
Zero Trust has become a buzzword in recent years, and no, not because dating in 2023 is next to impossible (or so I hear… I’m happily married).
Zero Trust is not an out of the box technology solution, but rather a new way of thinking about security and aligning the way you do security with the way you do business. In this blog, we will explain what Zero Trust is, what are its benefits, and why SMBs should adopt a Zero-Trust security strategy.
What is Zero Trust?
Zero Trust is a security model that assumes that any network, device, app, or user could be compromised and therefore requires verification for every access request.
It is a mindset of “Trust no one and nothing: verify everything.” Zero Trust helps organizations protect their data and resources from cyberattacks by using strong identity and device policies, least-privilege access, and threat protection. It is based on three guiding principles: verify explicitly, use least privilege access, and assume breach. Let’s look at each:
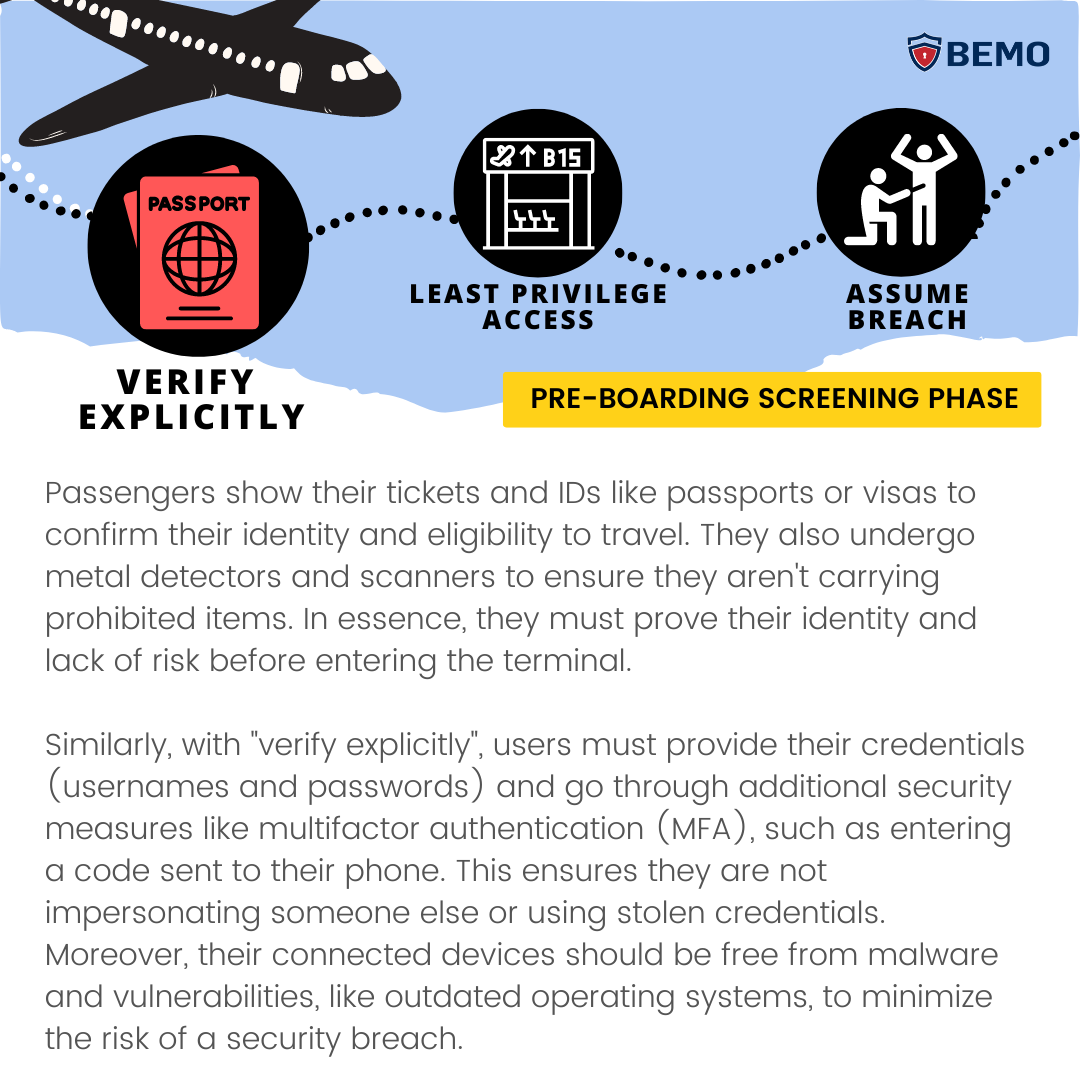
- Verify explicitly: To make your data safer, always check every request to access or use your data. This principle applies to all types of access, whether it is from inside or outside the network, or from trusted or untrusted sources.
