4 min read
Building a Winning Data Security Defense: Endpoint Security Management
![]() Laura Arce Fonseca
on Apr 27, 2023
Laura Arce Fonseca
on Apr 27, 2023

As an IT Manager or CEO of a small business, you know the importance of protecting your company's data from potential threats. Managing machines and endpoints that access your data can be a challenging task.
That's why, even though "IT" stands for "Information Technology," it might as well mean "Incredibly Tricky." With so many moving parts and constantly evolving technology, it can feel like a never-ending game of catch-up.
An endpoint refers to devices such as desktop computers, laptops, smartphones, servers, and other networked devices that interact with the network and communicate with other devices or systems. They act as the point of entry or exit for data packets in a network.
Endpoint management is an important aspect of a comprehensive security defense because cybercriminals target endpoints as they are doorways to corporate data and often vulnerable to attack. By using endpoint management solutions, such as Microsoft Intune, organizations can improve their security posture, enhance their visibility and control over their endpoints, and optimize their IT efficiency and productivity.
In this blog post, we'll be talking about the challenges faced by small and medium-sized businesses when managing devices and endpoints that access their data, as well as the layered security approach provided by Microsoft's Business Premium.
And we'll build a strategy to complete work more efficiently, while maintaining security and a reduced cost.
Before explaining what endpoint security management is and why you should apply it, let's explore small businesses' defense dilemma and how a strong security strategy can keep your data safe from opponents seeking to intercept your valuable assets.
Challenges of Distributed Work
From the red zone to the end zone, safeguarding your team's information is a critical play that requires a solid defense strategy. The challenges of distributed work are numerous, so let’s break these down and devise a game plan to keep your business on the winning side.
Remote and hybrid work has led to a rise in phishing attacks and ransomware, with hackers exploiting vulnerabilities in unsecured networks and unprotected machines.
Why is this happening? Basically, you need to keep in mind that email isn't the only entry point for hackers. Yes, it is the main one, but there are many other doors that you may have opened without even knowing.
Maybe you provide employees company-owned devices and they use their personal phone only to check email, or perhaps you don't have any company-owned devices and everyone uses their own (this is referred to as Bring Your Own Device BYOD).
In addition to security risks, there are also practical difficulties associated with remote work. Employees may struggle to access necessary company data and applications from home, slowing down productivity. IT managers need to ensure that their employees have secure remote access to company resources, while also ensuring that all endpoints are properly protected.
So what's the game plan?
One word: Intune. Intune Endpoint Manager is a cloud-based service that helps organizations manage their devices and applications. It can be compared to a football coach who oversees the performance and security of the players on the field. Intune Endpoint Manager can monitor, update, and protect devices from anywhere, just like a coach can communicate with players using headphones and tablets. Intune Endpoint Manager can also enforce policies and settings on devices, such as requiring passwords or blocking certain apps, similar to how a coach can set rules and strategies for the team
.png?width=661&height=430&name=intune%201%20(1).png)

The Importance of Endpoint Management
When it comes to cybersecurity, businesses need to play offense and defense. And just like in football, the best defense is a good offense. That's where endpoint management comes in.
Endpoint management refers to the process of monitoring and securing the various devices (or endpoints) that employees use to access company data, such as laptops, smartphones, and tablets. Whether they are company-owned devices or personal (BYOD)
For example, employees may use different devices to access company data which may not all be equally secure. Some employees may also use personal devices to access company data or use public Wi-Fi networks, which can also be a security risk.
This brings up two vital players you must put on the field: Mobile Application Management (MAM) and Mobile Device Management (MDM).
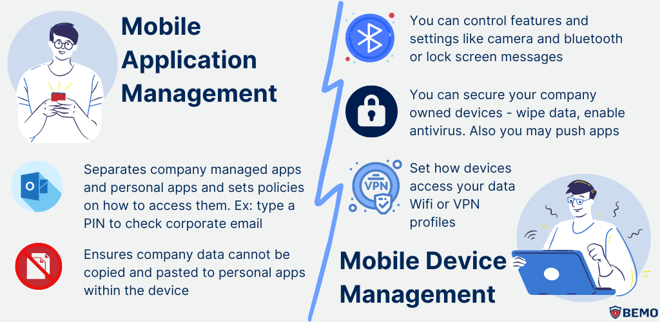
But just like in football, you can't rely on just one play to win the game. That's why a multi-layered security approach that includes endpoint management as well as security measures to protect against cyber attacks, such as firewalls, antivirus software, and intrusion detection systems is essential.
It's like having a whole playbook of defensive strategies to protect your endpoints from cyber criminals. So get in the game and protect your endpoints like a pro - your business will thank you for it.
The Solution: Microsoft 365 Business Premium
When it comes to endpoint management and cybersecurity, small and medium-sized businesses need a champion to lead the charge. Enter Microsoft 365 Business Premium, the MVP (Most Valuable Player) in the game of protecting your company's data.
This all-in-one solution is like a quarterback, directing your team of devices and apps with ease. With Microsoft 365 Business Premium, you get a multi-layered defense that would make even the toughest defense coordinator jealous.
It offers advanced threat protection, like an all-pro linebacker, ready to block phishing attempts and tackle ransomware attacks. And with the power of machine learning, it's always studying the playbook to stay ahead of the game.
You need these tips to level up your cybersecurity game!
.png?width=512&height=800&name=Top%209%20Cybersecurity%20Tips%20for%20SMBs%20(1).png)
But wait, there's more! Microsoft 365 Business Premium also comes with powerful tools for data backup and recovery, as well as collaboration and communication features like Microsoft Teams, OneDrive, and SharePoint. Like a receiver with hands of glue! Making it easy to connect and share with your teammates safely, whether they're in the same city or across the world.
With features such as anti-phishing and anti-ransomware protection, Microsoft 365 Business Premium is a valuable investment for any business looking to protect their sensitive data from cyber-attacks.
And, with pricing plans designed for businesses of all sizes, Microsoft 365 Business Premium is a cost-effective solution for small and medium-sized businesses that may not have the resources for an in-house cybersecurity team.
If you'd like to learn more in-depth about the benefits of Business Premium, make sure to read our blog on it! Alternatively, you may always book a meeting with our team, and we will be happy to address all your questions and find the best fitting package for your business needs. 
Don't settle for a second-string solution when you can have the MVP on your team! With Microsoft 365 Business Premium, you'll be ready to take on any opponent that comes your way and go undefeated.
If you want to learn more on this topic, check out our overview on YouTube:
Top 10 Posts
-
Google Workspace to Office 365 Migration: A Step-by-Step Guide
-
Office 365 MFA Setup: Step-by-Step Instructions
-
How to Migrate from GoDaddy to Office 365
-
Migrate From Gmail to Office 365: 2024 Guide
-
What are the 4 types of Microsoft Active Directory?
-
Windows 10 Enterprise E3 vs E5: What's the Difference?
-
How to remove Office 365 from GoDaddy (tips and tricks)
-
How to Set Up Office Message Encryption (OME)
-
How to Set Up Office 365 Advanced Threat Protection
-
Windows 10 Pro vs Enterprise

Leave us a comment!