9 min read
The Future of Passwords is in Your Hands (and Your Eyes, and...)
Domonic Lastoria
on Nov 13, 2020

Today, we use passwords to restrict access to and protect most, if not all, of our electronic computing devices (computers, tablets, cell phones and all remote computing services). Passwords have been a solid standby for...well, forever, but now, we find ourselves moving forward, perhaps towards a password-free society. As we evolve from exceedingly limited connectivity (think snail mail) to the most connected society (think FaceTime, Teams, etc.), so do the technologies that propel us at near-immeasurable speed to get there. Change comes when we eschew the current norms and look toward the future to create a cohesive, cost-effective and seamless authentication experience for all. In this post, we'll discuss the pros and cons of new password approaches, like passphrases and password managers and evaluate the hurdles towards a passwordless future.
Passwords: The Evolution
Remember as a kid having a secret password required of anyone who wanted to enter your fort/club house, etc.? Passwords in computing work very much the same way: they grant you access (though if you're still using the password “banana” from your pillow fort days, please, I implore you, keep reading!).
A password is nothing more than a set of characters which allow a user to access a computer, interface, or system. In essence, a password is the key that opens the door to your data and they've been the access norm for forever...that is, if you can remember them.
Think, Sherlock, think...

Pros and Cons of Passwords
Password authentication systems (think of any site login to that doesn’t require an advanced authentication method, for example, your Twitter account) come from software and are known for being relatively easy to implement. Another pro for passwords as authenticators (keys to data) versus newer authentication mechanisms are their low cost. Since the software handles basic password authentication, the only cost comes from the effort required to implement the program for their specific number of users. Another pro to using passwords is the ease and frequency with which users can change them if they need or want to.
However, there are fundamental problems with passwords, namely, the concept in and of itself is flawed. First, shorter passwords are easy for you to remember, right (think: banana)? But that also makes them easier for hackers to guess.
On the flip side, longer passwords are harder for cyberattackers to crack but more difficult for you to remember (think: 1@!!8vBrTTh*). Since the goal is to keep the information safe, password requirements have increased, both in complexity and length, creating a crazed combination of numbers, letters, and symbols. Password complexities serve to make a password more complicated in order to lock out attackers. However, this comes with the unintended consequences of also locking out the intended user as they fail to memorize the jumbled mess of characters.
The other problem is that, while maybe you’ve finally memorized your wily password, it’s just one of many. One down, one million to go! Just think about how many online accounts you access on the daily. “Aha!” You say, “I found a trick! I only use one complex password that I’ve memorized across all of my platforms. I’m hackproof!” To this we can only reply: 🤦♀️. Using just one or two passwords across the board for all of your online accounts poses a major problem. If attackers figure out your super stealthy password (Banana1!), they will have access to everything. Everything.
Passwords and all the “fun” that come with them aren’t just a problem for you and me. Nowadays, it is not uncommon to hear about your favorite web service or company being attacked after their password database has been compromised, like that Yahoo hack in 2013, Adobe's hack in 2013, or more recently, Facebook gaming giant Zynga last year. This is why technology is evolving from passwords to passphrases and other newer authentication mechanisms.
Passphrases: A Better, More Modern Approach
Since the advent of passwords, we have experienced unfathomable, and unimaginably rapid technical evolution and with this, thankfully, authentication (your key to your data) too has also shifted from total reliance on passwords to the use of passphrases. The simple restructuring of the password concept into passphrases has had a revolutionary effect, most especially in web application security by fixing the issue of unsanitized user input, more commonly known as SQL injection, that has plagued the web security industry for a long time .
Passphrases evolved as the more secure form of passwords. A passphrase is a sequence of words or text used to control access to a computer system, program, or data (think: ILoveBananas! as a very basic interpretation and to continue our theme). It is similar to a password in usage but it is generally longer for added security. All you need do is create a mnemonic or other simple way for you to memorize your passphrase. You can create your own or use a password generator to create one for you. In either circumstance, the likelihood that a hacker could guess said phrase are slim to none, yet are very easy for you to memorize. Just don't choose something commonly said, known or referenced.
Pros and Cons of Passphrases
Passphrases tend to be easier to remember than a random combination of symbols and letters and the use of punctuation and upper and lower cases will help to meet complexity requirements for passwords. Passphrases are next to impossible to crack because most of the highly efficient password cracking tools tend to cap out at around 10 characters.