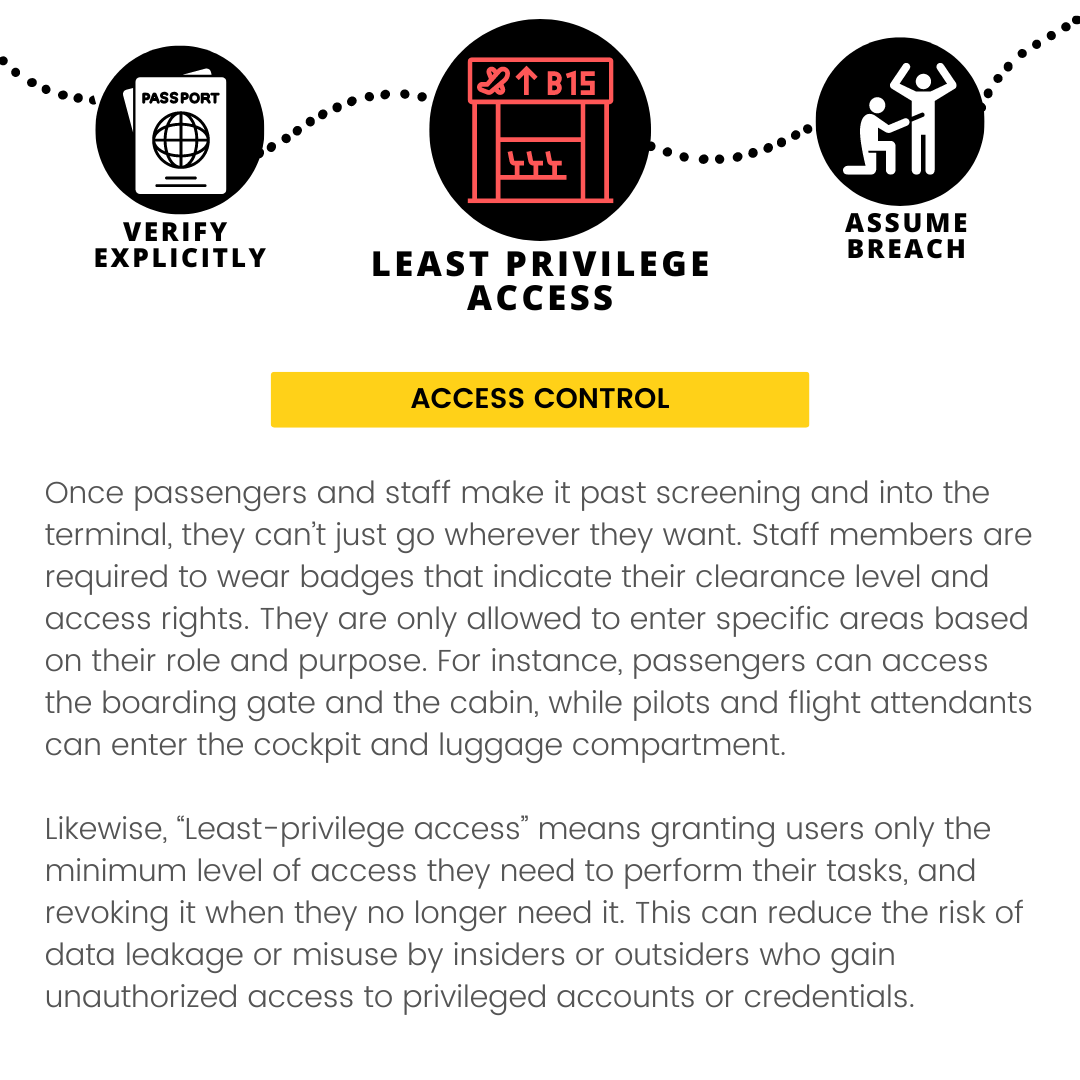
- Use least-privilege access: Users, devices, and services should only have the minimum level of access they need to perform their tasks, and nothing more. This reduces the risk of unauthorized or malicious actions and limits the damage that can be done in case of a breach.
