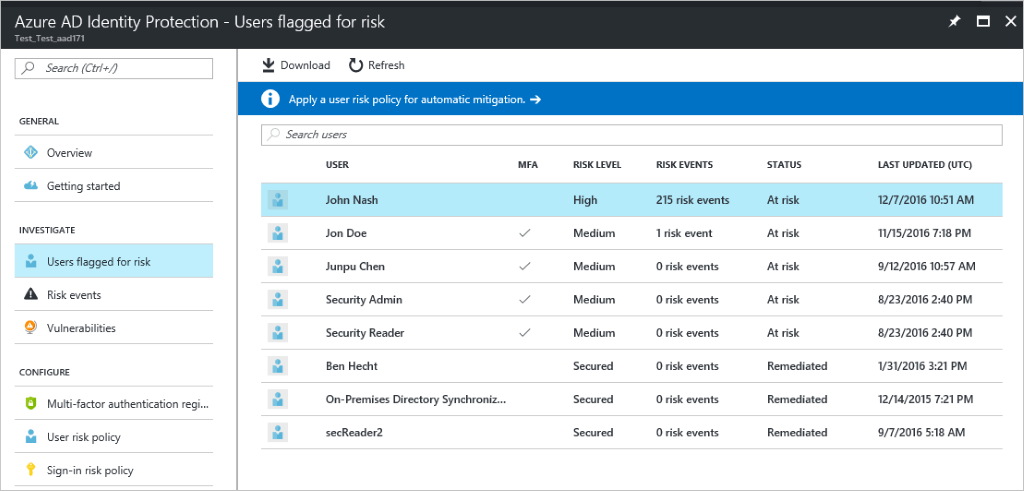
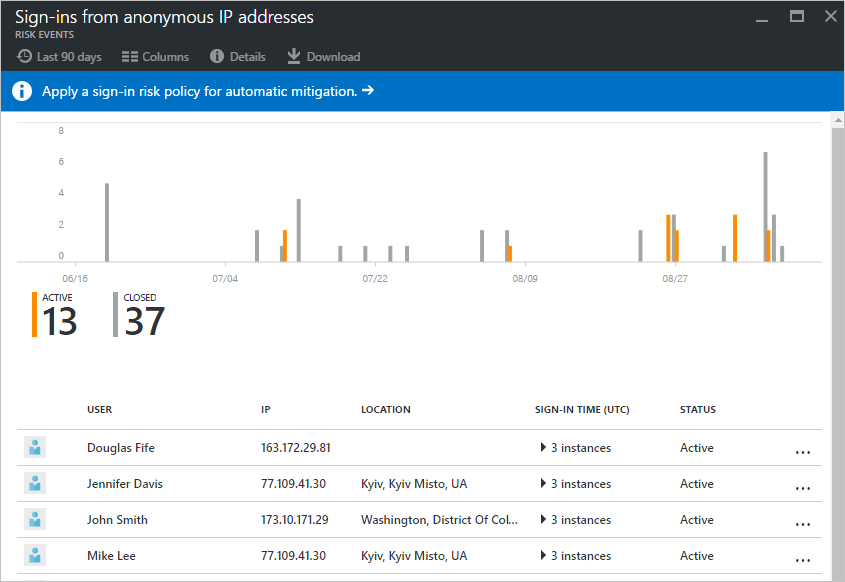
Sign-in risk is the likelihood someone other than the account owner is attempting to sign on using the identity. A sign-in risk policy is a Conditional Access policy that evaluates the risk level to a specific user or group. Based on the risk level (high/medium/low), a policy can be configured to block access or force multi-factor authentication. Make sure you force multi-factor authentication on Medium or above risk sign-ins.
Part 4 - Increase Awareness
Auditing and logging of security-related events and related alerts are essential components of an efficient protection strategy. Security logs and reports provide you with an electronic record of suspicious activities and help you detect patterns that may indicate attempted or successful external penetration of the network, and internal attacks. You can use auditing to monitor user activity, document regulatory compliance, perform forensic analysis, and more. Alerts provide notifications of security events.
Monitor Azure AD
Microsoft Azure services and features provide you with configurable security auditing and logging options to help you identify gaps in your security policies and mechanisms and address those gaps to help prevent breaches. You can use Azure Logging and Auditing and use Audit activity reports in the Azure Active Directory portal.
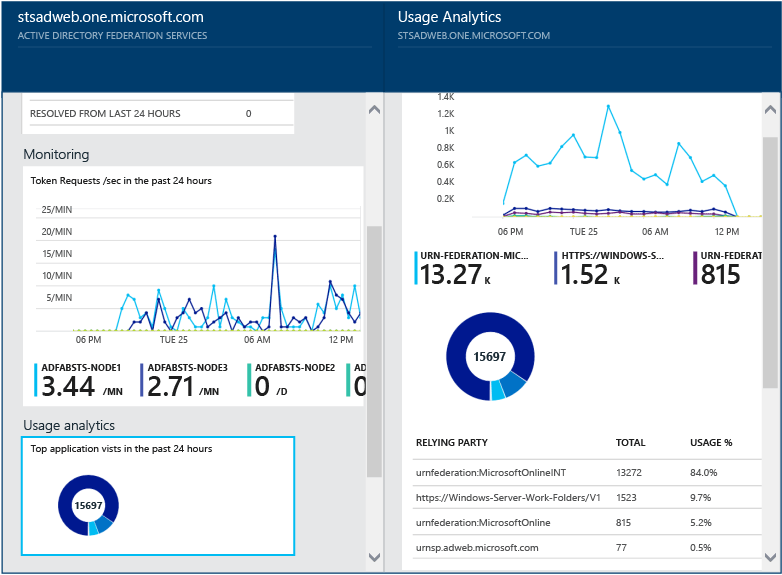
Monitor Azure AD Connect Health in Hybrid Environments
Monitoring AD FS with Azure AD Connect Health provides you with greater insight into potential issues and visibility of attacks on your AD FS infrastructure. Azure AD Connect Health delivers alerts with details, resolution steps, and links to related documentation, usage analytics for several metrics related to authentication traffic, performance monitoring, and reports.