However, a downside to the use of passphrases is that many internet sites still use fairly short password character limits, essentially eliminating passphrases as an option. Therefore instead of having one secure passphrase that can be used for multiple sites, users may have a passphrase on some sites, but still have to use a less complex password for others, thus, the juggling of passwords and passphrases continues.
Password Managers
OK, I think we can agree that nobody likes passwords but they are not going away anytime soon. Thankfully, we’ve learned to grow with them. Passwords, and their inherent flaws prompted the evolutionary change into the use of password managers. Password Managers are a little like a notebook of passwords locked in a safe by a master code that only you know. Password Managers (our favorite is Keeper) not only store passwords, but they can also help you generate and save strong, unique passwords when you sign up to a new website. When you next visit that site, all you have to do is click your mouse and your manager will automatically enter all of your login info. Hallelujah! No passwords OR usernames to remember!
Some have tried to kill off password managers by replacing them with biometric options like fingerprints and face-scanning technology, however, neither are perfect and when they fail, the default is to request a password. So, even if you're "password free", you really aren't. This is where a password manager comes in extra handy. They immediately recognize the site and provide your password, seamlessly logging you in!
Pros and Cons of Password Managers
Passwords are stolen all the time. Companies are supposed to encrypt (or scramble) your password whenever you enter it, also known as hashing. However, not all companies use strong or modern algorithms. This makes it easy for hackers to reverse that hashing and read your password in plain text. Aside from this, there is the problem with passwords of the sheer number of passwords you must memorize and remember. However, using a password manager avoids all of this for you. There is also the benefit of many password managers are cross-platform which means they also work on mobile devices, allowing you to take your passwords wherever you go.
Sadly, single point failure is a problem with password managers because if someone gets a hold of the master password, they gain access to all the passwords and your various online platforms.
Single Sign-On (SSO)
This is an authentication method that permits a user to use one set of login credentials, for example, a name and password to access multiple applications instead of multiple accounts and passwords. It helps to ease the management of having multiple usernames and passwords. All you do is simply log on with a single ID and password and you immediately have access to any of several related, yet independent software systems. True single sign-on allows the user to log in once and access services without re-entering authentication factors. It also allows websites to use other trustworthy sites to verify users. For example, here at BEMO, SSO allows us to access all our internal platforms like Microsoft 365, Keeper Enterprise, HubSpot, without the need to log into those systems repeatedly. I'm not going to lie, it's pretty amazing.
Pros and Cons of SSO
SSO enables users to have fewer username password combinations to remember for each application and streamlines the process of signing on and using applications. There's no need to reenter passwords. It also lessens the chances of credential phishing attempts being successful due to the additional layer of security that most if not all phishing tools don’t account for when attempting to gain access. IT teams will also cite the added benefit of fewer complaints and trouble with passwords from users.
The downsides to the use of SSO is that it does not address certain levels of security each application sign-on may require. Another issue is when connectivity to the SSO service is lost, users are locked out of the multiple systems connected to the SSO service. Another problem is that if an unauthorized user gains access (say if the that user were to gain access to the means of authentication i.e. phone authenticator), then they could gain access to more than one application. Thankfully, we at BEMO use more than just your run of the mill security to protect our data and our team. Check out a list of our favorite tools to manage a remote team safely and securely.
Passwordless
The notion that passwords should become obsolete has been floating around the IT world since 2004. Bill Gates predicted the demise of passwords at the 2004 RSA Conference saying that they don’t just meet the challenge for anything that you really want to be secure.
Recent technological advancements (e.g. the proliferation of biometric devices and smartphones) and changing business culture (acceptance of biometrics and work from home, for example) is continuously promoting the adoption of passwordless authentication.
Passwordless authentication is an authentication method in which a user can login to a computer system without entering and remembering an account password. The password-less authentication relies on a cryptographic key pair, both a public and a private key.
The public key is provided during registration to the authenticating service while the private key is kept on a user’s device and can only be accessed when a biometric signature, hardware token, or any other passwordless factor is introduced.
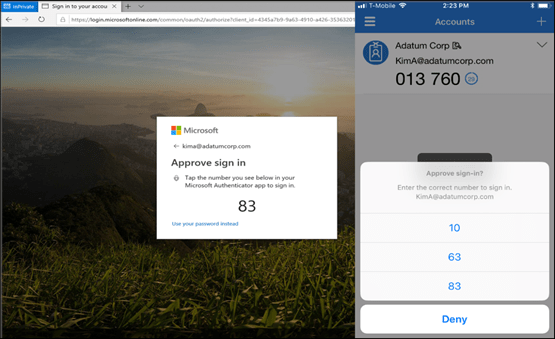
Most commonly, users are asked to enter their public identifiers such as username, mobile phone number, email address, or any other registered ID and then complete the authentication process by providing a secure proof of identity in the form of an accepted authentication factor which could either be an ownership factor or inherence factor.