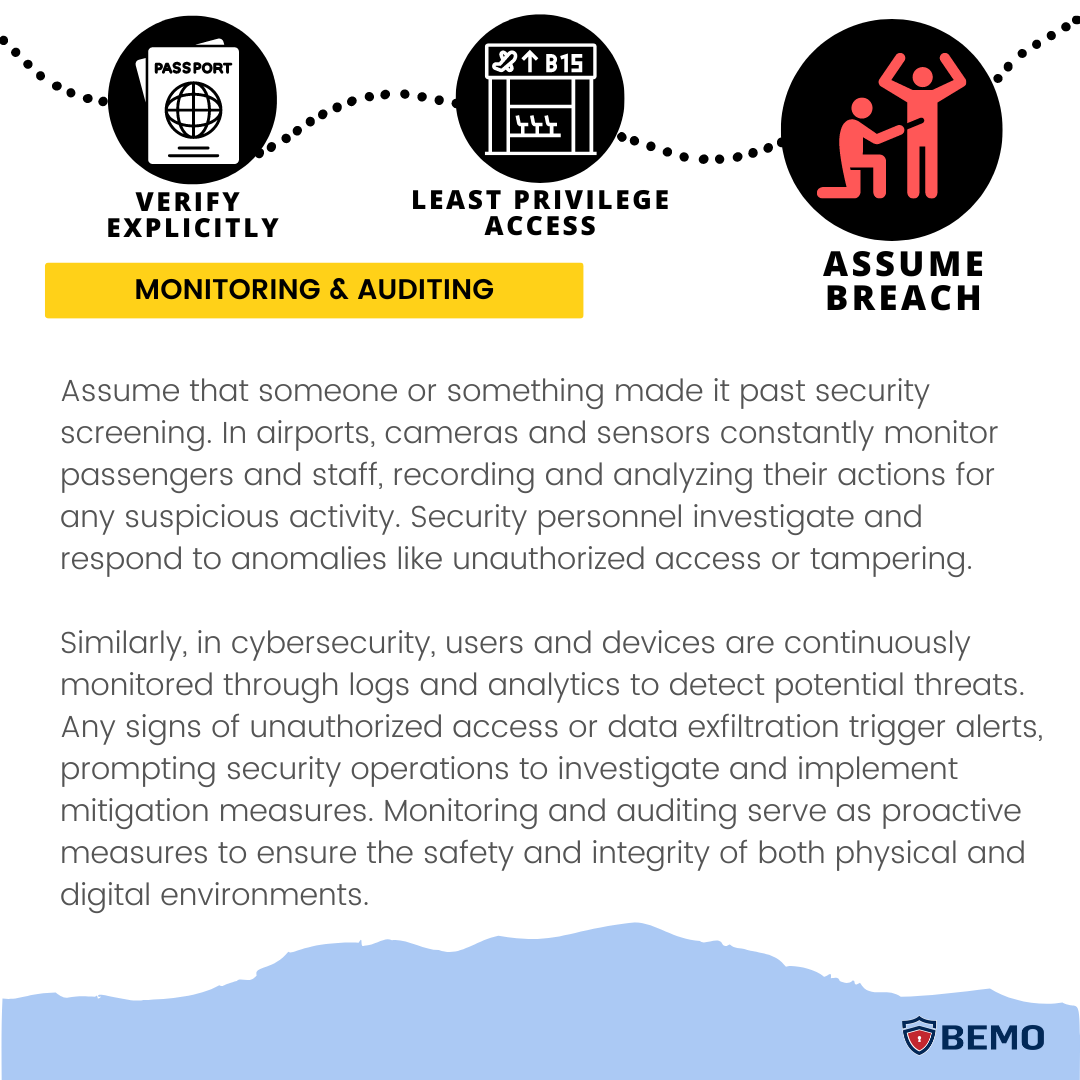
- Assume breach: Always assume an unauthorized person will eventually get access to your data. Be ready with techniques to quickly detect and minimize damage.