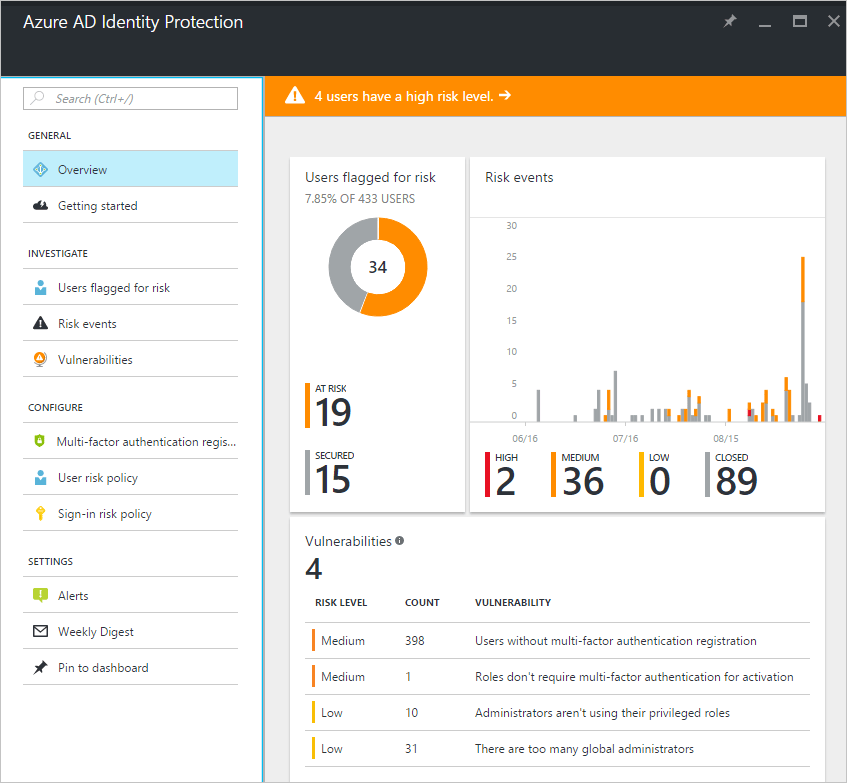
Monitor Azure AD Identity Protection Events
Azure AD Identity Protection is a notification, monitoring, and reporting tool you can use to detect potential vulnerabilities affecting your organization's identities. It identifies risk detections, such as leaked credentials, impossible travel, and sign-ins from infected devices, anonymous IP addresses, IP addresses associated with the suspicious activity, and unknown locations. Enable notification alerts to receive email of users at risk and/or a weekly digest email.
Azure AD Identity Protection provides two crucial reports you should monitor daily:
- Risky sign-in reports will surface user sign-in activities you should investigate, the legitimate owner may not have performed the sign-in.
- Risky user reports will surface user accounts that may have been compromised, such as leaked credential that was detected or the user signed in from different locations, causing an impossible travel event.
Audit Apps and Consented Permissions
Users can be tricked into navigating to a compromised web site or apps that will gain access to their profile information and user data, such as their email. A malicious actor can use the consented permissions it received to encrypt their mailbox content and demand a ransom to regain your mailbox data. Administrators should review and audit the permissions given by users.

Part 5 - Enable End-User Self-Help
As much as possible, you'll want to balance security with productivity. Along the same lines of approaching your journey with the mindset that you're setting a foundation for security in the long run, you can remove friction from your organization by empowering your users while remaining vigilant.
Implement Self-Service Password Reset (SSPR)
Azure's self-service password reset (SSPR) offers a simple means for IT administrators to allow users to reset or unlock their passwords or accounts without administrator intervention. The system includes detailed reporting that tracks when users access the system, along with notifications to alert you to misuse or abuse.
Implement Self-Service Group Management
Azure AD provides the ability to manage access to resources using security groups and Office 365 groups. These groups can be managed by group owners instead of IT administrators. Known as self-service group management, this feature allows group owners who are not assigned an administrative role to create and manage groups without relying on administrators to handle their requests.
Implement Azure AD Access Reviews
With Azure AD access reviews, you can manage group memberships, access to enterprise applications, and privileged role assignments to make sure you maintain a security standard that does not give users access for extended periods when they don't need it.
Don't want to implement it yourself?
Top 10 Posts
-
Google Workspace to Office 365 Migration: A Step-by-Step Guide
-
Office 365 MFA Setup: Step-by-Step Instructions
-
How to Migrate from GoDaddy to Office 365
-
Migrate From Gmail to Office 365: 2024 Guide
-
CMMC Meaning : A Comprehensive Guide for Startups
-
How to remove Office 365 from GoDaddy (tips and tricks)
-
What is Microsoft Purview ? Your A to Z Guide to Getting Secure Fast
-
What is The CIA Triad?
-
How to Set Up Office Message Encryption (OME)
-
What are the 4 types of Microsoft Active Directory?


Leave us a comment!