The ownership factor is ‘something the user possesses daily’ such as a cell phone, OTP token, smartcard, or a hardware token used for “authenticator applications like Microsoft’s Authenticator The inherence factor is ‘something the user is’ like fingerprints, retinal scans, face or voice recognition, and other biometric identifiers.
The Pros and Cons of Passwordless
PROS
Greater security
Passwords are known to be a weak point in electronic systems due to reuse, sharing, cracking, and are a top attack vector responsible for a huge percentage of security breaches.
Better user experience
Not only are the users of passwordless authentication not required to remember complicated passwords and comply with different security policies, but they are also not required to periodically renew passwords.
Reduced IT costs
Since no password storage and management is needed, IT teams are no longer burdened with the setting of password policies, detecting leaks, resetting forgotten passwords, and complying with password storage regulation.
Better visibility of credential use
Since credentials are tied to a specific device or inherent user attribute, they can’t be massively used hence access management becomes tighter.
Scalability
Managing multiple logins without additional password fatigue or complicated registration.
CONS
Implementation costs
Although, in the long run, passwordless authentication saves a good amount cost however, deployment costs and lack of security IT knowledge are currently a hindering factor for many potential users. Cost is associated with the need to deploy an authentication mechanism on an existing user directory and sometimes the additional hardware deployed to users.
Training and expertise needed
While most password management systems are built about the same, and have been used for many years, passwordless authentication requires adaptation from both IT teams and end-users.
Single point of failure
Particularly, implementations using OTP or push notifications to cellular device applications can create a challenge for the end-user if a device is broken, lost, stolen, or simply upgraded.
The Future of Passwords
It has become clear for a while now that passwords no longer provide the user experience or security needed for the people of today. While the majority of us are familiar with biometric authentication options like fingerprint or facial recognition methods, the latest advances in authentication will see our most intricate behavioral characteristics like typing patterns, location, and occupation used to verify our identity and protect our personal information. These new technologies will allow you to log into your applications without needing to do anything at all. Wow. Just wow.
Zero Login
It may surprise you to learn that zero login is already in use out there today. If you’ve logged in to your online banking from a new device or connected from a café that you’ve never been to before, you may have received a message or call from your bank asking you to verify your email or phone number to prove it’s really you.
Amazon.com is currently testing behavioral characteristics including the pressure applied when a user taps their phone as well as typing speed as vectors for verifying a user’s identity. Such intricate and unique patterns would be near impossible for a potential attacker to guess or replicate.
A zero login world would see passwords as the last line of defense and only attackers, ideally, would ever be asked to enter one. Today, many applications and online stores will ask for a password even though the chance of that transaction being fraudulent is extremely low. The days of passwords on passwords on passwords are about to change. Authentication is about to be redefined as we know it.
The Wrap Up
While remembering numerous complex passwords will soon fall under the umbrella of ‘the old ways” and phones will soon be able to recognize us from the moment we pick up the device, there's still some things to be figured out before we zoom over to Zero login. The technology is smart but people’s privacy and consent must be prioritized if we are to successfully construct a new era of authentication. Until then, I hope this guide has provided you a little more insight into how to safely and securely use passwords. Now, go change those Banana1!-esque passwords...now!
Did you enjoy this blog? Let us know in the comments below or use the social share buttons to spread the word to your networks 🙌
Curious how your company's security stacks up? Take our cybersecurity quiz here:
Don't miss the next installment of IT goodness, sign up to receive the blog weekly in your inbox 📮
Top 10 Posts
-
Windows 10 Pro vs Enterprise
-
Migrate From Gmail to Office 365: Step-By-Step Guide
-
Windows 10 Enterprise E3 vs E5: What's the Difference?
-
What are the 4 types of Microsoft Active Directory?
-
How to Migrate from GoDaddy to Office 365
-
Google Workspace to Office 365 Migration: A Step-by-Step Guide
-
How to Set Up Office 365 Advanced Threat Protection
-
10 Benefits of Microsoft Teams
-
Top 3 Reasons to Move From Google Drive to Microsoft OneDrive
-
How to remove Office 365 from GoDaddy (tips and tricks)
-2.png?width=1080&height=1080&name=Untitled%20design%20(5)-2.png)



Leave us a comment!