Modern threat protection is a critical component of all three areas, enabling organizations to detect attacks and suspicious activity, automatically block and flag risky behavior, take protective actions, and manage the growing amount of threat data.
Zero Trust Made Simple
Security concepts can be a bit overwhelming, so to help you conceptualize the concept of Zero Trust, let’s use an analogy that everyone is familiar with – Airport Security.
Airport security is based on the idea that not everyone who wants to board a plane is trustworthy. Therefore, it applies a series of checks and controls to verify the identity and intentions of the passengers and staff. These include:
Why SMBs Should Adopt Zero Trust.
Maybe you’ve always “flown under the radar” when it comes to your security posture and gotten by just fine, but times are changing.
Prior to the Zero Trust security model coming into the limelight, security models focused on perimeter defenses, an approach that could be compared to placing armed security guards at the outside of the airport, working to keep out dangers while allowing everyone and everything inside the airport to move around freely.
This model assumes that everyone that made it into the airport is trustworthy and nothing bad will happen afterward. We must assume that untrustworthy people might come through an unguarded entry (like other airports), are on the inside already (disgruntled employees), or have made it to the inside through deception of trustworthy people. And, we must have a plan for quick response to minimize the impact if it does happen. The 9/11 attacks drove the change to a new airport security model. The new model goes far beyond just prevention. Aviation security continues to evolve to address ever-changing threats, with a layered approach that involves surveillance, intelligence, and technology.
Likewise, an increase in the number and types of cyberattacks is driving businesses to adopt Zero Trust strategies. The movement towards cloud applications and remote workers connecting to those applications with mobile devices is forcing organizations of all sizes to adopt a Zero Trust strategy to defend their data.
According to a report by Verizon, 28% of data breaches in 2020 involved small businesses, and 22% of SMBs that suffered a cyberattack went out of business as a result. Therefore, SMBs cannot afford to ignore the importance of security and should consider adopting a Zero Trust approach.
.png?width=392&height=392&name=Benefits%20(1).png) By adopting Zero Trust, SMBs can protect their data and reputation from cyber threats and ransomware attacks. They can also improve their compliance with regulations and standards, such as HIPAA, GDPR, and PCI DSS. Zero Trust can also enhance their productivity and efficiency, as they can streamline their workflows and reduce the complexity of their IT infrastructure!.
By adopting Zero Trust, SMBs can protect their data and reputation from cyber threats and ransomware attacks. They can also improve their compliance with regulations and standards, such as HIPAA, GDPR, and PCI DSS. Zero Trust can also enhance their productivity and efficiency, as they can streamline their workflows and reduce the complexity of their IT infrastructure!.
How easily an organization can adopt these principles varies depending on its individual security challenges, needs, and capabilities. In other words, the journey to Zero Trust is unique to your business.
Zero Trust is not a one-time project, but a continuous process that requires constant evaluation and improvement. SMBs should work with trusted partners, like BEMO, that can help them implement and maintain zero trust in their environment.
Don't be shy and contact us if you'd like to implement this security strategy in the most efficient way. 
Zero Trust is the future of cybersecurity, and your SMB should not lag behind!
Want to learn more about how you can keep your business cybersecure?
.png?width=224&height=350&name=Top%209%20Cybersecurity%20Tips%20for%20SMBs%20(1).png)
Top 10 Posts
-
Windows 10 Pro vs Enterprise
-
Migrate From Gmail to Office 365: Step-By-Step Guide
-
Windows 10 Enterprise E3 vs E5: What's the Difference?
-
What are the 4 types of Microsoft Active Directory?
-
How to Migrate from GoDaddy to Office 365
-
Google Workspace to Office 365 Migration: A Step-by-Step Guide
-
How to Set Up Office 365 Advanced Threat Protection
-
10 Benefits of Microsoft Teams
-
Top 3 Reasons to Move From Google Drive to Microsoft OneDrive
-
How to remove Office 365 from GoDaddy (tips and tricks)
-2.png?width=1080&height=1080&name=Untitled%20design%20(5)-2.png)



Leave us a comment!